Article Summary
• Who this is for: Manufacturing executives, plant managers, and operations leaders responsible for protecting production, intellectual property, and uptime
• The challenge: Manufacturers face high downtime costs, IT/OT security gaps, and supply chain vulnerabilities that make them prime targets for ransomware and industrial cyberattacks
• Key insights covered: Why factory ransomware is so profitable for attackers, the risks of IT and OT convergence, ICS security weaknesses, supply chain attack paths, and practical segmentation and monitoring strategies
• Your outcome: A clear understanding of your manufacturing cybersecurity risk—and actionable steps to protect production systems, reduce downtime exposure, and strengthen long-term operational resilience
Key Takeaways
• Manufacturing companies face unique cybersecurity vulnerabilities due to their reliance on operational technology (OT) systems and low tolerance for downtime
• The convergence of IT and OT networks creates new attack vectors that cybercriminals actively exploit for maximum financial gain
• Factory ransomware attacks can cost manufacturers millions per hour in lost production, making them prime targets for high-value extortion
• Supply chain cyber threats amplify risks as attackers use manufacturing partners as entry points to larger networks
• Implementing proper OT vs IT security segmentation and proactive monitoring can significantly reduce industrial cybersecurity risks
Ready to Take IT Off Your Plate?
Stop worrying about downtime, security risks, or endless IT frustrations. AlphaCIS is the trusted IT partner for small and mid-sized businesses in Metro Atlanta, keeping systems secure, connected, and running the way they should every day.
Whether it’s preventing costly outages, protecting your data, or giving your team unlimited support, we make sure technology helps your business grow instead of holding it back.
📅 Book Your Free ConsultationQuick Answer

Manufacturing companies are primary targets for cybercriminals because they operate critical infrastructure with minimal downtime tolerance, often pay ransoms quickly to restore production, and typically have weaker cybersecurity for manufacturing companies compared to other industries. The integration of legacy operational technology with modern IT systems creates numerous vulnerabilities that attackers exploit for maximum financial impact.
Why Manufacturing Companies Are Prime Targets for Cyberattacks
Manufacturing companies represent the perfect storm for cybercriminals seeking maximum return on their malicious investments. Unlike other industries that can absorb some operational disruption, manufacturers face immediate and catastrophic financial losses when production stops.
The numbers tell a stark story. When a manufacturing facility goes down due to a cyberattack, companies lose an average of $50,000 to $2 million per hour, depending on their industry segment. This creates enormous pressure to pay ransoms quickly rather than endure extended downtime while systems are rebuilt from scratch.
What makes manufacturers especially vulnerable:
- Legacy operational technology that wasn’t designed with cybersecurity in mind
- Interconnected supply chains that create multiple entry points for attackers
- Limited cybersecurity budgets compared to financial services or healthcare
- Skilled workforce shortages in both manufacturing and cybersecurity roles
- Compliance gaps between IT security standards and OT operational requirements
I’ve seen firsthand how a single ransomware attack can shut down an entire automotive parts supplier for days, creating ripple effects throughout their customer base. The urgency to restore production often overrides security considerations, leading to hasty decisions that can compound the original problem.
The reality is that cybercriminals have studied manufacturing operations extensively. They understand production schedules, peak seasons, and the financial pressure points that make manufacturers more likely to pay ransoms rather than fight prolonged recovery battles.
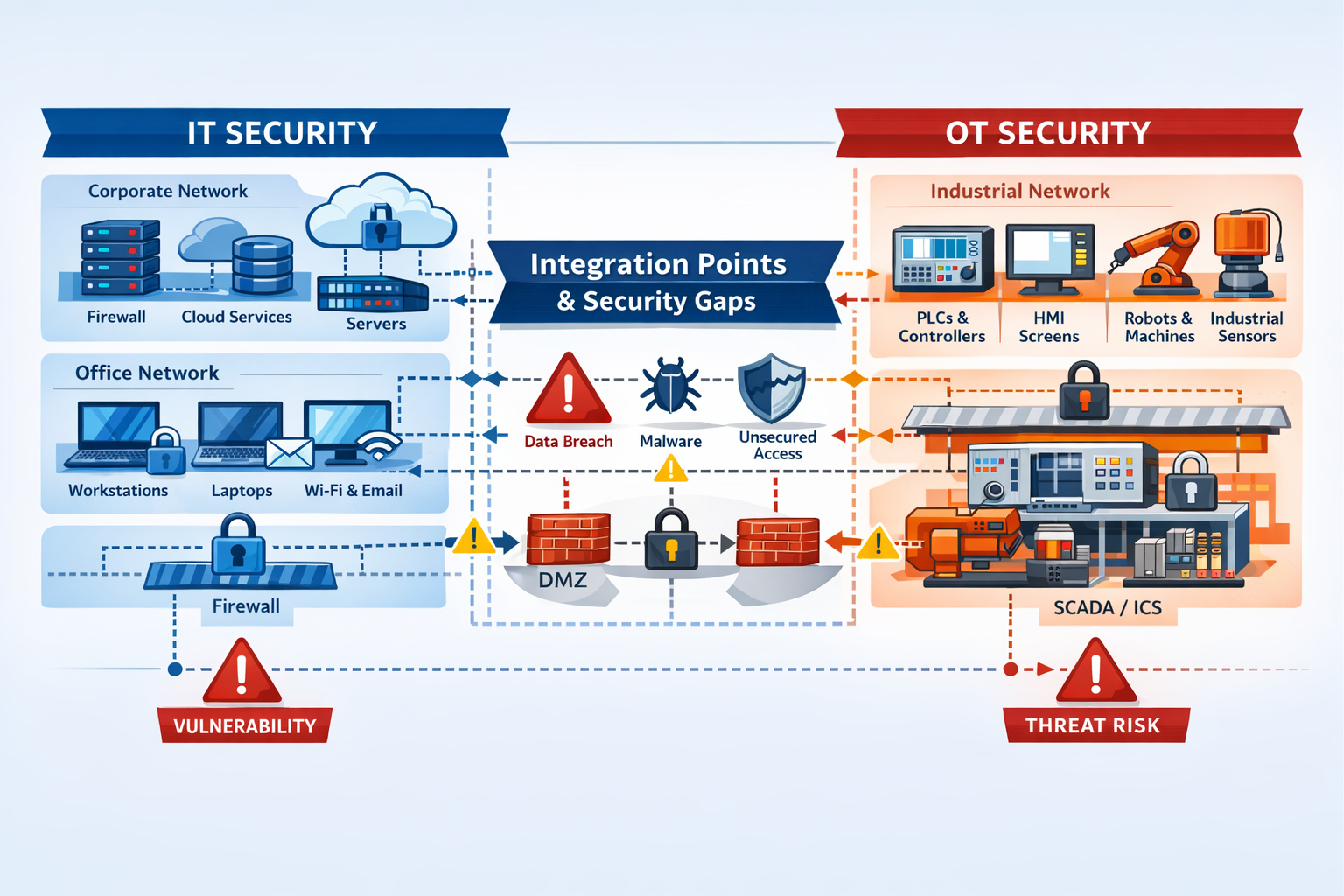
The Critical Difference: OT vs IT Security in Manufacturing
The fundamental challenge facing manufacturing companies lies in the collision between two very different technology worlds: information technology (IT) and operational technology (OT). This convergence has created a security nightmare that many manufacturers are still struggling to address.
Traditional IT systems were built with connectivity and data sharing in mind. They expect regular updates, patches, and security modifications. Operational technology, however, was designed for reliability, safety, and continuous operation, often running for decades without significant changes.
Key differences that create vulnerabilities:
IT Systems:
- Regular security updates and patches
- Built-in authentication and access controls
- Designed for network connectivity
- Shorter replacement cycles (3-5 years)
OT Systems:
- Infrequent updates due to uptime requirements
- Often lack basic authentication features
- Originally designed for isolated networks
- Extended lifecycles (15-25 years)
The problem intensifies when companies connect these systems for operational efficiency without properly securing the integration points. A vulnerability in an industrial control system (ICS) can provide attackers with direct access to production equipment, safety systems, and quality controls.
One manufacturing client we worked with discovered their programmable logic controllers (PLCs) were accessible from the corporate network with default passwords that hadn’t been changed in over a decade. This is unfortunately common; many OT devices still ship with default credentials and limited security features.
Common OT security gaps include:
- Unencrypted communications between devices
- Shared service accounts across multiple systems
- Direct connections between corporate networks and production floors
- Insufficient monitoring of the OT network traffic
- Lack of asset inventory for connected industrial devices
The solution isn’t to keep these systems completely isolated. Modern manufacturing requires data integration for efficiency and competitiveness. Instead, manufacturers need proper network segmentation, monitoring, and security controls designed specifically for industrial environments.
Supply Chain Cyber Threats: The Domino Effect
Manufacturing companies don’t operate in isolation; they’re part of complex supply chains that can span continents and involve hundreds of partners. This interconnectedness, while essential for modern production, creates a massive attack surface that cybercriminals actively exploit.
Supply chain attacks work by targeting the weakest link in the network. Attackers might compromise a small supplier with limited cybersecurity resources, then use that access to move laterally into larger manufacturing partners or customers.
How supply chain attacks typically unfold:
- Initial compromise of a smaller supplier or vendor
- Lateral movement through shared systems or trusted connections
- Privilege escalation within the target manufacturer’s network
- Data exfiltration or ransomware deployment across multiple organizations
The 2020 SolarWinds attack demonstrated how software supply chain compromises can affect thousands of organizations simultaneously. In manufacturing, similar attacks can propagate through vendor portals, shared engineering systems, or integrated logistics platforms.
Common supply chain vulnerabilities:
- Vendor remote access without proper monitoring or time limits
- Shared file systems for engineering drawings or specifications
- Integrated logistics platforms connecting multiple supply chain partners
- Third-party software embedded in manufacturing equipment
- Cloud services shared across multiple organizations
One automotive manufacturer we assisted had unknowingly provided network access to over 200 suppliers through various integration points. When one supplier was compromised, the attackers had potential access to production schedules, inventory levels, and customer data across the entire supply chain.
Protecting against supply chain threats requires:
- Vendor risk assessments that include cybersecurity evaluations
- Network segmentation that isolates supplier access to specific systems
- Continuous monitoring of third-party connections and data flows
- Incident response coordination with key supply chain partners
- Regular security audits of integrated systems and shared platforms
The goal isn’t to eliminate supply chain connectivity that would cripple modern manufacturing. Instead, manufacturers need visibility into their extended network and controls that can contain threats before they spread throughout the ecosystem.
Manufacturing Data Breaches: Beyond Production Disruption
While operational downtime grabs headlines, manufacturing data breaches can cause equally devastating long-term damage. Manufacturing companies possess valuable intellectual property, customer data, and operational intelligence that cybercriminals can monetize in multiple ways.
Types of valuable data targeted in manufacturing:
- Product designs and engineering specifications are worth millions in R&D investment
- Customer lists and pricing information that competitors would pay for
- Production processes and trade secrets that provide competitive advantages
- Financial data, including costs, margins, and strategic planning information
- Employee personal information for identity theft or additional attacks
The theft of intellectual property represents a particularly insidious threat. Unlike ransomware attacks that are immediately obvious, IP theft can go undetected for months or years while competitors gain unfair advantages or foreign adversaries build competing capabilities.
I worked with a precision manufacturing company that discovered competitors were bidding on contracts with suspiciously detailed knowledge of their proprietary processes. Investigation revealed that their engineering files had been accessed and copied over 18 months through a compromised vendor connection.
Common data exfiltration methods include:
- Insider threats from employees with legitimate access to sensitive information
- Compromised credentials that provide ongoing access to file systems
- Network infiltration through vulnerable industrial systems or vendor connections
- Cloud storage breaches where backup data lacks proper protection
- Email phishing targeting engineers, executives, or procurement staff
The financial impact extends beyond immediate costs:
- Lost competitive advantage from stolen IP
- Customer contract penalties for data exposure
- Regulatory fines for privacy violations
- Legal costs for litigation and investigation
- Reputation damage affecting future business opportunities
Protecting manufacturing data requires:
- Data classification to identify and prioritize the protection of sensitive information
- Access controls that limit data exposure based on job requirements
- Encryption for data at rest and in transit, especially for cloud storage
- Activity monitoring to detect unusual access patterns or data transfers
- Regular backups with offline copies that can’t be compromised by ransomware
The key is understanding that manufacturing cybersecurity isn’t just about keeping production lines running; it’s about protecting the intellectual capital that drives long-term competitiveness and profitability.
Operational Downtime Cyberattacks: The Million-Dollar Hour
Nothing focuses a manufacturing executive’s attention like watching production lines grind to a halt while costs accumulate by the minute. Operational downtime from cyberattacks represents the most immediate and quantifiable threat facing manufacturers today.
The financial mathematics is brutal. A mid-sized automotive parts manufacturer might lose $100,000 per hour when their injection molding lines stop. A pharmaceutical company could face $2 million per hour in lost production during peak demand periods. These numbers don’t include the cascading costs of missed deliveries, penalty payments, or emergency overtime to catch up.
Direct costs of operational downtime include:
- Lost production revenue calculated per hour or per unit
- Fixed costs that continue regardless of production status
- Emergency response expenses for incident investigation and recovery
- Overtime payments to make up for lost production time
- Customer penalties for missed delivery commitments
Indirect costs often exceed direct losses:
- Customer relationship damage from unreliable delivery performance
- Market share loss to competitors who can fulfill orders
- Insurance premium increases following security incidents
- Regulatory scrutiny that can slow future operations
- Employee productivity loss during extended recovery periods
I remember working with a food processing company that lost $50,000 worth of product in addition to production downtime when a ransomware attack disabled their refrigeration monitoring systems. The spoiled inventory represented weeks of production that couldn’t be recovered.
Why manufacturing downtime is particularly devastating:
Manufacturing operations are built on just-in-time principles with minimal buffer inventory. When production stops, there’s usually no stockpile to draw from while systems are restored. Customer commitments become impossible to meet, and the financial pressure mounts exponentially.
Factors that increase downtime duration:
- Lack of offline backups that can be quickly restored
- Integrated systems where one compromised component affects the entire production line
- Limited incident response planning specific to manufacturing environments
- Dependency on specialized software that may take days to rebuild or replace
- Regulatory requirements that prevent resuming production until safety systems are verified
Minimizing downtime requires:
- Rapid detection through 24/7 monitoring of both IT and OT systems
- Incident response procedures tested specifically for manufacturing scenarios
- Backup systems that can maintain critical safety and production functions
- Recovery prioritization that focuses on the highest-value production lines first
- Communication plans that keep customers and suppliers informed during incidents
The goal isn’t just preventing attacks, it’s ensuring that when incidents occur, recovery happens as quickly and safely as possible. Every minute of downtime avoided translates directly to preserved revenue and maintained customer relationships.
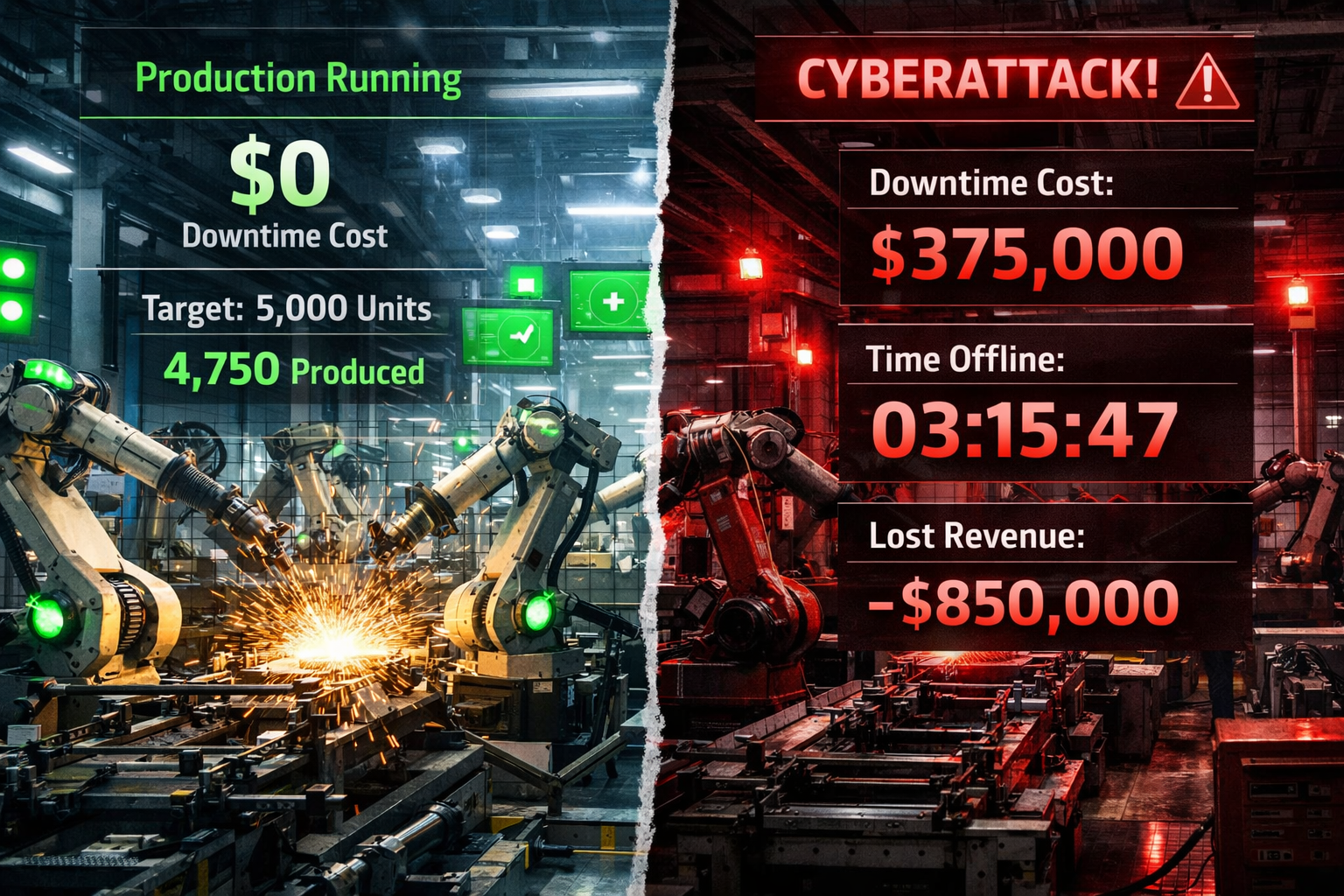
Factory Ransomware Attacks: The Perfect Extortion Target
Ransomware attacks on manufacturing facilities represent cybercrime at its most calculating and ruthless. Attackers specifically target manufacturers because they understand the unique pressure points that make these companies likely to pay quickly and pay well.
The typical factory ransomware attack follows a predictable pattern designed to maximize pressure and minimize the victim’s options. Attackers often strike during peak production periods, holidays, or critical delivery windows when downtime costs are highest and IT support may be limited.
How factory ransomware attacks typically unfold:
- Initial infiltration through phishing emails, compromised credentials, or vendor access
- Network reconnaissance to map production systems and identify critical assets
- Lateral movement from IT systems into operational technology networks
- Data exfiltration to enable double extortion tactics
- Simultaneous encryption of both IT systems and industrial control systems
- Ransom demands timed for maximum business impact
The sophistication of these attacks has increased dramatically. Modern ransomware groups research their targets extensively, understanding production schedules, customer commitments, and financial pressures that influence payment decisions.
What makes manufacturing particularly vulnerable:
- Low downtime tolerance creates urgency to restore operations quickly
- Limited backup systems for specialized industrial software and configurations
- Interconnected operations where one compromised system can shut down entire facilities
- Compliance requirements that prevent resuming production until safety systems are verified
- Customer penalties that make downtime extremely expensive
Double extortion tactics specifically target manufacturers:
Traditional ransomware focused on encrypting files and demanding payment for decryption keys. Modern attacks add data theft, threatening to release sensitive information if ransoms aren’t paid. For manufacturers, this might include:
- Customer lists and pricing information
- Proprietary manufacturing processes
- Product designs and specifications
- Financial data and strategic plans
- Employee personal information
One client faced demands for $2 million after attackers encrypted their production control systems and threatened to release customer data publicly. The combination of operational shutdown and potential data exposure created multiple pressure points that the criminals leveraged skillfully.
Protection strategies that work:
- Network segmentation that isolates production systems from corporate networks
- Offline backups that can’t be accessed or encrypted by ransomware
- Endpoint protection specifically designed for industrial environments
- Employee training focused on manufacturing-specific attack vectors
- Incident response planning that prioritizes safe production resumption
If attacked, key considerations include:
- Safety first – ensure all production systems are safe before attempting recovery
- Legal consultation regarding payment decisions and disclosure requirements
- Insurance coordination to understand coverage and claim procedures
- Customer communication to manage expectations and preserve relationships
- Evidence preservation for law enforcement and insurance investigations
The decision to pay or not pay ransoms involves complex legal, ethical, and business considerations. However, the best strategy remains prevention through proper cybersecurity measures and incident response preparation.
Cyber Threats in Production Facilities: Beyond the Network
Modern production facilities face cyber threats that extend far beyond traditional network security concerns. The integration of smart manufacturing technologies, IoT sensors, and automated systems has created an attack surface that includes physical production equipment, safety systems, and quality controls.
These threats are particularly dangerous because they can affect product quality, worker safety, and environmental compliance in addition to production efficiency. A cyberattack that manipulates temperature controls could spoil an entire batch of pharmaceuticals. Compromised safety systems could put workers at risk or trigger regulatory shutdowns.
Physical systems are now vulnerable to cyber threats:
- Programmable Logic Controllers (PLCs) that control production equipment
- Human-Machine Interfaces (HMIs) are used by operators to monitor and control processes
- Safety Instrumented Systems (SIS) are designed to prevent accidents and equipment damage
- Quality control systems that monitor product specifications and compliance
- Environmental controls for temperature, humidity, and contamination management
Real-world consequences of production facility cyber threats:
I worked with a chemical manufacturer where attackers modified temperature setpoints in their reactor systems. The changes were subtle enough to avoid immediate detection but could have caused product contamination or safety hazards if not discovered during a routine security audit.
Attack vectors specific to production environments:
- USB devices brought into facilities by maintenance personnel or contractors
- Wireless networks used for mobile devices or temporary equipment connections
- Remote access systems for equipment vendors or off-site monitoring
- Firmware vulnerabilities in industrial equipment that’s rarely updated
- Physical access to control panels, network equipment, or operator workstations
The challenge of legacy equipment:
Many production facilities operate equipment that was installed decades ago when cybersecurity wasn’t a consideration. These systems often lack basic security features like authentication, encryption, or access logging. Retrofitting security controls can be expensive and complex, but leaving them unprotected creates significant vulnerabilities.
Protecting production facilities requires a layered approach:
Physical security measures:
- Restricted access to control rooms and network equipment
- Visitor management systems that track contractor and vendor access
- Security cameras monitoring critical infrastructure areas
- Locked cabinets for network switches and control panels
Technical security controls:
- Network segmentation between production and corporate systems
- Monitoring software designed for industrial protocols and communications
- Regular security assessments of connected production equipment
- Firmware update management for industrial control systems
Operational security procedures:
- Background checks for personnel with access to critical systems
- Training programs focused on production environment security
- Incident response procedures that prioritize safety and production continuity
- Regular drills that test both cybersecurity and safety response capabilities
Working with a reliable partner like AlphaCIS can provide the industry expertise needed to secure production environments without disrupting operations. Our team understands the unique requirements of manufacturing facilities and can implement security measures that protect against cyber threats while maintaining the reliability and safety that production demands.
The goal is creating defense in depth that protects against both external attackers and insider threats while ensuring that security measures don’t interfere with production efficiency or worker safety. This requires understanding both cybersecurity principles and manufacturing operations – a combination that many traditional IT providers lack.
Ready to Take IT Off Your Plate?
Stop worrying about downtime, security risks, or endless IT frustrations. AlphaCIS is the trusted IT partner for small and mid-sized businesses in Metro Atlanta, keeping systems secure, connected, and running the way they should every day.
Whether it’s preventing costly outages, protecting your data, or giving your team unlimited support, we make sure technology helps your business grow instead of holding it back.
📅 Book Your Free ConsultationICS Security Risks: The Hidden Vulnerabilities in Your Factory
Industrial Control Systems (ICS) represent the nervous system of modern manufacturing, coordinating everything from assembly line speeds to safety shutoffs. However, these critical systems were designed decades ago with reliability and functionality as priorities – security was an afterthought at best.
The result is a manufacturing landscape filled with powerful systems that can be compromised by attackers with relatively basic skills. Unlike enterprise IT systems that receive regular security updates, ICS components often run for years without patches or security modifications due to uptime requirements and vendor restrictions.
Common ICS components and their vulnerabilities:
Supervisory Control and Data Acquisition (SCADA) systems:
- Often accessible through remote connections with weak authentication
- May use unencrypted communications protocols
- Frequently run on outdated operating systems with known vulnerabilities
- Lacks comprehensive logging and monitoring capabilities
Distributed Control Systems (DCS):
- Designed for isolated networks but increasingly connected to corporate systems
- May share credentials across multiple components
- Often lack proper access controls for different user roles
- Can be disrupted by network traffic or scanning activities
Programmable Logic Controllers (PLCs):
- Frequently ships with default passwords that are never changed
- May lack encryption for programming and communication interfaces
- Often accessible through vendor remote access systems
- Can be reprogrammed by attackers to cause equipment damage or safety hazards
Human Machine Interfaces (HMIs):
- May run on standard Windows systems with known vulnerabilities
- Often connected to both control networks and corporate networks
- Can be compromised through standard malware or phishing attacks
- May provide access to multiple production systems through a single compromise
Real-world ICS attack scenarios:
The infamous Stuxnet attack demonstrated how ICS vulnerabilities could be exploited to cause physical damage to industrial equipment. While most attacks focus on disruption rather than destruction, the potential for serious consequences remains high.
I’ve seen cases where attackers modified PLC programming to alter product specifications just enough to cause quality issues without triggering immediate alarms. The resulting product recalls and customer complaints caused more long-term damage than a straightforward ransomware attack.
Why ICS security is particularly challenging:
- Uptime requirements that prevent regular patching and updates
- Vendor restrictions on modifications to certified systems
- Legacy protocols that lack built-in security features
- Skills gaps between IT security professionals and OT operations staff
- Integration complexity when connecting isolated systems to modern networks
Protecting ICS environments requires specialized approaches:
Network-based protections:
- Industrial firewalls designed for OT protocols and communications
- Network segmentation that isolates critical control systems
- Monitoring tools that understand industrial communications and can detect anomalies
- Virtual patching through network security devices when system patching isn’t possible
Endpoint protections:
- Application whitelisting that prevents unauthorized software execution
- USB device controls to prevent malware introduction through removable media
- System hardening that removes unnecessary services and features
- Regular backup and recovery procedures for critical system configurations
Access management:
- Multi-factor authentication for remote access to control systems
- Role-based access controls that limit user privileges to necessary functions
- Regular review and removal of unnecessary user accounts
- Monitoring and logging of all access to critical control systems
Vendor management:
- Security requirements in contracts for equipment suppliers and service providers
- Controlled and monitored remote access for vendor support activities
- Regular security assessments of vendor-supplied systems and software
- Coordination with vendors on security updates and vulnerability management
The key to ICS security is understanding that these systems can’t be secured using traditional IT approaches. They require specialized knowledge, tools, and procedures that account for the unique requirements of industrial environments.
Working with experienced partners becomes crucial for ICS security. AlphaCIS has the industry expertise to implement security measures that protect your control systems without interfering with production operations. Our proactive solutions include 24/7 monitoring specifically designed for industrial environments and same-day support when issues arise.
Building Your Manufacturing Cybersecurity Defense Strategy
Creating effective cybersecurity for manufacturing companies requires a comprehensive approach that addresses both immediate threats and long-term operational requirements. The strategy must protect against manufacturing cyberattacks while maintaining the reliability and efficiency that modern production demands.
Start with risk assessment and asset inventory:
Before implementing security measures, you need a clear understanding of what you’re protecting and where your greatest vulnerabilities lie. This includes both traditional IT assets and operational technology components that may not be well-documented.
Critical assets to inventory:
- All network-connected production equipment and control systems
- Engineering workstations and design software systems
- File servers containing product specifications and customer data
- Remote access points used by vendors or off-site personnel
- Cloud services and external connections are used for business operations
Implement network segmentation and monitoring:
The foundation of manufacturing cybersecurity is proper network segmentation that isolates critical systems while enabling necessary business functions. This creates barriers that can contain attacks and provide visibility into unusual activities.
Essential segmentation strategies:
- Separate OT and IT networks with controlled connection points
- Isolate critical production lines from less critical systems
- Create DMZs for vendor access and file sharing
- Implement micro-segmentation within production networks to limit lateral movement
- Monitor all network traffic between segments for suspicious activities
Deploy endpoint protection and access controls:
Manufacturing environments require endpoint protection that can work in industrial settings without interfering with production operations. This includes both traditional endpoints like computers and specialized industrial devices.
Key endpoint protection measures:
- Application whitelisting on critical control systems
- USB device controls to prevent malware introduction
- Multi-factor authentication for all administrative access
- Regular security updates are applied during planned maintenance windows
- Backup and recovery procedures are tested regularly for critical systems
Develop incident response capabilities:
Manufacturing companies need incident response procedures that prioritize safety and production continuity while effectively containing and eliminating threats. This requires coordination between IT, operations, and safety personnel.
Essential incident response elements:
- Clear escalation procedures that involve appropriate personnel quickly
- Communication plans for customers, suppliers, and regulatory authorities
- Recovery prioritization that focuses on the most critical production systems first
- Evidence preservation procedures for law enforcement and insurance claims
- Regular testing and updates based on lessons learned and changing threats
Establish vendor and supply chain security:
Manufacturing companies must extend security considerations to their entire supply chain, including equipment vendors, software suppliers, and logistics partners. This requires both contractual requirements and technical controls.
Supply chain security measures:
- Security assessments for critical vendors and suppliers
- Contractual requirements for cybersecurity standards and incident notification
- Controlled access for vendor remote support and maintenance activities
- Regular audits of vendor security practices and compliance
- Incident response coordination with key supply chain partners
Invest in training and awareness:
Manufacturing cybersecurity depends on employees who understand both production requirements and security considerations. This includes everyone from operators and maintenance staff to engineers and executives.
Training program components:
- Role-specific security awareness for different job functions
- Phishing simulation and email security training
- Physical security procedures for production areas and control rooms
- Incident reporting procedures that encourage prompt notification
- Regular updates on new threats and protection measures
Partner with cybersecurity experts:
Manufacturing companies often lack the internal expertise needed to implement and maintain comprehensive cybersecurity programs. Partnering with experienced providers can fill these gaps while ensuring that security measures align with operational requirements.
Benefits of expert partnership:
- Industry-specific knowledge of manufacturing threats and vulnerabilities
- 24/7 monitoring and response capabilities that most manufacturers can’t maintain internally
- Access to specialized tools and technologies designed for industrial environments
- Regulatory compliance support for industry-specific requirements
- Cost-effective expertise compared to hiring and training internal staff
AlphaCIS provides the reliable partner relationship that manufacturing companies need, with straightforward pricing and personalized service that eliminates IT headaches. Our team combines cybersecurity expertise with an understanding of manufacturing operations, ensuring that security measures enhance rather than hinder your business objectives.
The goal is to create a security program that provides peace of mind while enabling the operational excellence that drives manufacturing success. This requires ongoing attention and continuous improvement as threats evolve and operations change.
Frequently Asked Questions
Why are manufacturing companies targeted more than other industries?
Manufacturing companies are targeted because they have low tolerance for downtime, often pay ransoms quickly to restore production, and typically have weaker cybersecurity compared to financial or healthcare organizations. The combination of valuable intellectual property and urgent operational needs makes them attractive targets for cybercriminals.
What’s the difference between IT and OT security in manufacturing?
IT security focuses on protecting information systems like computers and networks that handle business data. OT security protects operational technology like control systems and production equipment. OT systems often lack basic security features and can’t be updated frequently due to uptime requirements, creating unique vulnerabilities.
How much does manufacturing downtime from cyberattacks typically cost?
Downtime costs vary widely by industry and company size, ranging from $50,000 to $2 million per hour. This includes lost production revenue, fixed costs that continue during downtime, emergency response expenses, and customer penalties for missed deliveries.
Should manufacturing companies pay ransoms to restore operations?
Payment decisions involve complex legal, ethical, and business considerations. While paying may restore operations faster, it encourages future attacks and doesn’t guarantee full recovery. Companies should consult legal counsel and consider alternatives like insurance coverage and backup recovery procedures.
What are the most common entry points for manufacturing cyberattacks?
Common entry points include phishing emails targeting employees, compromised vendor remote access, USB devices brought into facilities, unpatched systems with known vulnerabilities, and weak credentials on industrial control systems. Supply chain connections also provide attack vectors.
How can manufacturers protect against supply chain cyber threats?
Protection requires vendor security assessments, contractual cybersecurity requirements, network segmentation that isolates supplier access, continuous monitoring of third-party connections, and incident response coordination with key partners. The goal is to maintain necessary connectivity while containing potential threats.
What industrial control systems are most vulnerable to cyberattacks?
PLCs with default passwords, SCADA systems with remote access capabilities, HMIs running outdated operating systems, and safety systems lacking proper access controls are particularly vulnerable. Legacy equipment that wasn’t designed with cybersecurity in mind presents the greatest risks.
How often should manufacturing companies test their cybersecurity defenses?
Regular testing should include monthly phishing simulations, quarterly vulnerability assessments, annual penetration testing, and semi-annual incident response drills. Industrial control systems may require specialized testing approaches that don’t disrupt production operations.
What cybersecurity insurance considerations apply to manufacturing companies?
Manufacturing cybersecurity insurance should cover operational downtime, data breach response, ransomware attacks, and supply chain incidents. Policies should account for the unique risks of industrial environments and the high costs of production interruption.
Can small manufacturers afford comprehensive cybersecurity programs?
Small manufacturers can implement effective cybersecurity through managed security services, cloud-based solutions, and partnerships with experienced providers. The key is prioritizing the most critical protections and working with partners who understand manufacturing requirements and budget constraints.
What role does employee training play in manufacturing cybersecurity?
Employee training is crucial because many attacks start with human error or social engineering. Manufacturing-specific training should cover email security, physical security procedures, USB device policies, and incident reporting. Different roles require different training focuses.
How do cybersecurity requirements differ across manufacturing sectors?
Requirements vary based on regulatory environments, customer demands, and operational criticality. Automotive manufacturers face different compliance requirements than food processors or pharmaceutical companies. However, all manufacturing sectors share common vulnerabilities related to operational technology and supply chain connectivity.
Key Takeaways
• Manufacturing companies are prime cyberattack targets due to their low downtime tolerance, valuable intellectual property, and typically weaker cybersecurity compared to other industries
• The convergence of IT and OT systems creates unique vulnerabilities that require specialized security approaches different from traditional enterprise cybersecurity
• Supply chain connectivity amplifies risks as attackers can use compromised suppliers or vendors as entry points to larger manufacturing networks
• Operational downtime from cyberattacks can cost manufacturers $50,000 to $2 million per hour, creating enormous pressure to pay ransoms quickly
• Industrial control systems lack basic security features and can’t be easily updated, requiring network-based protections and specialized monitoring
• Factory ransomware attacks are specifically designed to maximize pressure on manufacturers through timing, targeting, and double extortion tactics
• Production facility cyber threats extend beyond networks to include physical systems that affect product quality, worker safety, and regulatory compliance
• Effective manufacturing cybersecurity requires comprehensive strategies that address risk assessment, network segmentation, endpoint protection, incident response, and supply chain security
• Employee training and expert partnerships are essential for implementing and maintaining cybersecurity programs that protect operations without hindering productivity
• Proactive security measures and 24/7 monitoring provide the peace of mind that manufacturing executives need to focus on business growth rather than cyber threats
Manufacturing Cybersecurity Risk Assessment
Evaluate your facility's vulnerability to cyber threats
Conclusion
Manufacturing companies face a perfect storm of cybersecurity challenges that make them irresistible targets for cybercriminals. The combination of high-value operations, low downtime tolerance, and often inadequate security measures creates opportunities that attackers exploit with devastating effectiveness.
The path forward isn’t about choosing between security and operational efficiency – it’s about implementing cybersecurity for manufacturing companies that enhances both. Modern manufacturers need protection strategies that understand the unique requirements of industrial environments while providing the robust defense capabilities that today’s threat landscape demands.
The key is taking action before you become a statistic. Every day you delay implementing proper cybersecurity measures is another day your facility remains vulnerable to manufacturing cyberattacks that could shut down production, compromise sensitive data, and damage customer relationships.
Your next steps should include:
- Conduct a comprehensive security assessment that covers both IT and OT systems
- Implement network segmentation to isolate critical production systems
- Establish robust backup and recovery procedures that can restore operations quickly
- Deploy 24/7 monitoring designed for industrial environments
- Partner with cybersecurity experts who understand manufacturing operations
Don’t wait for a cyberattack to force these decisions. The manufacturers who thrive in 2026 and beyond will be those who view cybersecurity as an essential operational capability, not an optional expense.
AlphaCIS brings the industry expertise and reliable partner relationship that manufacturing companies need to eliminate IT headaches and achieve peace of mind. Our proactive solutions, straightforward pricing, and same-day support ensure that your cybersecurity program enhances rather than hinders your operational excellence.
Ready to protect your manufacturing operations? Contact AlphaCIS today for a personalized security assessment and discover how we can help you build defenses that keep production running while keeping threats out.
Ready to Take IT Off Your Plate?
Stop worrying about downtime, security risks, or endless IT frustrations. AlphaCIS is the trusted IT partner for small and mid-sized businesses in Metro Atlanta, keeping systems secure, connected, and running the way they should every day.
Whether it’s preventing costly outages, protecting your data, or giving your team unlimited support, we make sure technology helps your business grow instead of holding it back.
📅 Book Your Free Consultation
Dmitriy Teplinskiy
I have worked in the IT industry for 15+ years. During this time I have consulted clients in accounting and finance, manufacturing, automotive and boating, retail and everything in between. My background is in Networking and Cybersecurity