You walk into the office like any other morning, coffee in hand, ready to start the day. A couple of your employees are already there, but something’s off. One of them says their computer isn’t working. Another says the same.
You walk over to take a look. On the screen is a black background with a red message:
“Your files have been encrypted. You have 72 hours to pay or your data will be lost forever.”
You check a few more computers. It’s not just one. It’s all of them.
Your accounting system is down. Shared folders are gone. Email is inaccessible. Every file your business runs on is locked. You can feel the pressure building in your chest as the reality sets in: your entire operation is frozen.
In that moment, you’re not thinking about strategy or growth or clients. You’re thinking, How do I stop this from getting worse?
I’ve witnessed firsthand how devastating cyberattacks can be when organizations lack proper endpoint protection. Traditional security measures are no longer enough in today’s threat landscape. That’s where Endpoint Detection and Response (EDR) comes in as your digital security guardian that never sleeps.
Key Takeaways
• EDR provides real-time monitoring and threat detection across all endpoints in your network, going far beyond traditional antivirus capabilities
• Advanced threat hunting and behavioral analysis help identify sophisticated attacks that would otherwise go unnoticed for months
• Rapid incident response capabilities can contain and remediate threats in minutes rather than days or weeks
• Comprehensive visibility into endpoint activities enables proactive security posture improvements and compliance requirements
• Cost-effective protection compared to the potential millions in damages from successful cyberattacks and data breaches
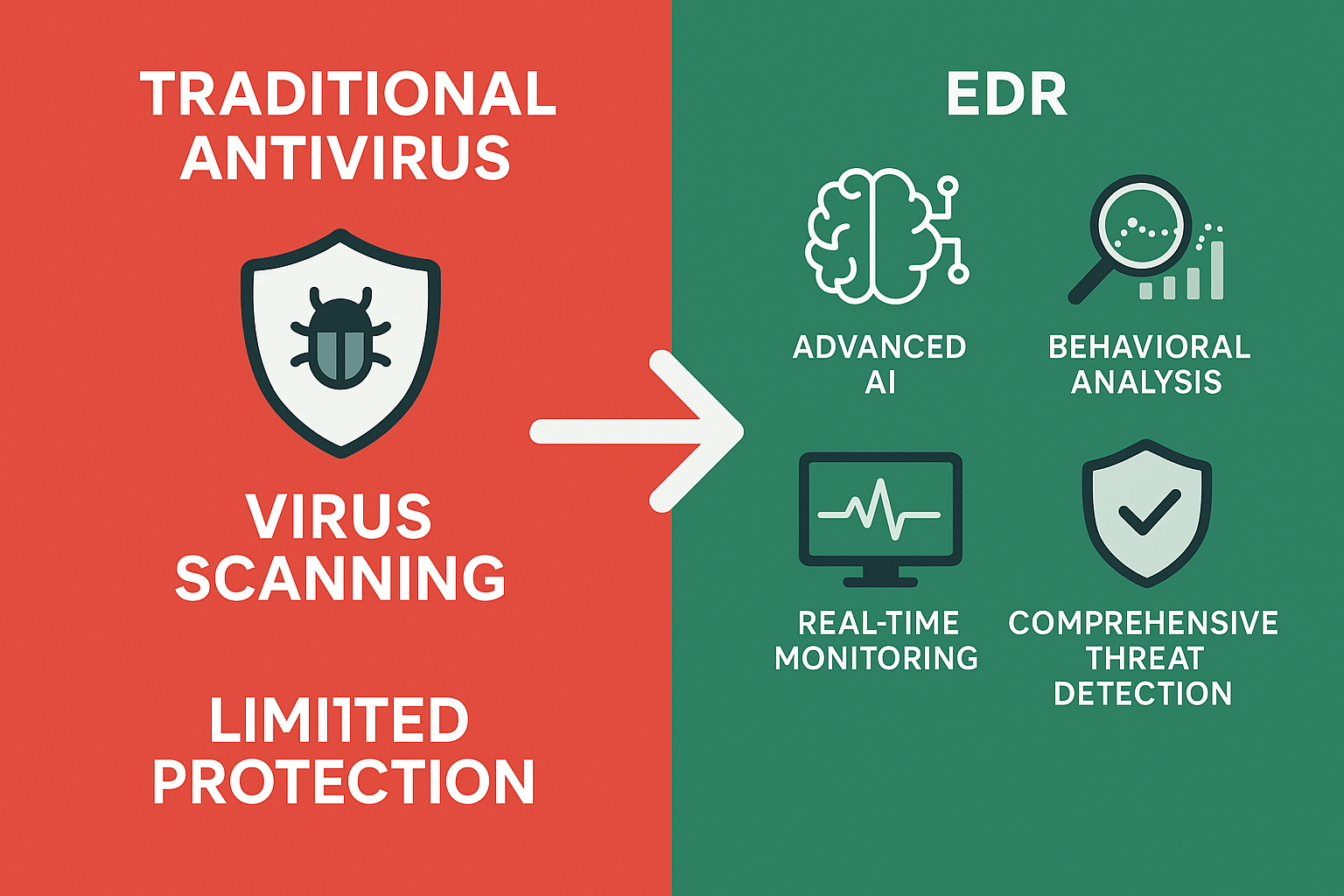
Understanding the Cybersecurity Landscape: Why Traditional Antivirus Isn’t Enough
Let me share a story that perfectly illustrates why we need to talk about EDR. Last year, I consulted with a mid-sized manufacturing company that thought its basic antivirus solution was sufficient protection. They discovered the hard way that cybercriminals had been living in their network for four months, slowly mapping their systems and stealing intellectual property.
The attack started with a simple phishing email that bypassed their antivirus. The malware was so sophisticated that it mimicked normal user behavior, making it invisible to traditional security tools. By the time they discovered the breach, the damage was catastrophic: stolen designs, compromised customer data, and a reputation that took years to rebuild.
The Evolution of Cyber Threats
Today’s cybercriminals are not the script kiddies of the past. They’re:
– Highly organized criminal enterprises with sophisticated tools
– Patient and persistent, often spending months planning attacks
– Adaptive, constantly evolving their techniques to bypass security measures
– Financially motivated, targeting businesses of all sizes for maximum profit
Traditional antivirus solutions rely on signature-based detection, essentially looking for known bad files. But what happens when attackers use:
– Zero-day exploits (unknown vulnerabilities)
– Fileless attacks that live in memory
– Living-off-the-land techniques using legitimate tools
– AI-powered attack methods
The answer is simple: traditional antivirus fails spectacularly.
What Is Endpoint Detection and Response (EDR)?
Endpoint Detection and Response (EDR) is a cybersecurity solution that continuously monitors and collects activity data from endpoints (computers, servers, mobile devices) to detect and respond to cyber threats in real-time.
Think of EDR as having a highly trained security analyst watching every single device in your organization 24/7, but with superhuman capabilities to process massive amounts of data and spot patterns that humans would miss.
Core Components of EDR Solutions
1. Continuous Monitoring and Data Collection
– Real-time monitoring of all endpoint activities
– Collection of process executions, file modifications, and network connections
– User behavior tracking and analysis
– System configuration changes monitoring
2. Threat Detection and Analysis
– Behavioral analysis to identify suspicious activities
– Machine learning algorithms for pattern recognition
– Threat intelligence integration
– Anomaly detection capabilities
3. Investigation and Forensics
– Detailed timeline reconstruction of security incidents
– Root cause analysis capabilities
– Evidence collection and preservation
– Attack vector identification
4. Response and Remediation
– Automated threat containment
– Remote device isolation
– Malware removal and system cleanup
– Policy enforcement and updates
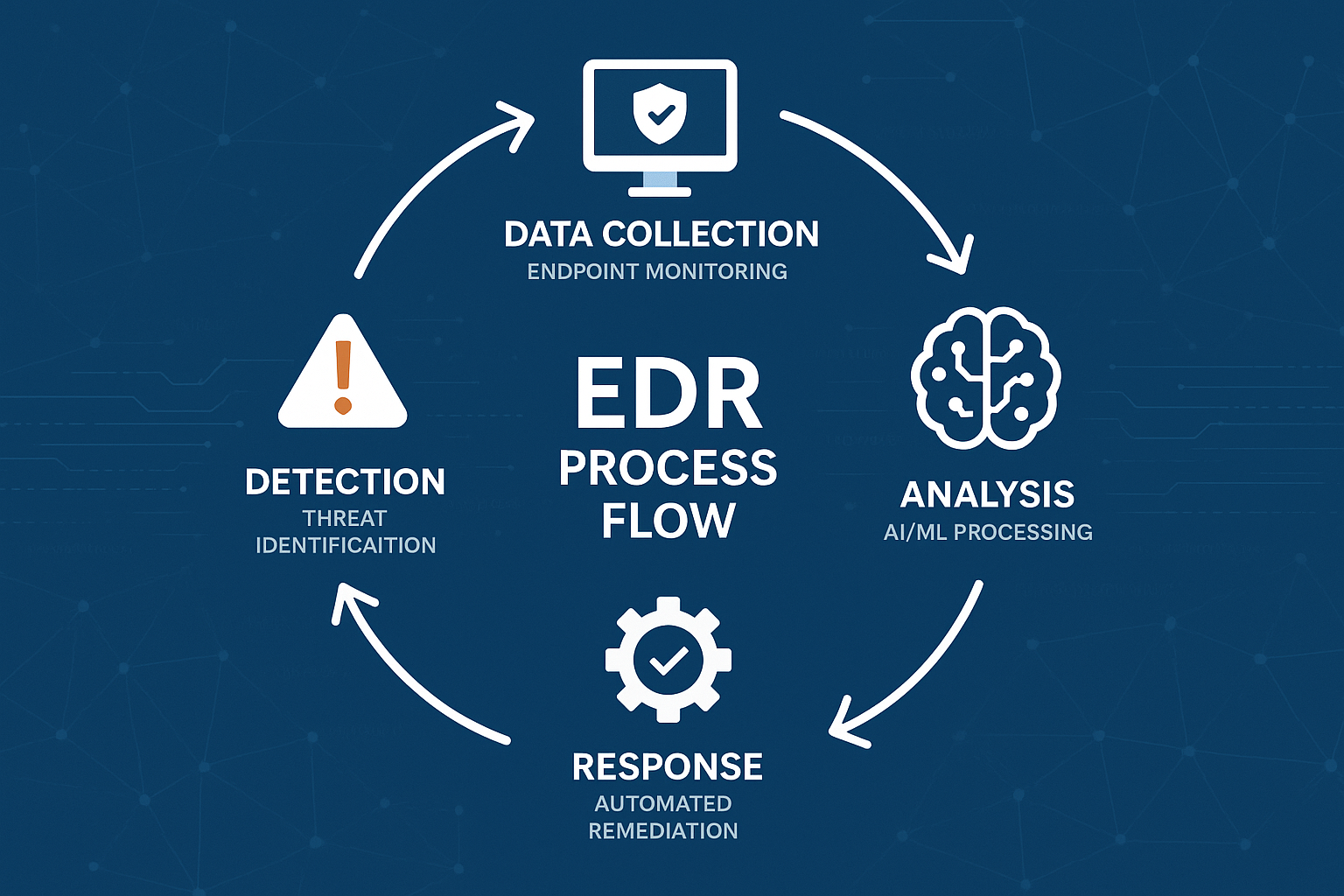
How EDR Works: The Technical Deep Dive
Let me walk you through how EDR works in practice. When I implement EDR solutions for clients, I often use this analogy: imagine your network as a busy airport, and EDR as an incredibly sophisticated security system.
The EDR Process Flow
Step 1: Data Collection
The EDR agent installed on each endpoint acts like security cameras throughout the airport, continuously recording:
– Process creation and termination
– File system changes
– Registry modifications
– Network communications
– User login activities
– Memory usage patterns
Step 2: Real-Time Analysis
This data streams to a central console where advanced analytics engines:
– Compare activities against known threat patterns
– Apply machine learning models to identify anomalies
– Cross-reference with global threat intelligence feeds
– Score risk levels for different activities
Step 3: Alert Generation
When suspicious activity is detected, the system:
– Generates prioritized alerts based on severity
– Provides context and supporting evidence
– Suggests response actions
– Escalates critical threats immediately
Step 4: Investigation and Response
Security teams can then:
– Drill down into detailed forensic data
– Trace attack progression across the network
– Implement containment measures
– Remediate affected systems
EDR vs Traditional Antivirus Interactive Tool
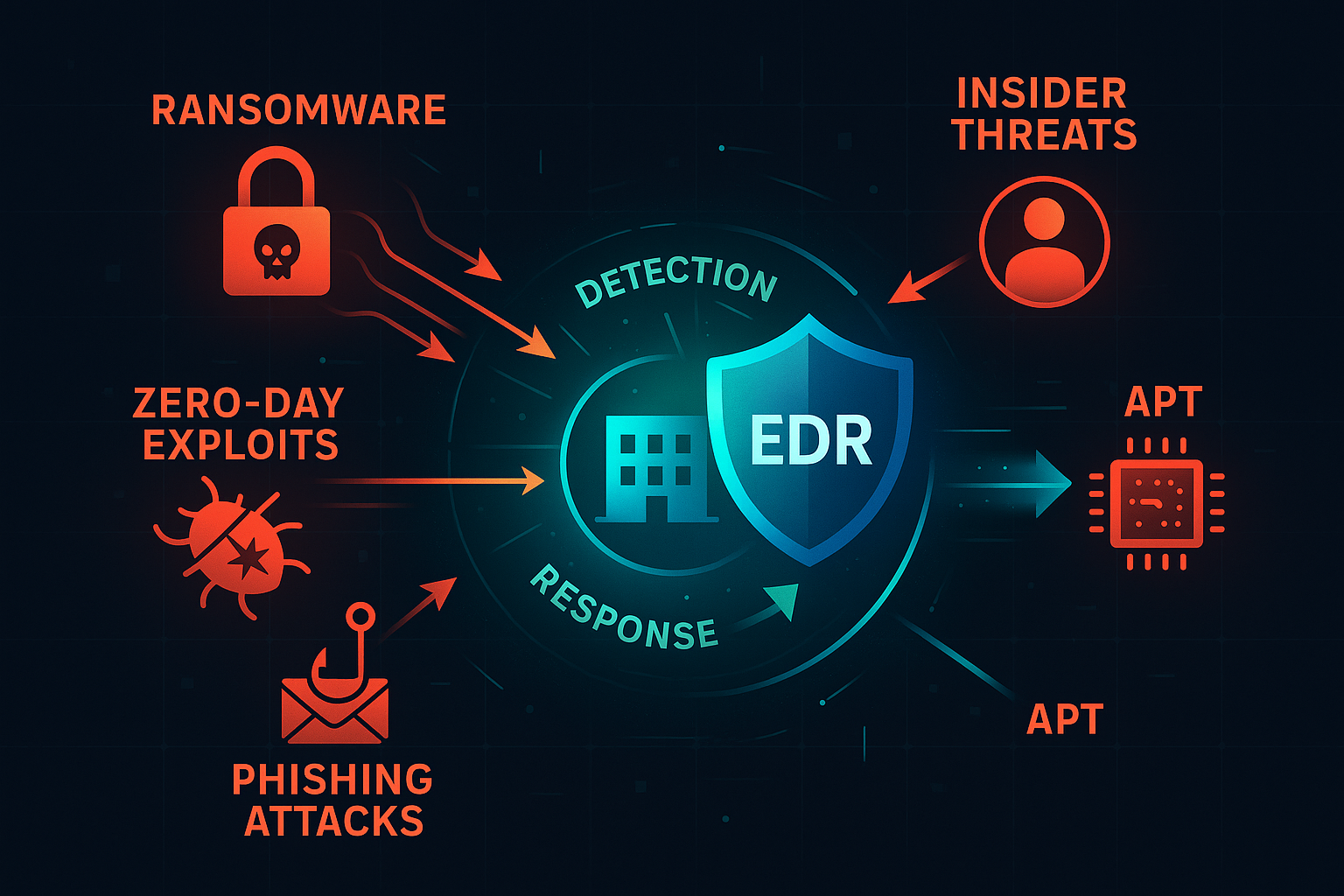
🎯 Advanced Persistent Threat (APT)
A sophisticated attacker gains initial access through a spear-phishing email and attempts to move laterally through your network over several weeks.
🔒 Ransomware Attack
Malicious software encrypts your files and demands payment. Time is critical to prevent complete data loss.
👤 Insider Threat
A disgruntled employee with legitimate access begins exfiltrating sensitive company data.
🌐 Zero-Day Exploit
Attackers use a previously unknown vulnerability to gain access to your systems.
Key Benefits of EDR: Why You Need It Now
1. Advanced Threat Detection
Unlike traditional antivirus software, which relies on known signatures, EDR uses behavioral analysis and machine learning to identify threats based on what they do, rather than what they look like. This means EDR can catch:
– Zero-day exploits before they’re publicly known
– Fileless malware that exists only in memory
– Living-off-the-land attacks using legitimate tools maliciously
– Insider threats from authorized users acting suspiciously
2. Real-Time Visibility and Monitoring
One of my clients recently told me, “EDR is like having X-ray vision into our network.” Here’s what you get:
– Complete endpoint visibility across all devices
– Real-time activity monitoring 24/7/365
– Historical data retention for forensic analysis
– Cross-platform support (Windows, Mac, Linux, mobile)
3. Rapid Incident Response
Speed is everything in cybersecurity. The average time to identify and contain a breach is 287 days without proper tools. With EDR:
– Automated threat containment in minutes
– Remote device isolation to prevent spread
– Guided remediation with step-by-step instructions
– Rollback capabilities to restore systems quickly
4. Proactive Threat Hunting
EDR doesn’t just wait for alerts; it actively hunts for threats:
– Hypothesis-driven searches based on threat intelligence
– Anomaly detection for unusual patterns
– Threat landscape analysis to stay ahead of attackers
– Custom detection rules tailored to your environment
EDR vs. Traditional Antivirus: The Critical Differences
Let me share a comparison that drives home the difference. Last month, I worked with two similar companies: one used traditional antivirus, while the other employed EDR.
| Capability | Traditional Antivirus | EDR Solution |
| Detection Method | Signature-based | Behavioral + AI/ML |
| Response Time | Hours to days | Minutes |
| Threat Coverage | Known malware only | Known + unknown threats |
| Investigation Tools | Basic logs | Comprehensive forensics |
| Automation | Limited | Extensive |
| Cost of Breach | $4.24M average | 80% reduction |
The company with a traditional antivirus suffered a $1.2 million breach that went undetected for 6 months. The EDR-protected company stopped a similar attack in 12 minutes with zero data loss.
Types of EDR Solutions: Finding Your Perfect Fit
Not all EDR solutions are created equal. Based on my experience implementing dozens of these systems, here are the main categories:
1. Standalone EDR
– Best for: Organizations with existing security teams
– Pros: Comprehensive features, customizable
– Cons: Requires dedicated security expertise
– Examples: CrowdStrike Falcon, SentinelOne
2. Managed EDR (MDR)
– Best for: Small to medium businesses without security teams
– Pros: 24/7 monitoring by experts, no hiring needed
– Cons: Less control, ongoing monthly costs
– Examples: Managed services from security providers
3. Integrated EDR
– Best for: Organizations wanting unified security platforms
– Pros: Single pane of glass, simplified management
– Cons: May sacrifice some specialized features
– Examples: Microsoft Defender for Endpoint, Symantec
4. Cloud-Native EDR
– Best for: Cloud-first organizations
– Pros: Scalable, no infrastructure needed
– Cons: Requires internet connectivity
– Examples: Most modern EDR solutions
Implementation Best Practices: Lessons from the Field
Over the years, I’ve seen EDR implementations succeed spectacularly and fail miserably. Here’s what I’ve learned:
Phase 1: Planning and Preparation
1. Conduct a Security Assessment
– Inventory all endpoints and assets
– Identify critical systems and data
– Assess current security gaps
– Define success metrics
2. Choose the Right Solution
– Evaluate based on your specific needs
– Consider your team’s technical expertise
– Factor in budget and scalability requirements
– Test with proof-of-concept deployments
Phase 2: Deployment Strategy
1. Start with a Pilot Program
– Deploy to 10-20% of endpoints first
– Choose a mix of critical and standard systems
– Monitor performance and user impact
– Gather feedback and adjust policies
2. Phased Rollout
– Deploy to critical systems first
– Gradually expand to all endpoints
– Maintain detailed deployment logs
– Provide user training and support
Phase 3: Optimization and Tuning
1. Fine-Tune Detection Rules
– Reduce false positives
– Customize alerts for your environment
– Implement automated responses
– Regular policy reviews and updates
2. Staff Training and Processes
– Train the security team on new tools
– Develop incident response procedures
– Create escalation protocols
– Regular tabletop exercises
Common EDR Implementation Challenges and Solutions
Challenge 1: Alert Fatigue
Problem: Too many false positives overwhelm security teams
Solution:
– Start with conservative settings
– Gradually increase sensitivity
– Implement alert prioritization
– Use automated triage and response
Challenge 2: Performance Impact
Problem: EDR agents slow down endpoint performance
Solution:
– Choose lightweight solutions
– Optimize agent configurations
– Monitor system performance metrics
– Implement during maintenance windows
Challenge 3: User Resistance
Problem: Employees complain about new security measures
Solution:
– Communicate the business benefits
– Provide comprehensive training
– Address concerns promptly
– Show how EDR protects their work
Challenge 4: Integration Complexity
Problem: EDR doesn’t integrate well with existing tools
Solution:
– Evaluate integration capabilities upfront
– Use API-based connections where possible
– Consider unified security platforms
– Plan for data migration and workflows
The ROI of EDR: Making the Business Case
When I present EDR to executives, I always start with this statistic: the average cost of a data breach is $4.24 million, but organizations with EDR reduce this by 80% or more.
Direct Cost Savings
1. Reduced Breach Costs
– Faster detection and containment
– Lower forensic investigation costs
– Reduced regulatory fines
– Minimized business disruption
2. Operational Efficiency
– Automated threat response
– Reduced manual investigation time
– Streamlined compliance reporting
– Lower insurance premiums
Indirect Benefits
1. Business Continuity
– Reduced downtime from attacks
– Maintained customer trust
– Protected intellectual property
– Preserved competitive advantage
2. Competitive Advantage
– Enhanced security posture
– Improved customer confidence
– Better vendor relationships
– Increased market opportunities
Real-World ROI Example
Let me share a case study from a 200-employee professional services firm:
EDR Investment: $90,000 annually
Prevented Breach Cost: $2.1 million
Operational Savings: $150,000 annually
Net ROI: 2,400% in the first year
Choosing the Right EDR Solution: A Buyer’s Guide
Key Evaluation Criteria
1. Detection Capabilities
– Behavioral analysis sophistication
– Machine learning algorithms
– Threat intelligence integration
– Custom rule creation
2. Response and Remediation
– Automated response options
– Remote isolation capabilities
– Rollback and recovery features
– Integration with other security tools
3. Usability and Management
– Intuitive dashboard design
– Reporting and analytics
– Multi-tenant capabilities
– Mobile management options
4. Scalability and Performance
– Agent resource consumption
– Cloud vs. on-premise options
– Multi-platform support
– Global deployment capabilities
Questions to Ask Vendors
1. What is your mean time to detection (MTTD) for unknown threats?
2. How do you handle false positives and alert tuning?
3. What level of managed services do you provide?
4. How does your solution integrate with our existing security stack?
5. What compliance frameworks do you support?
6. What is your incident response process?
7. How do you handle endpoint performance optimization?
8. What training and support do you provide?
Future of EDR: What’s Coming Next
The cybersecurity landscape is evolving rapidly, and EDR is evolving with it:
Extended Detection and Response (XDR)
XDR expands beyond endpoints to include:
– Network traffic analysis
– Cloud workload protection
– Email and collaboration tools
– Identity and access management
AI and Machine Learning Advancement
Future EDR will feature:
– More sophisticated behavioral analysis
– Predictive threat modeling
– Automated threat hunting
– Self-tuning detection algorithms
Zero Trust Integration
EDR will become a key component of Zero Trust architectures:
– Continuous device verification
– Dynamic access controls
– Micro-segmentation support
– Identity-based security policies
Taking Action: Your Next Steps
If you’ve made it this far, you understand why EDR is essential for modern cybersecurity. Here’s your action plan:
Immediate Actions (This Week)
1. Assess Your Current Security Posture
– Audit your existing endpoint protection
– Identify gaps in visibility and response
– Document critical assets and data
2. Build Your Business Case
– Calculate potential breach costs for your organization
– Research EDR solutions that fit your needs
– Prepare ROI projections for stakeholders
Short-Term Actions (Next 30 Days)
1. Vendor Evaluation
– Request demos from 3-5 EDR vendors
– Conduct proof-of-concept testing
– Check references from similar organizations
2. Internal Preparation
– Assess your team’s technical capabilities
– Plan training and skill development
– Develop implementation timeline
Long-Term Actions (Next 90 Days)
1. Implementation Planning
– Finalize vendor selection
– Develop a detailed deployment plan
– Prepare change management strategy
2. Success Measurement
– Define key performance indicators
– Establish baseline security metrics
– Plan regular security assessments
Conclusion
The question isn’t whether you’ll face a cyberattack, it’s when. In today’s threat landscape, traditional antivirus is like bringing a knife to a gunfight. You need the advanced capabilities that only EDR can provide.
I’ve seen too many organizations learn this lesson the hard way. Don’t let yours be next. The cost of implementing EDR pales in comparison to the devastating impact of a successful cyberattack.
EDR isn’t just a security tool; it’s business insurance for the digital age. It provides the visibility, detection, and response capabilities you need to protect your organization’s most valuable assets: your data, your reputation, and your future.
The threat actors aren’t waiting. Neither should you.
Take the first step today. Your future self and your stakeholders will thank you for it.
The question isn’t whether you’ll face a cyberattack, it’s when. In today’s threat landscape, traditional antivirus is like bringing a knife to a gunfight. You need the advanced capabilities that only EDR can provide.
I’ve seen too many organizations learn this lesson the hard way. Don’t let yours be next. The cost of implementing EDR pales in comparison to the devastating impact of a successful cyberattack.
EDR isn’t just a security tool; it’s business insurance for the digital age. It provides the visibility, detection, and response capabilities you need to protect your organization’s most valuable assets: your data, your reputation, and your future.
The threat actors aren’t waiting. Neither should you.
Book a Schedule: Book a 30-Minute Call With Us
Latest Article: IT Compliance Made Simple: A Small Business Guide

Dmitriy Teplinskiy
I have worked in the IT industry for 15+ years. During this time I have consulted clients in accounting and finance, manufacturing, automotive and boating, retail and everything in between. My background is in Networking and Cybersecurity



