Picture this: It’s 3 AM on a Tuesday, and your entire production line has ground to a halt. The smart sensors you installed six months ago to boost efficiency are now completely offline, and nobody knows why. Your IT team is scrambling to figure out what went wrong, but here’s the kicker they weren’t involved in the IoT deployment from the start. Sound familiar?
If you’re a manufacturing leader who’s been tempted to fast-track IoT implementation without proper IT oversight, you’re not alone. The promise of instant efficiency gains and real-time insights can make anyone want to skip the “boring” IT stuff. But here’s what I’ve learned after watching countless manufacturers learn this lesson the hard way: Industrial IoT without IT oversight is a disaster waiting to happen.
Key Takeaways

Ready to Take IT Off Your Plate?
Stop worrying about downtime, security risks, or endless IT frustrations. AlphaCIS is the trusted IT partner for small and mid-sized businesses in Metro Atlanta, keeping systems secure, connected, and running the way they should every day.
Whether it’s preventing costly outages, protecting your data, or giving your team unlimited support, we make sure technology helps your business grow instead of holding it back.
📅 Book Your Free Consultation- Security vulnerabilities multiply exponentially when IoT devices are deployed without proper IT governance and network segmentation
- Data integrity and reliability suffer without standardized protocols and centralized management systems
- Integration nightmares emerge when IoT solutions aren’t designed with existing IT infrastructure in mind
- Compliance risks skyrocket in regulated industries without proper documentation and security frameworks
- Long-term scalability becomes impossible without strategic IT planning and architecture design
The Hidden Dangers of Going Rogue with IoT
Challenge 1: Security Becomes Your Achilles’ Heel
Let me tell you about a mid-sized automotive parts manufacturer I worked with last year. They were so excited about their new IoT-enabled quality control sensors that they bypassed their IT department entirely. The operations team plugged these devices directly into their network, thinking they were being proactive.
Why This Matters:
– Each unmanaged IoT device becomes a potential entry point for cybercriminals
– Manufacturing networks often contain sensitive intellectual property and customer data
– A single compromised sensor can provide access to your entire operational technology (OT) network
The Reality Check:
Without IT oversight, you’re essentially leaving your digital front door wide open. Industrial IoT devices often ship with default passwords, outdated firmware, and minimal security features. When your IT team isn’t involved, these vulnerabilities go unaddressed.
The Solution:
Implement a zero-trust network architecture where every IoT device is:
– Authenticated before network access
– Segmented into isolated network zones
– Continuously monitored for unusual behavior
– Regularly updated with security patches
Challenge 2: Data Chaos Replaces Data Insights
Here’s something that might surprise you: having more data doesn’t automatically mean having better insights. I’ve seen manufacturers collect terabytes of sensor data that becomes completely useless because there’s no standardized way to process, store, or analyze it.
The Problem:
When IT isn’t involved in IoT planning, you end up with:
– Incompatible data formats across different devices
– No centralized data storage strategy
– Unreliable data transmission protocols
– Zero data backup and recovery plans
Real-World Impact:
One food processing company I consulted for had installed temperature sensors throughout their facility. Six months later, they discovered that 30% of their data was corrupted due to network interference, and they had no way to recover the lost information. Their quality compliance reports became unreliable, putting their certifications at risk.
The IT-Driven Solution:
– Establish data governance policies before deployment
– Implement edge computing solutions for real-time processing
– Create standardized APIs for seamless data integration
– Set up automated backup systems with redundancy
Challenge 3: Integration Nightmares That Never End
Nothing kills IoT enthusiasm faster than discovering your shiny new sensors can’t talk to your existing systems. Without IT oversight, this scenario plays out in manufacturing facilities across the globe every single day.
Common Integration Failures:
– IoT data can’t connect to your ERP system
– Sensors use protocols incompatible with your SCADA systems
– No unified dashboard for monitoring all devices
– Manual data entry becomes necessary (defeating the automation purpose)
The Domino Effect:
When integration fails, you don’t just lose efficiency, you often end up less efficient than before. Operators spend time troubleshooting connectivity issues instead of focusing on production. Maintenance teams can’t access the predictive insights they need. Quality control becomes reactive instead of proactive.
IoT Security Risk Assessment
Evaluate your current Industrial IoT security posture
Recommended Actions:
Ready to Take IT Off Your Plate?
Stop worrying about downtime, security risks, or endless IT frustrations. AlphaCIS is the trusted IT partner for small and mid-sized businesses in Metro Atlanta, keeping systems secure, connected, and running the way they should every day.
Whether it’s preventing costly outages, protecting your data, or giving your team unlimited support, we make sure technology helps your business grow instead of holding it back.
📅 Book Your Free Consultation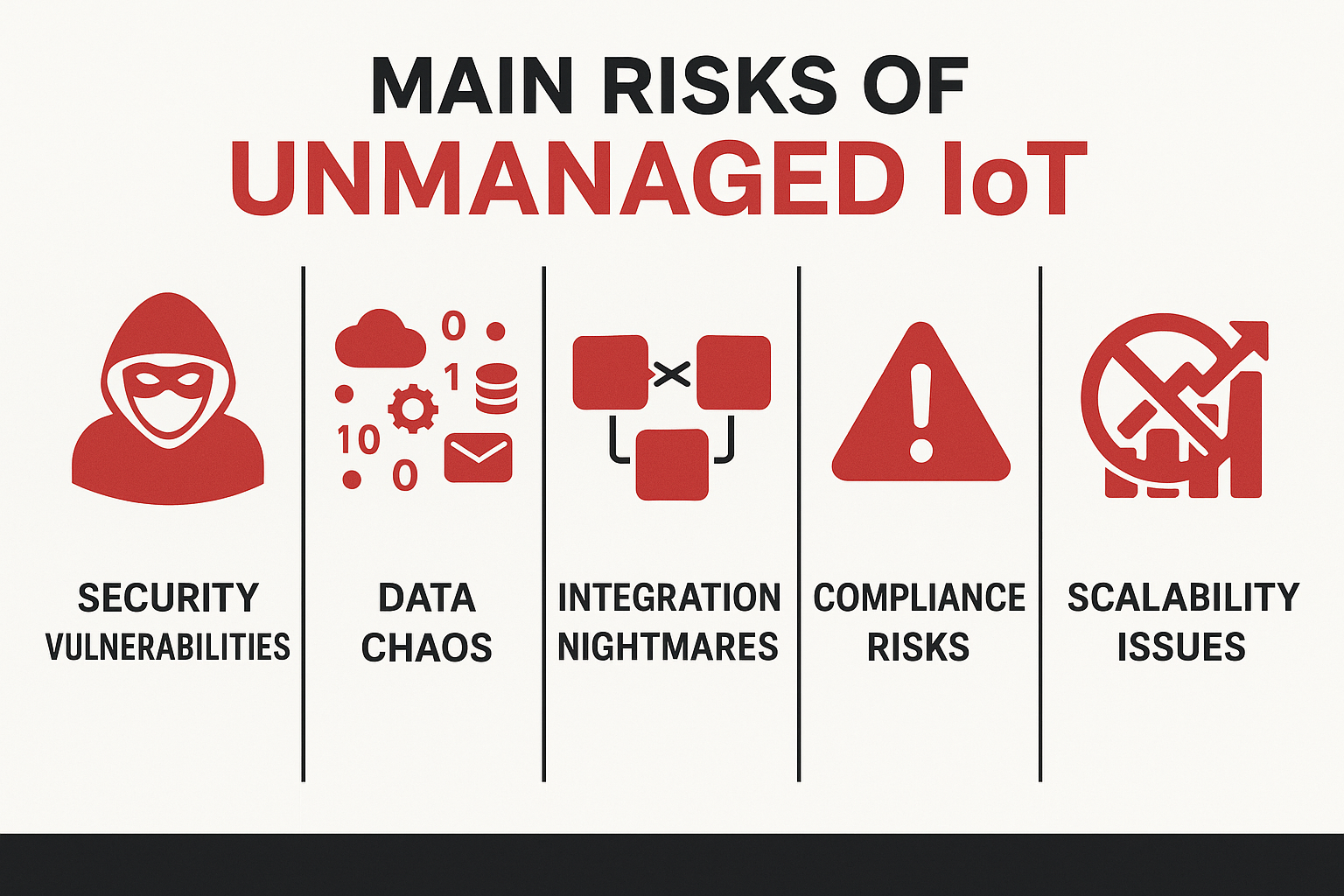
Challenge 4: Compliance Becomes a Moving Target
If you’re in a regulated industry, and let’s face it, most manufacturing is compliance isn’t optional. It’s the difference between staying in business and facing hefty fines or shutdowns.
The Compliance Trap:
Without IT oversight, you’re flying blind when it comes to:
– Data retention requirements (How long must you keep sensor data?)
– Audit trails (Who accessed what data and when?)
– Data sovereignty (Where is your data being stored and processed?)
– Privacy regulations (How are you protecting personally identifiable information?)
A Real-World Warning:
A pharmaceutical manufacturer I worked with faced a surprise FDA audit. They had implemented IoT sensors to monitor environmental conditions in their cleanrooms, but without proper IT documentation, they couldn’t prove data integrity. The result? A six-month production halt while they rebuilt their entire monitoring system with proper oversight.
The IT-First Approach:
– Document everything from the start with proper change management
– Implement role-based access controls for all IoT systems
– Create automated compliance reporting with real-time monitoring
– Establish data lineage tracking for full audit transparency
Challenge 5: Scalability Hits a Brick Wall
Here’s what nobody tells you about DIY IoT deployments: they work great until they don’t. What starts as a small pilot project with a few sensors quickly becomes an unmanageable mess when you try to scale.
The Scalability Nightmare:
– Network congestion as more devices come online
– Incompatible systems that can’t communicate with each other
– Performance degradation affecting critical operations
– Management overhead that grows exponentially with each new device
Why IT Oversight Prevents This:
IT professionals think in terms of architecture, not just individual devices. They consider:
– Bandwidth requirements for current and future deployments
– Interoperability standards that ensure long-term compatibility
– Performance monitoring to identify bottlenecks before they impact production
– Upgrade pathways that protect your investment as technology evolves
The Cost of Getting It Wrong
Let me share some sobering statistics that highlight why Industrial IoT without IT oversight is a disaster waiting to happen:
| Risk Category | Average Cost Impact | Recovery Time |
| Security Breach | $3.8M per incident | 6-12 months Data Loss |
| Data Loss | $1.2M per event | 3-6 months |
| Compliance Violation | $500K-$10M in fines | 12-24 months |
| System Downtime | $50K per hour | 24-72 hours |
| Integration Failure | $200K in rework | 2-4 months |
The Hidden Costs Nobody Talks About:
– Opportunity cost of delayed insights and optimization
– Employee frustration and reduced productivity
– Customer confidence erosion due to quality issues
– Competitive disadvantage while you’re fixing problems instead of innovating
Building the Right Foundation: IT-Led IoT Success
Now that we’ve covered the disasters that happen without IT oversight, let’s talk about what success looks like when you do it right.
The IT-First Framework
1. Strategic Planning Phase
– Conduct a comprehensive network assessment
– Define clear security requirements and protocols
– Establish data governance policies
– Create integration roadmaps for existing systems
2. Pilot Implementation
– Start small with critical success metrics
– Test security protocols under real conditions
– Validate data quality and integration points
– Document lessons learned for scaling
3. Controlled Scaling
– Implement robust monitoring and alerting
– Establish automated update and patch management
– Create redundancy and failover procedures
– Train operations teams on new processes
4. Continuous Optimization
– Regular security assessments and updates
– Performance monitoring and capacity planning
– Compliance auditing and reporting
– Technology refresh planning
Essential IT Oversight Components
Network Architecture:
– Segmented networks that isolate IoT traffic
– Quality of Service (QoS) rules that prioritize critical data
– Redundant connections for high-availability requirements
– Edge computing capabilities for real-time processing
Security Framework:
– Multi-factor authentication for all device access
– Certificate-based device authentication
– Intrusion detection systems specifically tuned for IoT traffic
– Regular penetration testing and vulnerability assessments
Data Management:
– Standardized data formats and APIs
– Automated backup and recovery procedures
– Data lifecycle management policies
– Real-time analytics platforms with proper governance
Industry-Specific Considerations
Automotive Manufacturing
– Supply chain traceability requirements
– Quality control data retention for warranty claims
– Production efficiency metrics for lean manufacturing
– Safety compliance monitoring for worker protection
Food and Beverage
– HACCP compliance with automated monitoring
– Cold chain management with real-time alerts
– Batch tracking for rapid recall capabilities
– Sanitation monitoring with automated reporting
Pharmaceuticals
– FDA validation requirements for all systems
– Environmental monitoring with audit trails
– Batch genealogy tracking for regulatory compliance
– Contamination prevention with real-time detection
Electronics Manufacturing
– ESD monitoring in sensitive production areas
– Component traceability for quality assurance
– Environmental controls for cleanroom operations
– Equipment efficiency tracking for OEE optimization
Making the Business Case for IT Oversight
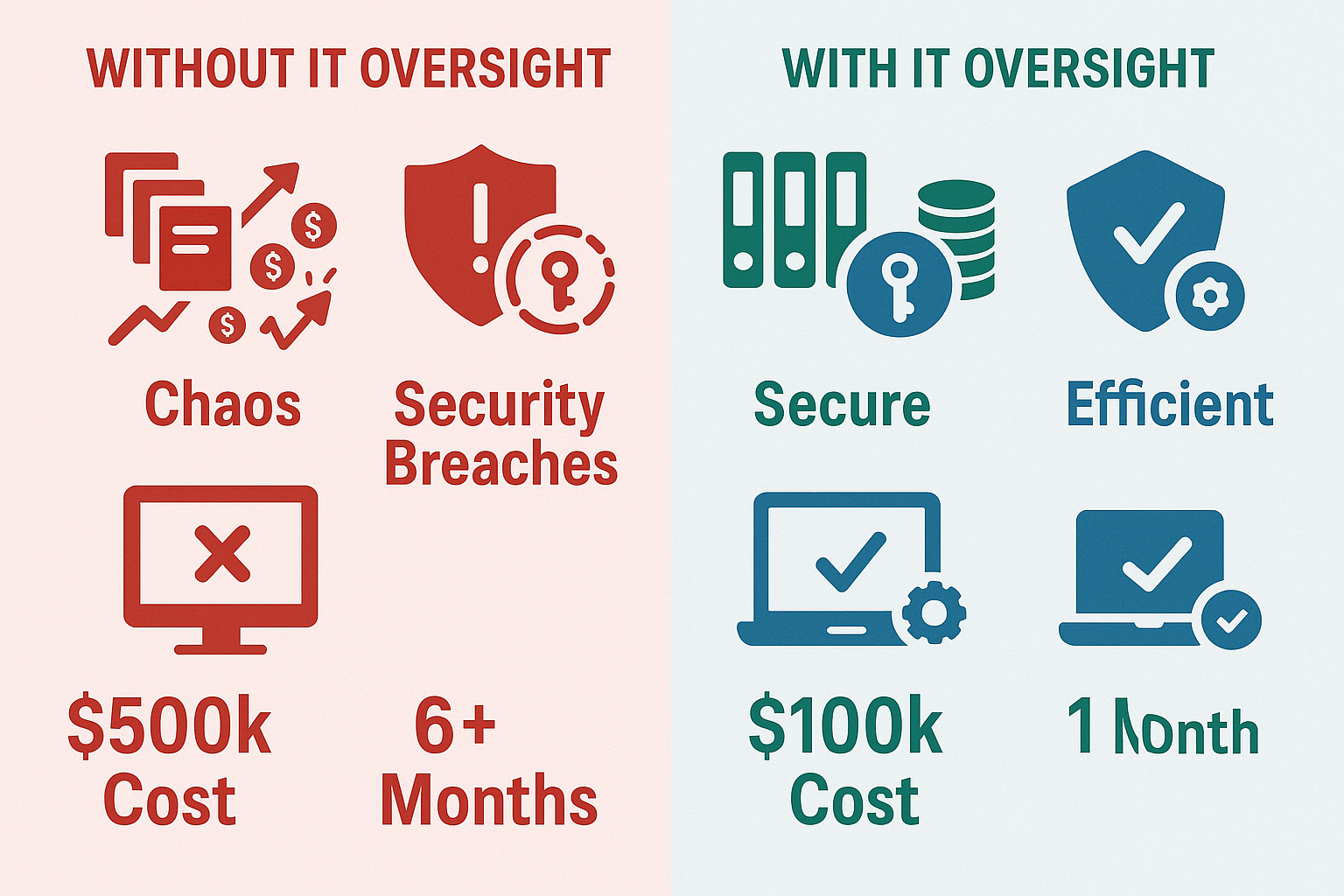
I know what you’re thinking: “This all sounds expensive and complicated.” But here’s the reality – the cost of doing it right upfront is a fraction of the cost of fixing it later.
ROI Calculation Framework
mmediate Benefits:
– Reduced security incidents (Average savings: $500K-$2M annually)
– Improved system reliability (Reduced downtime: 40-60%)
– Faster problem resolution (Mean time to repair: 50% reduction)
– Better compliance posture (Audit preparation time: 70% reduction)
Long-term Value:
– Scalable architecture that grows with your business
– Future-proof technology choices that protect investments
– Competitive advantage through reliable, secure operations
– Innovation enablement with solid foundation for advanced analytics
Building Your Business Case
Step 1: Quantify Current Risks
– Calculate potential costs of security breaches
– Estimate downtime impact on production
– Assess compliance violation penalties
– Factor in opportunity costs of delayed insights
Step 2: Define Success Metrics
– Production efficiency improvements
– Quality control enhancements
– Maintenance cost reductions
– Energy usage optimization
Step 3: Create Implementation Timeline
– Phase 1: Foundation and security (Months 1-3)
– Phase 2: Pilot deployment (Months 4-6)
– Phase 3: Scaling and optimization (Months 7-12)
– Phase 4: Advanced analytics and AI (Year 2+)
Choosing the Right IT Partner
Not all IT teams are created equal when it comes to Industrial IoT. Here’s what to look for:
Essential Capabilities
– OT/IT convergence experience with manufacturing environments
– Industrial protocol expertise (Modbus, OPC-UA, MQTT, etc.)
– Cybersecurity specialization in industrial control systems
– Compliance knowledge for your specific industry
Red Flags to Avoid
– One-size-fits-all solutions that ignore manufacturing requirements
– Lack of industrial experience with only enterprise IT background
– Vendor lock-in strategies that limit future flexibility
– Inadequate security focus treating IoT like standard IT equipment
Questions to Ask Potential Partners
- How many manufacturing IoT deployments have you completed?
- What industry-specific compliance requirements do you understand?
- How do you handle OT/IT network convergence?
- What’s your approach to IoT security and monitoring?
- How do you ensure minimal disruption to production during implementation?
The Future of Manufacturing IoT

As we look ahead to 2025 and beyond, the manufacturers who get IoT right will have significant competitive advantages. But those advantages only come with proper IT foundation.
Emerging Trends to Watch
– AI-powered predictive maintenance requiring massive, clean datasets
– Digital twin technology demanding real-time, reliable data streams
– Supply chain transparency needing secure, traceable data sharing
– Sustainability reporting requiring comprehensive environmental monitoring
Preparing for What’s Next
The IoT foundation you build today will determine whether you can take advantage of these emerging opportunities. Industrial IoT without IT oversight isn’t just a disaster waiting to happen; it’s a barrier to future innovation.
Key Preparation Steps:
– Standardize on open protocols that support future integration
– Build scalable data architecture that can handle exponential growth
– Implement robust security frameworks that can evolve with threats
– Create flexible integration platforms that support rapid innovation
Real Success Stories: When IT Oversight Gets It Right
Let me share a success story that illustrates the power of doing IoT right from the start.
Case Study: Precision Parts Manufacturer
A tier-one automotive supplier wanted to implement predictive maintenance across their CNC machining centers. Instead of rushing into deployment, they partnered with an experienced industrial IT team.
The IT-First Approach:
– Conducted six-month network assessment and planning phase
– Implemented dedicated IoT network with proper segmentation
– Established data governance policies before collecting any data
– Created integration framework connecting to existing ERP and MES systems
Results After 18 Months:
– Zero security incidents despite sophisticated threat landscape
– 35% reduction in unplanned downtime through predictive insights
– $2.3M in maintenance cost savings through optimized scheduling
– Full regulatory compliance with automated audit reporting
– Successful scaling to three additional facilities
The Key Difference:
This wasn’t just about the technology, it was about having the right foundation from day one. When they wanted to add quality monitoring sensors six months later, it took weeks instead of months because the infrastructure was already in place.
Your Action Plan: Getting Started the Right Way
If you’re convinced that Industrial IoT without IT oversight is a disaster waiting to happen, here’s your roadmap to doing it right:
Phase 1: Assessment and Planning (Month 1-2)
Week 1-2: Current State Analysis
– Audit existing network infrastructure
– Identify security vulnerabilities
– Document current systems and data flows
– Assess compliance requirements
Week 3-4: Future State Design
– Define IoT objectives and success metrics
– Design network architecture with proper segmentation
– Create security framework and policies
– Develop integration strategy
Week 5-8: Vendor Selection and Planning
– Evaluate IT partners with industrial experience
– Select IoT platforms and devices
– Create detailed implementation timeline
– Secure budget and stakeholder buy-in
Phase 2: Foundation Building (Month 3-4)
– Implement network segmentation and security controls
– Deploy monitoring and management systems
– Establish data governance policies
– Train IT and operations teams
Phase 3: Pilot Deployment (Month 5-6)
– Deploy IoT devices in controlled environment
– Test all integration points and data flows
– Validate security controls under real conditions
– Document lessons learned and optimize processes
Phase 4: Scaling and Optimization (Month 7-12)
– Roll out to additional production areas
– Implement advanced analytics and reporting
– Continuously monitor and optimize performance
– Plan for future expansion and capabilities
Conclusion
The promise of Industrial IoT is real, improved efficiency, better quality, reduced costs, and competitive advantage. But these benefits only materialize when you build on a solid foundation of proper IT oversight.
Industrial IoT without IT oversight is a disaster waiting to happen because it creates more problems than it solves. Security vulnerabilities, data chaos, integration nightmares, compliance risks, and scalability limitations all stem from the same root cause: treating IoT as a quick technology fix instead of a strategic business transformation.
The manufacturers who succeed with IoT in 2025 and beyond will be those who recognize that technology is only as good as the foundation it’s built on. They’ll invest in proper planning, security, and integration from day one. They’ll partner with IT professionals who understand both technology and manufacturing operations.
Most importantly, they’ll resist the temptation to take shortcuts that lead to disasters.
Your next step is simple: Don’t let your manufacturing operation become another cautionary tale. Start with the foundation, build with proper oversight, and scale with confidence. The competitive advantages of well-implemented Industrial IoT are too significant to risk getting it wrong.
The question isn’t whether you can afford to involve IT in your IoT strategy; it’s whether you can afford not to.
Ready to Take IT Off Your Plate?
Stop worrying about downtime, security risks, or endless IT frustrations. AlphaCIS is the trusted IT partner for small and mid-sized businesses in Metro Atlanta, keeping systems secure, connected, and running the way they should every day.
Whether it’s preventing costly outages, protecting your data, or giving your team unlimited support, we make sure technology helps your business grow instead of holding it back.
📅 Book Your Free Consultation
Dmitriy Teplinskiy
I have worked in the IT industry for 15+ years. During this time I have consulted clients in accounting and finance, manufacturing, automotive and boating, retail and everything in between. My background is in Networking and Cybersecurity



