Article Summary
• Who this is for: Small to mid-sized business owners who believe they’re “too small to be targeted” but rely heavily on digital systems, email, and customer data
• The challenge: Cybercriminals are increasingly targeting SMBs with AI-powered attacks, ransomware, and phishing—while most small businesses lack enterprise-level security, monitoring, and response capabilities
• Key insights covered: Why 43% of attacks now target small businesses, how AI and ransomware-as-a-service have changed the threat landscape, the true financial impact of breaches, and the most common attack vectors hitting SMBs in 2026
• Your outcome: A clear understanding of why your business is a prime target—and a practical, step-by-step action plan to reduce risk, strengthen defenses, and prevent costly downtime or permanent closure
Key Takeaways
• Small businesses face 43% of all cyberattacks in 2026, despite representing only 30% of the business landscape
• AI-powered attacks have made it easier for cybercriminals to target multiple SMBs simultaneously with sophisticated threats
• Limited cybersecurity budgets and lack of dedicated IT staff make small businesses attractive, low-resistance targets
• The average cost of a data breach for small businesses now exceeds $4.9 million, often forcing permanent closure
• Proactive cybersecurity measures and managed IT services provide the most cost-effective protection against evolving threats
Ready to Take IT Off Your Plate?
Stop worrying about downtime, security risks, or endless IT frustrations. AlphaCIS is the trusted IT partner for small and mid-sized businesses in Metro Atlanta, keeping systems secure, connected, and running the way they should every day.
Whether it’s preventing costly outages, protecting your data, or giving your team unlimited support, we make sure technology helps your business grow instead of holding it back.
📅 Book Your Free ConsultationQuick Answer
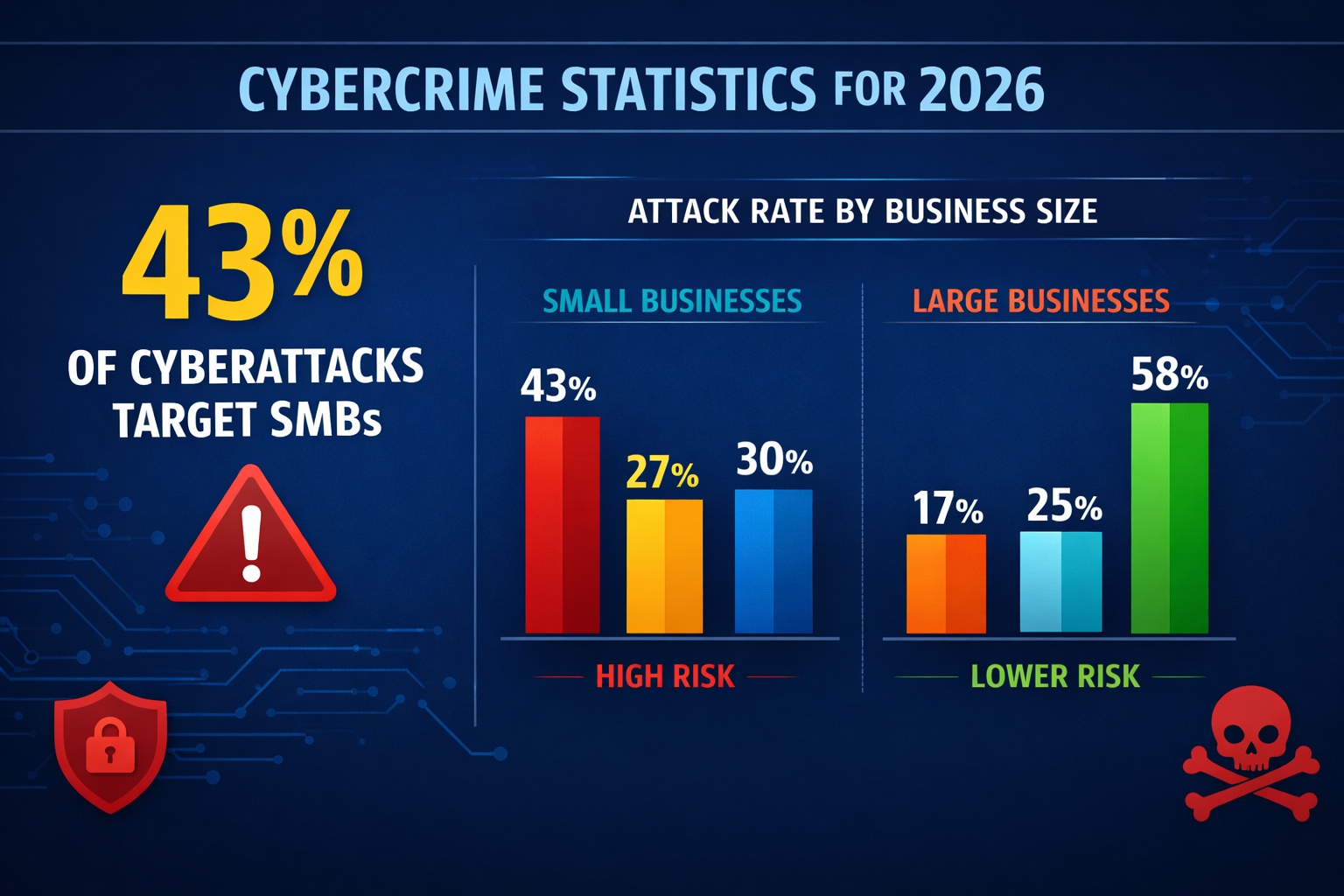
Small businesses have become the primary target for cyberattacks in 2026 because they typically have weaker security defenses, limited IT budgets, and valuable data, while being less likely to quickly detect sophisticated threats. Cybercriminals view SMBs as “low-hanging fruit”, easier to breach than large enterprises, but still containing valuable customer data, financial information, and business intelligence worth stealing or holding for ransom.
Last month, I received a frantic call from Sarah, who owns a dental practice in Marietta. Her entire patient management system was locked down by ransomware, and the attackers were demanding $50,000 to restore access to years of patient records. “I thought we were too small for hackers to notice,” she told me, her voice shaking.
Sarah’s story isn’t unique. Small businesses’ cyberattacks 2026 statistics show that cybercriminals are increasingly targeting SMBs over large enterprises. The landscape of SMB cyber threats in 2026 has evolved dramatically, with hackers utilizing AI-powered tools to launch sophisticated attacks against businesses that often lack the necessary resources to defend themselves effectively.
If you’re a small business owner reading this, you’re likely wondering why your company has become such an attractive target and what you can do about it. The reality is sobering: ransomware attacks on small businesses have increased by 78% since 2024, and phishing attacks on small companies are now more sophisticated than ever before.
But here’s the good news: understanding why hackers target small businesses is the first step toward protecting your company. With the right cybersecurity for small business strategies and potentially partnered with managed IT services for SMB, you can build defenses that rival those of much larger organizations.
Why Hackers Target Small Businesses: The Perfect Storm
Small businesses represent the ideal target for cybercriminals because they combine valuable assets with minimal security defenses. Think of it like this: if you’re a burglar, would you rather break into a house with multiple security systems and guards, or one with a basic lock and no alarm? The choice is obvious.
Here’s what makes small businesses so attractive to cybercriminals:
Limited Security Infrastructure
Most small businesses operate with basic antivirus software and maybe a firewall if they’re lucky. Unlike large corporations that invest millions in cybersecurity, SMBs often rely on consumer-grade protection that’s easily bypassed by modern attack methods.
Valuable Data Without Protection
Small businesses collect the same types of valuable information as large enterprises: customer data, financial records, employee information, and business intelligence. However, they rarely have the same level of data protection and monitoring systems in place.
Human Factor Vulnerabilities
With limited IT training budgets, small business employees are more likely to fall victim to social engineering attacks. A single clicked link or downloaded attachment can compromise an entire network when proper security awareness training isn’t in place.
Delayed Detection
Large enterprises have 24/7 security operations centers monitoring for threats. Small businesses might not discover a breach for weeks or months, giving attackers plenty of time to steal data or establish persistent access.
The numbers don’t lie. Small business cybersecurity statistics reveal that 60% of SMBs go out of business within six months of experiencing a significant cyberattack. This isn’t just about money, it’s about survival.
The Evolution of SMB Cyber Threats in 2026

The cybercrime landscape has fundamentally changed, with AI and automation making it easier than ever for attackers to target multiple small businesses simultaneously. Gone are the days when cybercriminals needed extensive technical knowledge or significant resources to launch sophisticated attacks.
AI-Powered Attack Automation
Cybercriminals now use artificial intelligence to scan for vulnerabilities across thousands of small business networks simultaneously. These automated tools can identify weak points, craft personalized phishing emails, and even adapt attack strategies in real-time based on a target’s responses.
Ransomware-as-a-Service (RaaS)
The criminal ecosystem has become industrialized. Cybercrime groups now offer “ransomware-as-a-service,” allowing even novice criminals to launch sophisticated attacks against small businesses. This has dramatically lowered the barrier to entry for cybercrime.
Supply Chain Targeting
Attackers have realized that compromising one small business can provide access to their larger clients. A small accounting firm might serve dozens of other businesses, making it a gateway to multiple targets through a single breach.
Cryptocurrency and Anonymous Payments
The rise of cryptocurrency has made it easier for criminals to receive ransom payments without being traced. This has emboldened attackers to target smaller businesses, knowing they can collect payments anonymously.
Here’s a real example from our experience: A small manufacturing company in Gwinnett County was targeted by an AI-powered phishing campaign that sent personalized emails to 15 different employees over three days. The emails were so convincing that they referenced specific projects and vendor relationships. It was only because they had implemented our managed security awareness training that the attack was stopped.
Common Types of Attacks Targeting Small Businesses
Ransomware attacks on small businesses have become the most financially devastating threat, but they’re far from the only concern. Understanding the full spectrum of threats helps you prepare appropriate defenses.
Ransomware: The Business Killer
Ransomware encrypts your business files and demands payment for the decryption key. For small businesses, this often means:
- Complete operational shutdown
- Loss of customer data and trust
- Regulatory compliance violations
- Potential permanent closure
The average ransom demand for small businesses has increased to $84,000 in 2026, but the total cost, including downtime, recovery, and reputation damage, often exceeds $500,000.
Phishing: The Gateway Attack
Phishing attacks on small companies have become incredibly sophisticated. Modern phishing campaigns include:
- Spear phishing: Highly targeted emails referencing specific business relationships
- Business Email Compromise (BEC): Impersonating executives to authorize fraudulent payments
- Voice phishing (vishing): Phone calls impersonating vendors or service providers
- SMS phishing (smishing): Text messages directing victims to malicious websites
Data Theft and Espionage
Small business data breaches often go unnoticed for months, while attackers:
- Steal customer databases for resale
- Monitor email communications for business intelligence
- Access financial systems for fraudulent transactions
- Gather information for future, more targeted attacks
Insider Threats
Whether malicious or accidental, insider threats pose unique risks to small businesses:
- Disgruntled employees with system access
- Contractors with temporary but extensive permissions
- Accidental data exposure through misconfigured systems
- Social engineering targeting employees with elevated access
I remember working with a small law firm that discovered an ex-employee had been accessing client files for months after termination because no one had disabled their remote access credentials. The potential liability was enormous, and it highlighted how small oversights can create massive vulnerabilities.
The True Cost of Cyberattacks for Small Businesses
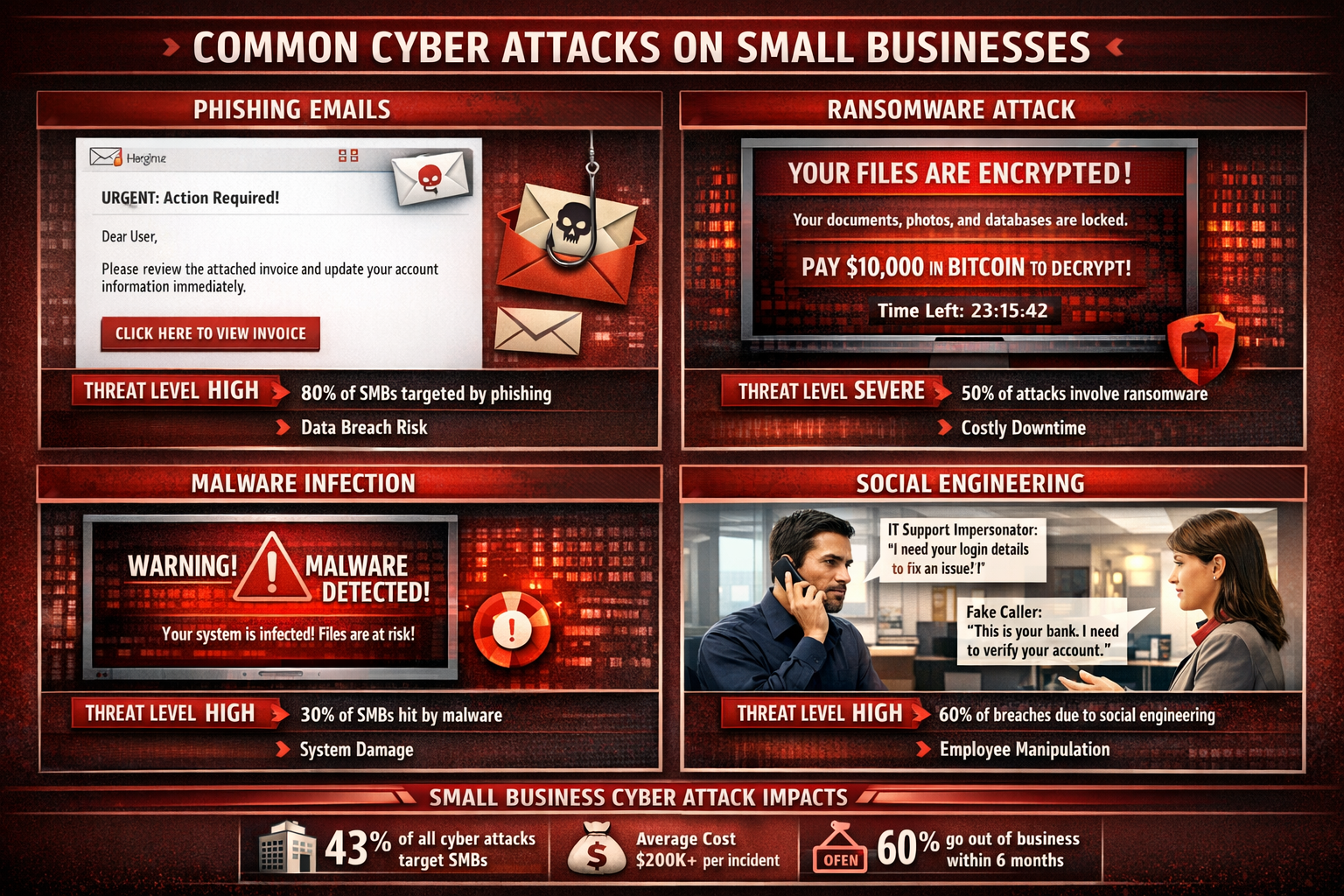
The financial impact of small business data breaches extends far beyond the immediate ransom payment or system recovery costs. When we break down the true cost, it becomes clear why cybersecurity for small businesses isn’t just an IT expense – it’s business survival insurance.
Direct Financial Costs
- Ransom payments: Average of $84,000 in 2026
- System recovery: $15,000-$50,000 for professional incident response
- Lost productivity: $2,000-$5,000 per day of downtime
- Legal fees: $25,000-$100,000 for breach notification and compliance
- Regulatory fines: Up to $50,000 for HIPAA violations, more for other regulations
Hidden Business Costs
- Customer churn: 30-40% of customers may leave after a publicized breach
- Reputation damage: Years of marketing efforts destroyed overnight
- Insurance premium increases: Cyber insurance rates often double after a claim
- Lost business opportunities: Prospects avoid companies with security issues
- Employee turnover: Staff stress and uncertainty following incidents
Long-term Impact
The most devastating aspect isn’t the immediate cost – it’s the long-term business impact. Consider these sobering statistics:
- 29% of small businesses never fully recover their pre-breach revenue levels
- Average recovery time is 18-24 months for full operational restoration
- Customer acquisition costs increase by 40-60% post-breach due to reputation damage
Let me share a story that illustrates this perfectly. We worked with a small healthcare clinic that experienced a ransomware attack in early 2025. The direct costs were manageable – about $35,000 for system recovery and legal compliance. But the real damage came later: they lost 40% of their patients within six months, had to lay off three staff members, and are still struggling to rebuild their reputation. The total business impact exceeded $400,000.
Prevention vs. Recovery: The Math is Clear
Here’s the comparison that every small business owner should see:
| Prevention Cost (Annual) | Breach Recovery Cost |
|---|---|
| Managed cybersecurity: $3,000-$8,000 | Average total cost: $490,000 |
| Employee training: $500-$1,500 | Lost revenue: $200,000+ |
| Backup solutions: $1,200-$3,600 | Legal/compliance: $50,000+ |
| Total Prevention: $4,700-$13,100 | Total Recovery: $740,000+ |
The return on investment for cybersecurity is clear: every dollar spent on prevention saves approximately $50-60 in potential breach costs.
Building Your Small Business Cybersecurity Defense
Effective cybersecurity for small businesses doesn’t require an enterprise-level budget, but it does require a strategic approach that addresses your most critical vulnerabilities first. The key is implementing layered security that provides maximum protection for your investment.
Essential Security Foundations
1. Professional-Grade Endpoint Protection
Consumer antivirus isn’t enough anymore. You need business-grade endpoint detection and response (EDR) that can:
- Detect and block advanced malware
- Monitor for suspicious behavior patterns
- Provide real-time threat intelligence
- Automatically isolate infected devices
2. Network Security and Monitoring
Your network perimeter needs professional protection:
- Next-generation firewalls with intrusion detection
- Network monitoring to spot unusual activity
- Secure Wi-Fi with proper guest network isolation
- VPN access for remote workers
3. Email Security Solutions
Since 90% of attacks start with email, this is critical:
- Advanced threat protection beyond basic spam filtering
- Link and attachment scanning with sandboxing
- Business email compromise protection
- Encryption for sensitive communications
4. Data Backup and Recovery
The best ransomware defense is reliable backups:
- Automated daily backups with multiple restore points
- Offsite storage that’s disconnected from your network
- Regular restore testing to ensure backups actually work
- Recovery time objectives of 4 hours or less
Human Factor Security
Employee Security Awareness Training
Your team is both your biggest vulnerability and your strongest defense:
- Monthly training modules on current threats
- Simulated phishing tests to identify at-risk employees
- Incident reporting procedures that encourage transparency
- Security policies that are actually followed
Access Control and Management
Limit damage potential through proper access controls:
- Multi-factor authentication on all business systems
- Principle of least privilege – minimum necessary access only
- Regular access reviews and prompt deprovisioning
- Privileged account monitoring for administrative access
I worked with a small accounting firm that implemented these basics and caught three separate attack attempts in their first year. The security awareness training alone prevented a $75,000 wire fraud attempt when an employee recognized a suspicious email requesting a client payment redirect.
The Role of Managed IT Services in SMB Cybersecurity
For most small businesses, achieving enterprise-level cybersecurity requires partnering with managed IT services for SMB that specialize in security. The reality is that cybersecurity has become too complex and time-sensitive for most small businesses to handle entirely in-house.
Why Managed Security Makes Sense
24/7 Monitoring and Response
Cyber threats don’t respect business hours. Professional managed security services provide:
- Continuous network monitoring for suspicious activity
- Real-time threat detection and automated response
- Security incident escalation to human experts when needed
- After-hours support when attacks occur outside business hours
Access to Enterprise-Grade Tools
Managed service providers can offer small businesses access to security tools that would be prohibitively expensive to license individually:
- Security information and event management (SIEM) platforms
- Advanced threat intelligence feeds
- Professional vulnerability scanning and assessment
- Compliance monitoring and reporting tools
Expertise and Experience
Cybersecurity expertise is expensive and hard to find. Managed services provide:
- Certified security professionals with specialized training
- Experience across multiple industries and attack scenarios
- Vendor relationships for rapid incident response
- Regulatory compliance expertise for healthcare, finance, and other regulated industries
Cost-Effective Scaling
Instead of hiring full-time security staff (average salary $85,000+), you get access to an entire security team for a fraction of the cost.
What to Look for in Managed IT Services
When evaluating managed IT services for SMB cybersecurity, focus on providers that offer:
Proactive Security Management
- Regular vulnerability assessments and patch management
- Continuous security monitoring and alerting
- Incident response planning and testing
- Security awareness training for your team
Industry Expertise
- Experience with businesses similar to yours
- Understanding of industry-specific compliance requirements
- References from satisfied clients in your sector
- Local presence for on-site support when needed
Transparent Pricing and Service Levels
- Clear service level agreements with response time guarantees
- Straightforward pricing without hidden fees
- Regular reporting on security posture and incidents
- Scalable services that grow with your business
Here in Metro Atlanta, we’ve seen too many small businesses struggle with IT providers who treat cybersecurity as an afterthought. The difference between a true security-focused managed service provider and a basic IT support company can literally mean the difference between business survival and closure.
Cybercrime Trends 2026: What’s Coming Next
The cybercrime landscape continues evolving rapidly, and understanding emerging cybercrime trends 2026 helps small businesses prepare for tomorrow’s threats today. Staying ahead of these trends isn’t just about technology; it’s about business survival in an increasingly connected world.
AI-Driven Attack Sophistication
Artificial intelligence is revolutionizing cybercrime in ways that particularly impact small businesses:
Deepfake Social Engineering
Criminals now use AI to create convincing audio and video of executives requesting wire transfers or sensitive information. A small business might receive a “video call” from its bank manager requesting account verification, when it’s actually an AI-generated deepfake.
Automated Vulnerability Discovery
AI tools can scan thousands of small business networks simultaneously, identifying specific vulnerabilities and crafting targeted attacks faster than human security teams can respond.
Personalized Phishing at Scale
Machine learning analyzes social media, business websites, and public records to create highly personalized phishing emails that reference specific vendors, projects, and relationships.
Supply Chain and Third-Party Risks
Small businesses are increasingly targeted as entry points to larger organizations:
Vendor Email Compromise
Attackers compromise small vendor email accounts to send malicious invoices or requests to larger clients. A small marketing agency’s compromised email might be used to attack its Fortune 500 clients.
Software Supply Chain Attacks
Criminals target small software vendors or service providers to inject malware into updates that then spread to all their business customers.
Cloud Service Exploitation
As more small businesses move to cloud services, attackers focus on compromising cloud credentials to access multiple business environments through a single breach.
Regulatory and Compliance Evolution
New regulations are increasing the compliance burden on small businesses:
State Privacy Laws
More states are implementing California-style privacy laws that apply to small businesses processing personal information, with significant penalties for non-compliance.
Cyber Insurance Requirements
Insurance companies are requiring specific cybersecurity measures before providing coverage, effectively mandating certain security standards for small businesses.
Industry-Specific Regulations
Healthcare, finance, and other regulated industries are seeing increased enforcement and higher penalties for small business violations.
The key insight here is that cybersecurity is no longer optional for any business – it’s become a basic requirement for operating in the modern economy.
Creating Your Cybersecurity Action Plan
Every small business needs a practical, step-by-step cybersecurity action plan that addresses immediate vulnerabilities while building long-term resilience. Here’s how to get started, regardless of your current security posture or budget constraints.
Phase 1: Immediate Risk Reduction (First 30 Days)
Week 1: Critical Account Security
- Enable multi-factor authentication on all business email accounts
- Change default passwords on routers, printers, and other network devices
- Review and update admin access to all business systems
- Install a reputable business antivirus on all computers
Week 2: Email and Communication Security
- Implement email filtering to block phishing attempts
- Train employees to verify unusual requests by phone before acting
- Set up automatic software updates for operating systems
- Create an incident response contact list
Week 3: Data Protection Basics
- Identify your most critical business data and where it’s stored
- Set up automated backups for essential files and systems
- Test backup restoration to ensure it actually works
- Remove unnecessary software and close unused accounts
Week 4: Network Security Foundation
- Change default Wi-Fi passwords and enable WPA3 encryption
- Set up a separate guest network for visitors
- Document all devices connected to your network
- Schedule a professional security assessment
Phase 2: Building Robust Defenses (Months 2-3)
Advanced Threat Protection
- Deploy business-grade endpoint detection and response tools
- Implement network monitoring and intrusion detection
- Set up email encryption for sensitive communications
- Establish secure remote access procedures
Employee Security Program
- Launch a formal security awareness training program
- Conduct simulated phishing tests to identify vulnerabilities
- Create clear security policies and incident reporting procedures
- Implement regular security check-ins during team meetings
Compliance and Documentation
- Document your cybersecurity policies and procedures
- Ensure compliance with industry-specific regulations
- Review cyber insurance coverage and requirements
- Create an incident response plan with clear roles and responsibilities
Phase 3: Ongoing Security Management (Month 4+)
Continuous Monitoring
- Implement 24/7 security monitoring or partner with a managed service provider
- Schedule regular vulnerability assessments and penetration testing
- Maintain current threat intelligence and security updates
- Review and update security policies quarterly
Business Continuity Planning
- Develop and test disaster recovery procedures
- Create communication plans for security incidents
- Establish relationships with cybersecurity incident response professionals
- Regularly review and update cyber insurance coverage
One of our clients, a small law firm, followed this exact plan after experiencing a minor security incident. Within six months, they had transformed from having basic consumer-grade protection to maintaining security standards that exceeded many firms twice their size. The investment was less than $15,000 annually, but it provided peace of mind worth far more than that.
Frequently Asked Questions
Q: How much should a small business spend on cybersecurity?
A: Most small businesses should budget 3-5% of their annual revenue for cybersecurity, including tools, training, and professional services. For a business with $1 million in annual revenue, this means $30,000-$50,000 per year – far less than the average cost of a single data breach.
Q: Can small businesses really be as secure as large enterprises?
A: Yes, but it requires the right approach. Small businesses can achieve enterprise-level security by partnering with managed service providers who provide access to advanced tools and expertise that would be too expensive to maintain in-house.
Q: What’s the most important cybersecurity investment for a small business?
A: Employee security awareness training provides the highest return on investment. Since 90% of successful attacks involve human error, properly trained employees are your strongest defense against cyber threats.
Q: How quickly can cybercriminals compromise a small business network?
A: Modern automated attacks can compromise poorly protected networks in minutes. However, the average time from initial compromise to data theft or ransomware deployment is 2-4 weeks, which provides a window for detection and response.
Q: Do cyber insurance policies actually pay out for small businesses?
A: Yes, but policies often require specific cybersecurity measures to be in place. Many claims are denied because businesses didn’t meet basic security requirements outlined in their policy terms.
Q: Should small businesses pay ransomware demands?
A: Security experts and law enforcement strongly advise against paying ransoms. Payment doesn’t guarantee data recovery, encourages future attacks, and may violate sanctions laws. Focus on prevention and backup strategies instead.
Q: How often should small businesses update their cybersecurity measures?
A: Security tools should be updated automatically and continuously. Policies and procedures should be reviewed quarterly, with annual comprehensive security assessments to identify new vulnerabilities and threats.
Q: What’s the difference between antivirus and endpoint protection?
A: Traditional antivirus software only detects known malware signatures. Modern endpoint protection uses behavioral analysis and machine learning to detect unknown threats, provides network monitoring, and can automatically respond to incidents.
Q: Can a small business handle cybersecurity entirely in-house?
A: While possible, it’s increasingly difficult due to the complexity of modern threats and the 24/7 nature of cybersecurity. Most successful small businesses combine basic in-house capabilities with professionally managed security services.
Q: What should a small business do immediately after discovering a cyberattack?
A: Disconnect affected systems from the network, contact your incident response team or managed service provider, preserve evidence, notify relevant authorities if required, and begin executing your incident response plan.
Q: How can small businesses stay informed about new cyber threats?
A: Subscribe to threat intelligence feeds from organizations like CISA, maintain relationships with cybersecurity professionals, participate in industry security groups, and ensure your managed service provider provides regular threat briefings.
Q: Are cloud services safer than on-premises systems for small businesses?
A: Major cloud providers typically offer better security than most small businesses can implement on-premises, but proper configuration and access management are critical. Many breaches involve misconfigured cloud services rather than provider security failures.
Key Takeaways: Protecting Your Small Business in 2026
• Small businesses face unprecedented cyber risks, with 43% of all attacks targeting SMBs despite their limited security resources and expertise
• AI-powered cybercrime tools have made sophisticated attacks accessible to low-skill criminals, increasing both the frequency and effectiveness of threats against small businesses
• The true cost of cyberattacks extends far beyond ransom payments – including lost revenue, reputation damage, regulatory fines, and potential business closure within six months
• Prevention costs 50-60 times less than recovery – investing $5,000-$15,000 annually in cybersecurity can prevent losses exceeding $500,000 from a single incident
• Employee training provides the highest ROI since 90% of successful attacks involve human error, making security awareness your strongest defense
• Managed IT services offer enterprise-level protection at small business prices, providing 24/7 monitoring, expert response, and access to advanced security tools
• Layered security approaches work best – combining endpoint protection, network monitoring, email security, backup systems, and employee training creates multiple barriers against attacks
• Compliance requirements are increasing across all industries, making cybersecurity not just a business protection issue but a legal requirement
• Cyber insurance requires proactive security measures – insurers now mandate specific cybersecurity implementations before providing coverage
• Regular security assessments and updates are essential as the threat landscape evolves rapidly with new attack methods emerging monthly
The bottom line is clear: cybersecurity isn’t an IT expense – it’s business survival insurance. In 2026, small businesses can no longer afford to hope they won’t be targeted. The question isn’t whether you’ll face a cyber threat, but whether you’ll be prepared when it happens.
Your business deserves the same level of protection as large enterprises, and with the right approach and partnerships, that level of security is both achievable and affordable. The peace of mind that comes from knowing your business is protected allows you to focus on what you do best – growing your company and serving your customers.
Don’t wait until you’re dealing with a ransomware demand or explaining a data breach to your customers. Take action today to protect your business, your employees, and your customers from becoming the next cybercrime statistic.
Ready to transform your cybersecurity from a worry into a competitive advantage? Contact our team for a free security assessment and discover how we can provide the industry expertise and proactive solutions that give you complete peace of mind.
Ready to Take IT Off Your Plate?
Stop worrying about downtime, security risks, or endless IT frustrations. AlphaCIS is the trusted IT partner for small and mid-sized businesses in Metro Atlanta, keeping systems secure, connected, and running the way they should every day.
Whether it’s preventing costly outages, protecting your data, or giving your team unlimited support, we make sure technology helps your business grow instead of holding it back.
📅 Book Your Free ConsultationConclusion: Building Your Secure Hybrid Future

Securing a hybrid and remote workforce doesn’t have to be overwhelming. By following your MSP checklist for securing hybrid and remote workforces, you’re taking a systematic approach that addresses the most critical security challenges facing modern businesses.
Remember, security isn’t a destination; it’s an ongoing journey. The threat landscape continues to evolve, and your security measures need to evolve with it. The good news is that with the right foundation in place, maintaining and improving your security posture becomes much more manageable.
The key is to start with a comprehensive assessment, implement the essential protections we’ve discussed, and partner with experienced professionals who understand the unique challenges of hybrid work environments. You don’t have to navigate this alone.
Your Next Steps
- Conduct a security assessment using the interactive checklist above to identify your current gaps
- Prioritize critical vulnerabilities that pose the highest risk to your business operations
- Implement foundational protections like MFA, endpoint security, and secure network connections
- Establish monitoring and response procedures to detect and address threats quickly
- Create ongoing maintenance schedules for updates, training, and compliance reviews
The businesses that thrive in our hybrid work world are those that take proactive steps to secure their operations. Don’t wait for a security incident to force your hand. Take action now to protect your business, your employees, and your customers.
Ready to Secure Your Business with Confidence?
Stop worrying about security gaps and start focusing on growing your business. Our team provides industry expertise, same-day support, and 24/7 monitoring to keep your hybrid workforce secure and compliant. With straightforward pricing and personalized service, we’ll help you implement these security measures without the IT headaches.
Contact AlphaCIS today for your complimentary security consultation and discover how we can become your trusted partner in creating a secure, productive hybrid work environment.
Small Business Cybersecurity Risk Assessment
Evaluate your current security posture and get personalized recommendations
1. How many employees does your business have?
2. Do you have multi-factor authentication enabled on business accounts?
3. How often do you provide cybersecurity training to employees?
4. What type of backup system do you currently use?
5. Do you have dedicated IT support or cybersecurity expertise?
6. How do you handle software updates and patches?
Ready to Take IT Off Your Plate?
Stop worrying about downtime, security risks, or endless IT frustrations. AlphaCIS is the trusted IT partner for small and mid-sized businesses in Metro Atlanta, keeping systems secure, connected, and running the way they should every day.
Whether it’s preventing costly outages, protecting your data, or giving your team unlimited support, we make sure technology helps your business grow instead of holding it back.
📅 Book Your Free Consultation
Dmitriy Teplinskiy
I have worked in the IT industry for 15+ years. During this time I have consulted clients in accounting and finance, manufacturing, automotive and boating, retail and everything in between. My background is in Networking and Cybersecurity