Quickly check the Dark Web for your leaked credentials… without checking the Dark Web
Ever wonder if your most used username and password is floating out there in the dark web, but don’t want to install a Tor browser, start visiting questionable underground websites, downloading data dumps by hacking groups and spending hours running queries to find your username and password present in these databases?
You are in luck because Google did all the hard legwork for you. Chrome is a popular browser that has a fairly robust password wallet built into it. So if you are in fact using Chrome, your passwords are saved and synced across all devices.
- Go to passwords.google.com
- Select Go to Password Checkup
- Check passwords. You might need to sign in.
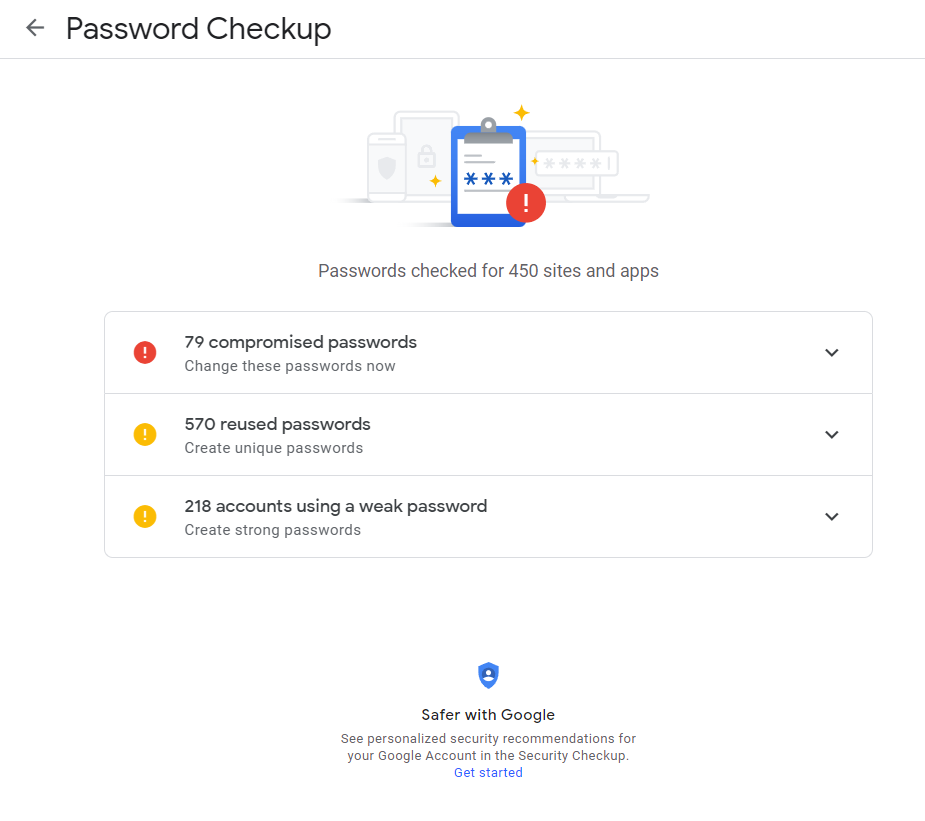
Expand the first row that has compromised passwords.
Odds are you will have plenty in there as well. Address the initial compromised passwords. You will be surprised, but for me large websites like alibaba.com, booking.com, dominos.com, ebates.com, jet.com, meetup.com, photobucket showed up as compromised passwords. This means that data has leaked from these websites and was picked up by hackers on the dark web.
Those are just some of them!
If you’re using Chrome as your password wallet, this is certainly an easy way to check if your password and usernames have been compromised.
If you are wondering why would I care about some of those websites, you might not use them anyways. Well, check out this article to better understand how hackers can take advantage of these usernames/passwords to bypass 2FA you might have on your bank or Office 365 or GoDaddy accounts.
Unfortunately threats come from every direction and these same passwords that you have compromised could be the same ones that you use for your VPN connection, login into your computer etc. I always say that hackers have all the time in the world to come up with exploits while you have a day job, kids to take care of and other priorities to worry about. Security is just a tiny fraction of what you spend your energy on during the day, while bad actors spend 100% of their time trying to exploit this.
How can you protect your business from cyberthreats?
This is why I always tell our clients to fully utilize the full featured security suite instead of just the antivirus. Back in the golden day if you had the AV program installed you could basically claim that you are protected. Rarely would infections get in and the AV would quickly patch those. Attacks now days are way more intricate than an annoying pop up advertisement on your computer that slowed your systems down.
For example, just recently an exploit was found that does not rely on a cobalt launcher or any C2 framework in order to infiltrate the entire network using an unpatched Microsoft Exchange Server. This attack relies on using all open source or off the shelf built-in command lines used by admins to manage Exchange servers. They encrypt all data using built in BitLocker for the servers and DiskCryptor on the workstations. If you are unaware of this attack happening or have safeguards in place that can stop it from fully executing and sounding red flags, by the time you discover that you have been hacked, it’s too late.
This is why we incorporate automated prevention of advanced attacks to avoid potential data breaches. Utilizing machine learning stops advanced attacks at pre-execution. Our security solutions analyze command code in memory of the endpoint and prevent script based attacks from executing. This combined with an antivirus solution allows us to detect and prevent most intrusions. However, as we all know, no one is fully safe. That’s why it’s always important to think ahead and make sure your backups are safeguarded with additional authentication and ensure that you have a plan in place in case something like this happens to your systems.
If you need assistance determining whether your security systems are up to snuff or if you need a business security solution, AlphaCIS can assist. We are based in Atlanta’s Metro area and provide full managed services as well as security solutions. If you’re not sure if your company’s security is up to par, ask us to do a security audit of your system.

Dmitriy Teplinskiy
I have worked in the IT industry for 15+ years. During this time I have consulted clients in accounting and finance, manufacturing, automotive and boating, retail and everything in between. My background is in Networking and Cybersecurity



