Across Atlanta’s manufacturing plants, millions of dollars in revenue depend on machines powered by outdated software. Many of these systems have not received a security update in years, quietly becoming hackers’ favorite entry points.
It’s a growing issue. Unsupported software is now one of the top causes of industrial cyber incidents in the Southeast. Companies pour resources into physical security and employee awareness, yet overlook the outdated systems running the very equipment that keeps their production lines alive.
When those systems fail or get breached, the results aren’t just inconvenient. They’re catastrophic: halted production, data loss, regulatory fines, and reputational damage that takes years to rebuild.
Keeping unsupported software in play might seem like a cost-saving decision, but in today’s threat landscape, it’s like leaving the factory doors wide open overnight.
Key Takeaways

Ready to Take IT Off Your Plate?
Stop worrying about downtime, security risks, or endless IT frustrations. AlphaCIS is the trusted IT partner for small and mid-sized businesses in Metro Atlanta, keeping systems secure, connected, and running the way they should every day.
Whether it’s preventing costly outages, protecting your data, or giving your team unlimited support, we make sure technology helps your business grow instead of holding it back.
📅 Book Your Free Consultation- Unsupported software creates invisible attack vectors that cybercriminals actively exploit, with manufacturing being their #1 target in 2025
- Atlanta’s manufacturing sector faces unique risks due to its concentration of automotive, aerospace, and food processing industries
- The true cost extends beyond downtime to include regulatory fines, supply chain disruptions, and permanent customer loss
- Legacy systems can be secured through strategic modernization, virtual patching, and network segmentation
- Proactive software lifecycle management reduces security risks by up to 87% while improving operational efficiency
The Hidden Crisis in Atlanta’s Manufacturing Hub
Atlanta has earned its reputation as the “Silicon Valley of the South,” but this technological prowess comes with a dark side that many manufacturers are only now beginning to understand. The very software systems that power our production lines, manage our supply chains, and control our quality processes are becoming our greatest vulnerabilities.
What Makes Software “Unsupported”?
When I talk to manufacturing executives, I often get puzzled looks when I mention “unsupported software.” Let me break it down in simple terms:
Unsupported software is any program, operating system, or application that no longer receives:
– Security patches and updates
– Technical support from the vendor
– Compatibility updates for new hardware
– Bug fixes and performance improvements
This happens when:
– End-of-life (EOL) dates pass – Vendors stop supporting older versions
– Licensing expires – Companies skip renewals to cut costs
– Custom applications are built without ongoing maintenance contracts
– Legacy systems become too old to update safely
The Atlanta Manufacturing Landscape: A Perfect Storm
Atlanta’s manufacturing sector is particularly vulnerable because of its unique characteristics:
Industry Concentration: Our region hosts over 2,400 manufacturing facilities, creating a dense target-rich environment for cybercriminals. The automotive corridor alone includes major players like:
– Porsche’s North American headquarters
– Mercedes-Benz’s U.S. operations
– Dozens of Tier 1 and Tier 2 suppliers
Interconnected Supply Chains: Atlanta’s role as a logistics hub means that a security breach at one facility can cascade through entire supply networks, amplifying the impact exponentially.
Mixed Technology Environments: Many local manufacturers operate hybrid environments where cutting-edge Industry 4.0 technologies sit alongside legacy systems from the 1990s and early 2000s.
Challenge 1: The Legacy System Trap
The Problem: When “If It Ain’t Broke, Don’t Fix It” Becomes Dangerous
I recently worked with a food processing plant in Gwinnett County that was still running its entire inventory management system on Windows Server 2003. The plant manager’s reasoning was sound from a business perspective: “It’s been running perfectly for 15 years. Why would we spend $200,000 to replace something that works?”
Here’s why that thinking is flawed:
Windows Server 2003 stopped receiving security updates in July 2015. That means every vulnerability discovered since then, and there have been hundreds, remains unpatched and exploitable. It’s like leaving your front door unlocked because the lock “still works,” even though everyone in the neighborhood has a copy of your key.
Why Legacy Systems Matter More Than Ever
The manufacturing sector has become the #1 target for cyberattacks in 2025, with 67% of all ransomware attacks targeting industrial operations. Here’s what the data tells us:
| Year | Manufacturing | Average Downtime | Average Cost |
| 2023 | 2,847 incidents | 14.2 hours | $1.8M |
| 2024 | 3,921 incidents | 18.7 hours | $2.4M |
| 2025 | 5,200+ incidents | 22.3 hours | $3.1M |
*Projected based on Q1-Q2 data
The Solution: Strategic Legacy Modernization
The key isn’t to rip and replace everything overnight. Instead, successful manufacturers are taking a phased approach:
Phase 1: Assessment and Prioritization
– Inventory all software systems and their support status
– Identify critical vs. non-critical systems
– Map interdependencies and potential failure points
Phase 2: Risk-Based Mitigation
– Implement network segmentation to isolate legacy systems
– Deploy virtual patching solutions for unsupported software
– Establish monitoring and anomaly detection
Phase 3: Strategic Replacement
– Replace highest-risk systems first
– Migrate to modern, supported platforms
– Ensure proper lifecycle management for new systems
Challenge 2: The Hidden Costs of Cyber Incidents
The Problem: It’s Not Just About the Ransom
When most manufacturers think about cybersecurity costs, they focus on the obvious expenses: ransom payments, new equipment, and maybe some consultant fees. But the real costs of a cyber incident involving unsupported software go much deeper.
Let me share a story that illustrates this perfectly. Last year, I worked with a textile manufacturer in Dalton whose production planning system was compromised. The attack itself lasted only 6 hours, but the ripple effects continued for months:
Immediate Costs(Week 1):
– $150,000 in ransom payment
– $75,000 in emergency IT response
– $200,000 in production downtime
Extended Costs (Months 2-6):
– $800,000 in lost contracts due to delivery delays
– $300,000 in regulatory compliance and legal fees
– $450,000 in customer retention and reputation management
– $250,000 in insurance premium increases
Total Impact: $2.225 million for what started as a “minor” security incident.
Why Unsupported Software Amplifies These Costs
Incidents involving unsupported software are particularly expensive because:
- Longer Recovery Times: Without vendor support, you’re on your own to figure out what happened and how to fix it
- Deeper System Compromise: Unpatched vulnerabilities often allow attackers to move laterally through your network
- Compliance Violations: Many industry standards require current, supported software
- Insurance Complications: Policies may not cover incidents involving known unsupported systems
The Solution: Total Cost of Ownership (TCO) Analysis
Smart manufacturers are shifting from purchase price thinking to total cost of ownership analysis. Here’s how to calculate the true cost:
Current State Costs (Unsupported Software):
– Base operational costs
– Increased security monitoring
– Manual workarounds and inefficiencies
– Risk-adjusted potential incident costs
– Compliance gap remediation
Future State Costs (Supported Software):
– Software licensing and maintenance
– Implementation and training
– Ongoing support and updates
– Reduced security and operational risks
In most cases, the TCO analysis shows that modernization pays for itself within 18-24 months, even before considering the risk reduction benefits.
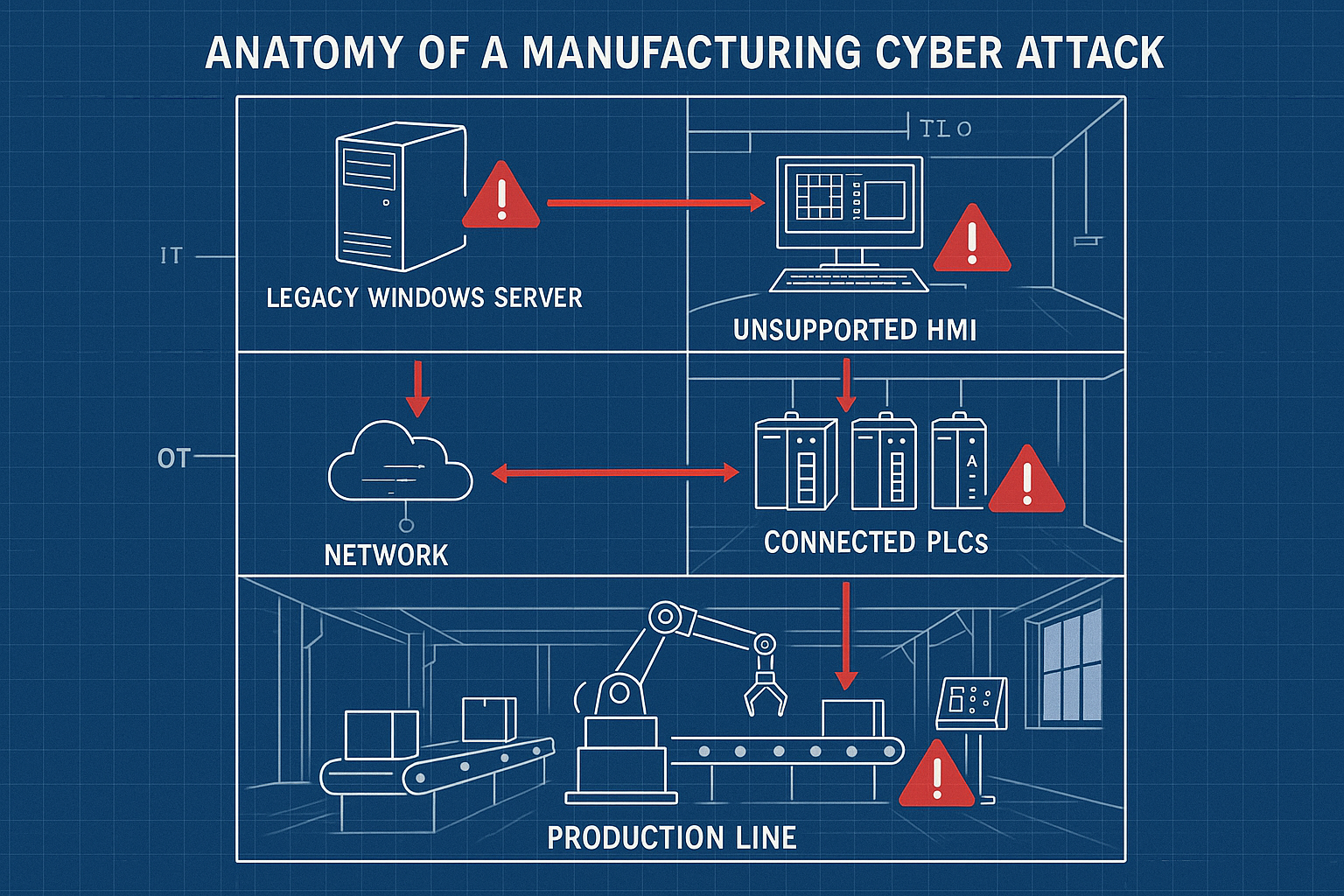
Challenge 3: Operational Technology (OT) Vulnerabilities
The Problem: When Factory Floor Meets Cybercrime
The convergence of Information Technology (IT) and Operational Technology (OT) has created unprecedented efficiency gains in manufacturing. But it’s also created new attack surfaces that many manufacturers don’t fully understand.
Consider this: That programmable logic controller (PLC) managing your assembly line might be running software that hasn’t been updated since Obama was president. But now it’s connected to your corporate network, and through that network, to the internet.
The Unique Challenges of OT Security
Legacy by Design: Many OT systems were designed for 20-30 year lifecycles with minimal maintenance. Security wasn’t a primary consideration when they were built.
Availability Requirements: You can’t just “patch and reboot” a system that controls a continuous manufacturing process. Downtime for updates often requires scheduled maintenance windows that may only occur quarterly or annually.
Specialized Knowledge: OT systems require specialized expertise that’s different from traditional IT security. Many cybersecurity professionals don’t understand industrial protocols like Modbus, DNP3, or Ethernet/IP.
Air Gap Illusion: Many manufacturers believe their OT networks are “air-gapped” and therefore secure. In reality, most modern facilities have multiple connection points between IT and OT networks.
Real-World OT Attack Scenarios
Scenario 1: The HMI Compromise
A human-machine interface (HMI) running unsupported Windows 7 becomes infected with malware through a USB drive. The malware spreads to connected PLCs, altering temperature controls in a chemical process and causing $3.2 million in product loss.
Scenario 2: The Remote Access Backdoor
An unsupported remote access solution used for equipment maintenance becomes the entry point for attackers who gain control of robotic systems, causing physical damage and safety incidents.
Scenario 3: The Historian Attack
Attackers compromise an unsupported data historian system, gaining access to production data, trade secrets, and customer information spanning several years.
The Solution: OT-Specific Security Framework
Securing OT environments requires a specialized approach:
Network Architecture:
– Implement proper network segmentation between IT and OT
– Deploy industrial firewalls and DMZs
– Monitor all IT/OT communication channels
Asset Management:
– Maintain comprehensive inventories of all OT devices
– Track software versions and support status
– Implement change management procedures
Monitoring and Detection:
– Deploy OT-specific security monitoring tools
– Establish baseline behavior patterns
– Implement anomaly detection for industrial protocols
Incident Response:
– Develop OT-specific incident response procedures
– Train response teams on industrial system impacts
– Establish communication protocols with operations teams
Challenge 4: Compliance and Regulatory Pressures
The Problem: When Unsupported Software Meets Regulatory Requirements
The regulatory landscape for manufacturing cybersecurity is evolving rapidly, and unsupported software is increasingly becoming a compliance liability. This is particularly challenging for Atlanta manufacturers who often serve multiple industries with different regulatory requirements.
Key Regulatory Frameworks Affecting Atlanta Manufacturers
NIST Cybersecurity Framework: While not mandatory for most manufacturers, it’s becoming the de facto standard for cybersecurity best practices. The framework explicitly requires organizations to maintain current, supported software systems.
FDA Requirements: Food and medical device manufacturers must comply with FDA cybersecurity guidance, which mandates supported software for systems that could impact product safety.
ITAR and Export Controls: Aerospace and defense manufacturers must protect controlled technical data, which requires current, supported security controls.
State and Local Regulations: Georgia’s data protection laws are becoming more stringent, with potential penalties for organizations that fail to implement reasonable security measures.
The Compliance Catch-22
Here’s where it gets tricky: Many manufacturers find themselves in a compliance catch-22 with legacy systems:
– Option A: Keep running unsupported software and risk compliance violations
– Option B: Upgrade systems and risk production disruptions during the transition
– Option C: Implement compensating controls that may be expensive and complex
The Solution: Compliance-Driven Modernization Strategy
The most successful approach I’ve seen combines compliance requirements with business modernization goals:
Step 1: Regulatory Mapping
– Identify all applicable regulations for your industry and customer base
– Map specific software requirements to your current systems
– Prioritize upgrades based on regulatory risk levels
Step 2: Compensating Controls
For systems that can’t be immediately upgraded:
– Implement network segmentation to isolate non-compliant systems
– Deploy additional monitoring and logging
– Establish documented risk acceptance procedures
– Create detailed remediation timelines
Step 3: Audit-Ready Documentation
– Maintain comprehensive software inventories
– Document all risk assessment and mitigation decisions
– Establish regular compliance review cycles
– Train staff on compliance requirements and procedures
Challenge 5: Supply Chain Vulnerabilities
The Problem: Your Security is Only as Strong as Your Weakest Supplier
Atlanta’s position as a major logistics and manufacturing hub means that local companies are deeply integrated into global supply chains. This interconnectedness creates a unique vulnerability: your unsupported software doesn’t just put your company at risk; it can impact your entire supply chain, and vice versa.
The SolarWinds Effect in Manufacturing
The 2020 SolarWinds attack taught us that supply chain cybersecurity isn’t just about physical components; it’s about software throughout the entire ecosystem. In manufacturing, this plays out in several ways:
Supplier Software Dependencies: Many manufacturers rely on supplier-provided software for everything from inventory management to quality control. If that software becomes unsupported, it creates risks for everyone in the chain.
Customer Requirements: Major OEMs are increasingly requiring their suppliers to maintain current, supported software systems as part of their vendor qualification processes.
Third-Party Integrations: Modern manufacturing involves numerous software integrations with suppliers, customers, and service providers. Unsupported software can break these integrations or create security gaps.
Real-World Supply Chain Scenarios
Case Study 1: The Automotive Ripple Effect
A Tier 2 automotive supplier in metro Atlanta suffered a ransomware attack through their unsupported ERP system. The attack didn’t just impact their operations; it forced three assembly plants to reduce production for two weeks while alternative suppliers were qualified and brought online.
Case Study 2: The Food Safety Incident
A food processing company’s unsupported quality management system was compromised, leading to falsified inspection records. The incident resulted in a product recall that affected 15 different food brands and caused $12 million in damages across the supply chain.
The Solution: Supply Chain Security Collaboration
Addressing supply chain vulnerabilities requires a collaborative approach:
Supplier Assessment Programs:
– Include software security requirements in vendor qualifications
– Conduct regular security assessments of critical suppliers
– Establish minimum standards for software support and patching
Information Sharing Initiatives:
– Participate in industry threat intelligence sharing
– Establish communication channels for security incidents
– Coordinate incident response across supply chain partners
Contractual Protections:
– Include cybersecurity requirements in supplier contracts
– Establish liability and insurance requirements
– Define incident notification and response procedures
Challenge 6: Skills and Resource Constraints
The Problem: The Cybersecurity Talent Gap Hits Manufacturing Hard
Even if manufacturers recognize the risks of unsupported software, many lack the internal expertise to address them effectively. The cybersecurity talent shortage is particularly acute in manufacturing, where specialized knowledge of both IT and OT systems is required.
The Numbers Don’t Add Up
According to recent industry data:
– 3.5 million cybersecurity jobs remain unfilled globally
– Manufacturing ranks 4th in cybersecurity talent shortage by industry
– Average time to fill a manufacturing cybersecurity role: 8.2 months
– Salary premium for manufacturing cybersecurity expertise: 23% above general IT security roles
Why Manufacturing Cybersecurity is Different
Manufacturing cybersecurity requires a unique skill set that combines:
Traditional IT Security: Network security, endpoint protection, incident response, compliance management
Operational Technology Knowledge: Understanding of industrial protocols, control systems, safety instrumented systems, and production processes
Business Operations: Knowledge of manufacturing processes, supply chain management, and quality systems
Regulatory Expertise: Understanding of industry-specific compliance requirements and standards
The Solution: Strategic Resource Planning
Smart manufacturers are addressing the skills gap through multiple approaches:
Build Internal Capabilities:
– Cross-train existing IT staff on OT security concepts
– Send operations staff to cybersecurity training programs
– Establish career development paths for cybersecurity roles
– Partner with local universities for internship and recruitment programs
Leverage External Expertise:
– Partner with specialized cybersecurity firms for gap areas
– Use managed security services for 24/7 monitoring
– Engage consultants for strategic planning and implementation
– Participate in industry consortia for shared learning
Technology Force Multipliers:
– Implement automated security tools to reduce manual workload
– Use security orchestration platforms to streamline processes
– Deploy AI-powered threat detection to augment human expertise
– Establish standardized procedures and playbooks
The Path Forward: Building Resilient Manufacturing Operations

Creating a Software Lifecycle Management Program
The most effective approach to addressing unsupported software vulnerabilities is to implement a comprehensive software lifecycle management program. This isn’t just about keeping software current; it’s about building organizational capability to manage technology risks proactively.
Essential Components of an Effective Program
Asset Discovery and Inventory:
– Automated discovery tools for both IT and OT environments
– Regular inventory updates and validation
– Integration with configuration management databases
– Risk scoring based on criticality and exposure
Lifecycle Planning:
– Vendor roadmap tracking and analysis
– End-of-life planning for all software assets
– Budget planning for upgrades and replacements
– Alternative solution evaluation and testing
Risk Assessment and Mitigation:
– Regular vulnerability assessments
– Threat modeling for critical systems
– Compensating control implementation
– Risk acceptance and documentation procedures
Change Management:
– Standardized procedures for software updates
– Testing and validation protocols
– Rollback procedures and emergency response
– Communication and coordination with operations teams
Building Organizational Resilience
Beyond technical measures, resilient manufacturing operations require organizational capabilities:
Executive Leadership: Senior leadership must understand and actively support cybersecurity initiatives, including budget allocation for software modernization.
Cross-Functional Collaboration: Effective cybersecurity requires close collaboration between IT, OT, operations, quality, and business teams.
Continuous Improvement: Regular assessment and improvement of security processes, with lessons learned from incidents and near-misses.
Culture of Security: Building awareness and accountability for cybersecurity throughout the organization, from the factory floor to the executive suite.
Emerging Trends and Future Considerations
The Evolution of Manufacturing Cybersecurity in 2025
As we move deeper into 2025, several trends are shaping the future of manufacturing cybersecurity:
AI-Powered Attacks: Cybercriminals are using artificial intelligence to identify and exploit vulnerabilities in unsupported software faster and more effectively than ever before.
Regulatory Acceleration: New regulations are being introduced at both state and federal levels, with increasing penalties for organizations that fail to maintain adequate cybersecurity controls.
Supply Chain Mandates: Major manufacturers are beginning to require cybersecurity certifications from their suppliers, making unsupported software a potential barrier to business opportunities.
Insurance Market Changes: Cyber insurance providers are becoming more selective, with some excluding coverage for incidents involving known unsupported software.
Preparing for What’s Next
Zero Trust Architecture: Moving beyond perimeter-based security to assume that all systems, including internal ones, could be compromised.
Software Bill of Materials (SBOM): Detailed inventories of all software components, including third-party libraries and dependencies, to enable better vulnerability management.
Quantum-Safe Cryptography: Preparing for the eventual arrival of quantum computing and its impact on current encryption methods.
Autonomous Security: AI-powered security systems that can detect, analyze, and respond to threats without human intervention.
Interactive Assessment Tool
🏭 Manufacturing Software Security Risk Assessment
Evaluate your organization's exposure to unsupported software vulnerabilities
Ready to Take IT Off Your Plate?
Stop worrying about downtime, security risks, or endless IT frustrations. AlphaCIS is the trusted IT partner for small and mid-sized businesses in Metro Atlanta, keeping systems secure, connected, and running the way they should every day.
Whether it’s preventing costly outages, protecting your data, or giving your team unlimited support, we make sure technology helps your business grow instead of holding it back.
📅 Book Your Free ConsultationConclusion: Taking Action Before It’s Too Late
The forgotten vulnerability of unsupported software isn’t really forgotten; it’s ignored. And in Atlanta’s competitive manufacturing landscape, that ignorance comes with a price tag that grows higher every day.
Throughout this article, we’ve explored how unsupported software creates invisible attack vectors, amplifies incident costs, complicates compliance efforts, and threatens supply chain relationships. But we’ve also seen that these challenges aren’t insurmountable. The manufacturers who are thriving in 2025 are those who’ve made the strategic decision to address these vulnerabilities proactively.
Your Next Steps Start Today
Immediate Actions (This Week):
- Conduct a rapid software inventory – You can’t protect what you don’t know exists
- Identify your highest-risk systems – Focus on unsupported software that’s internet-connected or handles critical data
- Document your current state – Create a baseline for measuring improvement
Short-Term Initiatives (Next 30 Days):
- Implement network segmentation – Isolate vulnerable systems while you plan upgrades
- Establish monitoring – Deploy tools to detect unusual activity on unsupported systems
- Create an upgrade roadmap – Prioritize replacements based on risk and business impact
Strategic Investments (Next 6-12 Months):
- Modernize critical systems – Replace or upgrade your highest-risk software
- Build internal capabilities – Train your team or partner with specialists
- Establish lifecycle management – Create processes to prevent future vulnerabilities
The Cost of Inaction
Remember the textile manufacturer I mentioned earlier? The one whose 6-hour attack cost $2.225 million? They’re now one of the most secure manufacturers in their sector, with a comprehensive software lifecycle management program and state-of-the-art security controls. But they learned their lessons the hard way.
You don’t have to.
The Competitive Advantage of Security
Forward-thinking manufacturers are discovering that cybersecurity isn’t just about risk reduction; it’s about competitive advantage. Companies with robust security programs are:
– Winning more contracts because customers trust them with sensitive data
– Reducing operational costs through improved efficiency and reduced downtime
– Attracting better talent who want to work for innovative, secure organizations
– Commanding premium pricing because security is increasingly a differentiator
The question isn’t whether you can afford to address unsupported software vulnerabilities. The question is whether you can afford not to.
In Atlanta’s manufacturing sector, the companies that survive and thrive will be those that view cybersecurity not as a cost center, but as a strategic enabler. The forgotten vulnerability of unsupported software represents both a significant risk and a tremendous opportunity.
The choice is yours. The time is now.
Ready to Take IT Off Your Plate?
Stop worrying about downtime, security risks, or endless IT frustrations. AlphaCIS is the trusted IT partner for small and mid-sized businesses in Metro Atlanta, keeping systems secure, connected, and running the way they should every day.
Whether it’s preventing costly outages, protecting your data, or giving your team unlimited support, we make sure technology helps your business grow instead of holding it back.
📅 Book Your Free Consultation
Dmitriy Teplinskiy
I have worked in the IT industry for 15+ years. During this time I have consulted clients in accounting and finance, manufacturing, automotive and boating, retail and everything in between. My background is in Networking and Cybersecurity



