Picture this: It’s 6 AM on a Tuesday, and the production manager at a major automotive parts manufacturer walks into what should be a bustling factory floor. Instead, they’re greeted by silence. Every machine has stopped. Computer screens display the same chilling message: “Your files have been encrypted. Pay $2 million in Bitcoin to restore operations.” This isn’t science fiction; it’s the new reality of why manufacturing plants are the new cyber targets: protecting OT and IT systems before it’s too late has become the most critical challenge facing industrial operations in 2025.
The convergence of Information Technology (IT) and Operational Technology (OT) has created unprecedented opportunities for cybercriminals to cause maximum damage with minimal effort. What used to require physical access to sabotage can now be accomplished with a single phishing email that travels from the accounting department’s computer to the factory floor’s control systems.
Key Takeaways
• Manufacturing facilities face unique cyber risks due to the convergence of IT and OT systems, creating new attack vectors that can shut down entire production lines
• A single phishing email can cascade from office computers to critical industrial control systems, causing millions in downtime and safety hazards
• Traditional IT security approaches are insufficient for protecting operational technology, requiring specialized strategies and tools
• The financial impact of manufacturing cyberattacks averages $50 million per incident, including downtime, recovery costs, and regulatory fines
• Immediate action is required as 75% of manufacturing companies experienced at least one cyber incident in 2024, with attacks increasing 300% year-over-year
Ready to Take IT Off Your Plate?
Stop worrying about downtime, security risks, or endless IT frustrations. AlphaCIS is the trusted IT partner for small and mid-sized businesses in Metro Atlanta, keeping systems secure, connected, and running the way they should every day.
Whether it’s preventing costly outages, protecting your data, or giving your team unlimited support, we make sure technology helps your business grow instead of holding it back.
📅 Book Your Free ConsultationThe Perfect Storm: How Manufacturing Became Cybercriminals’ Goldmine

The Digital Transformation Trap
I’ve been working in cybersecurity for over a decade, and I’ve never seen a sector transform as rapidly—or as vulnerably—as manufacturing. The push toward Industry 4.0 has created what I call “the perfect storm” for cyber threats.
Here’s what’s happening: Manufacturing companies are connecting everything to everything. Smart factories promise incredible efficiency gains, but they’ve also created a massive attack surface. Every sensor, every robot, every control system that gets connected to the network becomes a potential entry point for attackers.
The numbers tell the story:
- 68% of manufacturing companies have experienced a cyberattack in the past year
- Average downtime from a successful attack: 23 days
- Cost per minute of downtime in automotive manufacturing: $22,000
- Recovery time for OT systems: 3x longer than traditional IT systems
Why Criminals Love Manufacturing Targets
Manufacturing plants are attractive targets for several reasons:
High-Value Operations: When a production line stops, money hemorrhages immediately. Unlike other sectors where downtime is inconvenient, manufacturing downtime is catastrophic.
Safety-Critical Systems: Attackers know that companies will pay quickly when human safety is at risk. I’ve seen organizations pay ransoms not because they couldn’t restore data, but because they couldn’t guarantee worker safety during extended downtime.
Legacy Systems: Many manufacturing facilities run on systems that are 10, 15, or even 20 years old. These systems were never designed with cybersecurity in mind.
Complex Networks: The sheer complexity of modern manufacturing networks makes them difficult to secure comprehensively.
Understanding the IT-OT Convergence Crisis
What Exactly Are IT and OT Systems?
Let me break this down in simple terms, because understanding the difference is crucial to grasping why manufacturing plants are the new cyber targets: protecting OT and IT systems before it’s too late requires a completely different approach than traditional cybersecurity.
Information Technology (IT) includes:
- Office computers and laptops
- Email servers
- Business applications
- Financial systems
- HR databases
- Customer relationship management (CRM) systems
Operational Technology (OT) includes:
- Industrial control systems (ICS)
- Supervisory Control and Data Acquisition (SCADA) systems
- Programmable Logic Controllers (PLCs)
- Human Machine Interfaces (HMIs)
- Safety instrumented systems
- Manufacturing execution systems (MES)
The Dangerous Bridge
Historically, these systems lived in separate worlds. IT managed the business side, OT managed the production side, and never the twain shall meet. But that’s changed dramatically.
I remember visiting a client’s facility in 2023 where the plant manager proudly showed me their new “smart” production line. “We can monitor everything from our phones now!” he said. What he didn’t realize was that the same network connection that let him check production metrics from his iPhone also created a direct pathway for attackers to move from the corporate network to the factory floor.
This convergence creates several critical vulnerabilities:
Shared Network Infrastructure: IT and OT systems now often share the same network, eliminating the “air gap” that previously protected industrial systems.
Remote Access Requirements: The pandemic accelerated remote monitoring needs, creating new entry points for attackers.
Data Integration: Modern manufacturing requires real-time data sharing between business and operational systems.
Cloud Connectivity: Many OT systems now connect to cloud platforms for analytics and monitoring.
🏭 Manufacturing Cybersecurity Risk Assessment
Evaluate your facility's cyber risk level and get personalized recommendations
Ready to Take IT Off Your Plate?
Stop worrying about downtime, security risks, or endless IT frustrations. AlphaCIS is the trusted IT partner for small and mid-sized businesses in Metro Atlanta, keeping systems secure, connected, and running the way they should every day.
Whether it’s preventing costly outages, protecting your data, or giving your team unlimited support, we make sure technology helps your business grow instead of holding it back.
📅 Book Your Free ConsultationHow a Simple Phishing Email Can Shut Down an Entire Plant
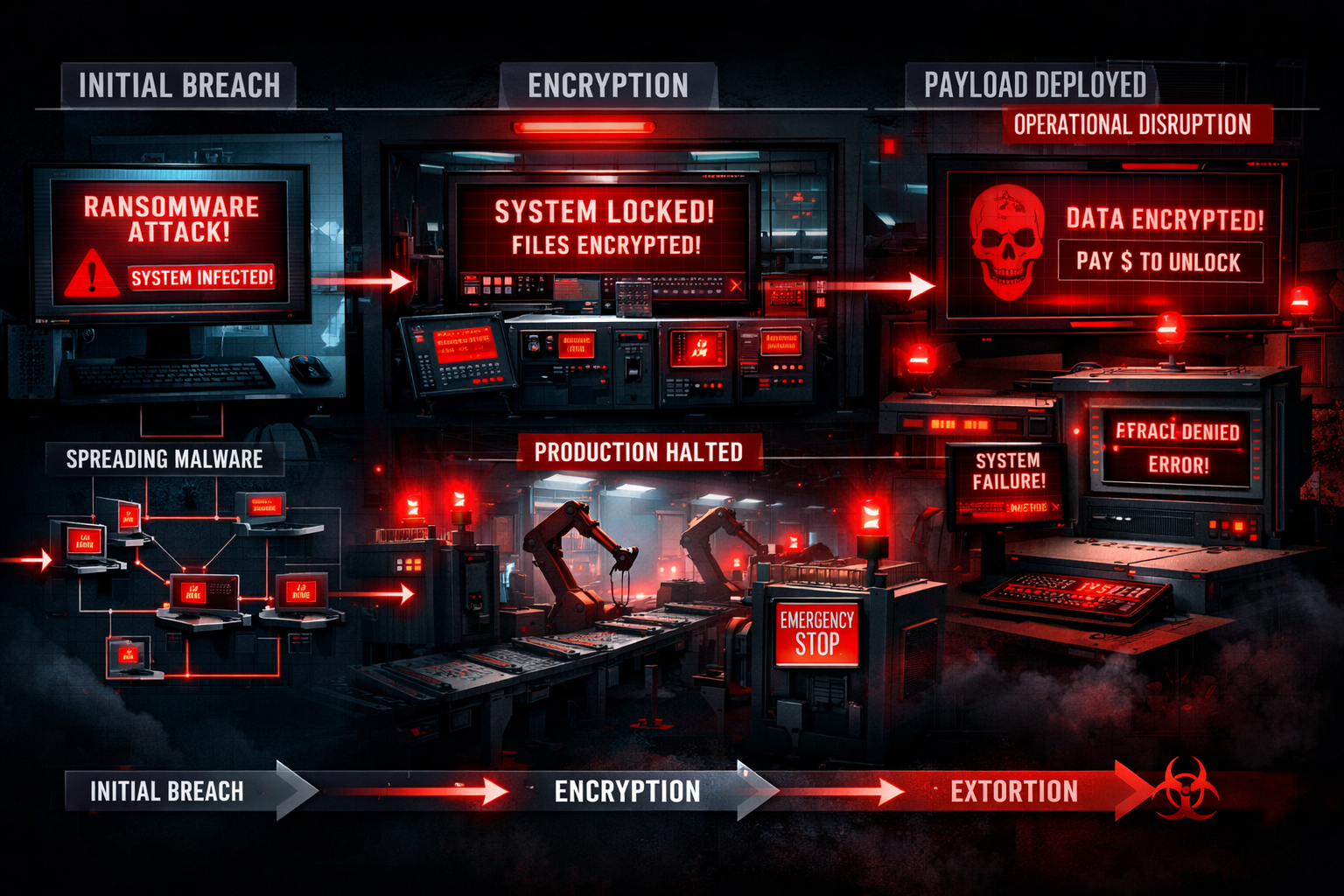
The Anatomy of a Manufacturing Cyberattack
Let me walk you through a real scenario that illustrates exactly why manufacturing plants are the new cyber targets: protecting OT and IT systems before it’s too late isn’t just about technology, it’s about understanding how these attacks actually unfold.
Day 1 – The Entry Point Sarah from accounting receives an email that looks like it’s from her bank, asking her to verify her account. She clicks the link and enters her credentials on what appears to be the bank’s website. Unknown to her, she’s just given attackers access to her computer.
Day 2-7 – Lateral Movement The malware sits quietly, learning about the network. It discovers that Sarah’s computer has access to shared drives, email systems, and—critically—some manufacturing planning software that connects to the production network.
Day 8 – The Bridge The attackers discover that the manufacturing execution system (MES) shares credentials with the business network. They use these credentials to access the OT network.
Day 9-14 – OT Reconnaissance Now inside the operational network, the malware maps out all the connected systems: PLCs controlling assembly lines, SCADA systems managing chemical processes, safety systems, and quality control equipment.
Day 15 – The Attack. At 3 AM on a Monday, the ransomware activates simultaneously across both IT and OT systems. Office computers display ransom demands, but more critically, production systems begin shutting down in a cascade of safety lockouts.
Why OT Systems Are Particularly Vulnerable
Legacy Architecture: Many OT systems run on Windows XP or older operating systems that can’t be easily updated without disrupting production.
Always-On Requirements: Unlike office computers that can be rebooted for updates, many OT systems must run continuously, making security updates challenging.
Shared Credentials: I’ve seen facilities where the same password is used across dozens of industrial controllers. A single compromised credential can unlock everything.
Insufficient Monitoring: Traditional IT security tools often can’t see OT network traffic, creating blind spots where attackers can operate undetected.
The Real Cost of Manufacturing Cyber Incidents
Beyond the Ransom: Hidden Costs That Devastate
When I talk to manufacturing executives about cybersecurity, they often focus on the ransom amount. “We have insurance,” they say. “We can handle a $2 million payment.” But the ransom is just the tip of the iceberg.
Here’s what a typical manufacturing cyberattack actually costs:
Immediate Costs:
- Production Downtime: $50,000-$500,000 per hour, depending on the industry
- Emergency Response: $100,000-$500,000 for incident response teams
- System Recovery: $500,000-$2 million for complete system restoration
- Regulatory Fines: Up to $10 million for safety violations during downtime
Long-term Costs:
- Customer Penalties: $1-10 million in late delivery penalties
- Lost Contracts: 30% of affected companies lose major customers
- Reputation Damage: 15-25% drop in stock price for public companies
- Insurance Premium Increases: 200-400% increase in cyber insurance costs
Case Study: The $50 Million Email
I worked with an automotive parts manufacturer that experienced what I call “the $50 million email.” Here’s how it broke down:
A finance employee clicked on a phishing link that appeared to be from their logistics partner. Within two weeks, attackers had encrypted both the business systems and the factory floor controllers.
The Cascade Effect:
- Hour 1-6: Production stops, safety systems activate
- Day 1-3: Emergency teams attempt recovery
- Week 1-2: Gradual system restoration begins
- Month 1-3: Full production capacity restored
- Months 3-12: Customer relationship recovery
Final Damage:
- Direct costs: $12 million
- Lost production: $18 million
- Customer penalties: $15 million
- Reputation/future business: $5 million
- Total: $50 million
The most painful part? The attack could have been prevented with a $200,000 investment in proper IT-OT security architecture.
Building Fortress-Level Protection for Manufacturing Plants

The Four Pillars of Manufacturing Cybersecurity
Understanding why manufacturing plants are the new cyber targets: protecting OT and IT systems before it’s too late requires a fundamentally different approach than traditional IT security. Here’s the framework I’ve developed after working with dozens of manufacturing facilities:
Pillar 1: Network Segmentation and Zero Trust Architecture
What This Means: Create secure zones within your network so that a breach in one area can’t spread everywhere.
How to Implement:
- Physical Segmentation: Use separate network hardware for IT and OT systems
- Virtual Segmentation: Deploy firewalls and VLANs to create security zones
- Micro-Segmentation: Isolate individual critical systems
- Zero Trust Principles: Verify every connection, even within your network
Real-World Example: I helped a chemical manufacturer implement a three-tier segmentation strategy. When they were hit with a ransomware attack six months later, it was contained to the office network production never stopped.
Pillar 2: OT-Specific Monitoring and Detection
Traditional IT security tools are blind to OT protocols and behaviors. You need specialized monitoring that understands industrial communications.
Essential Capabilities:
- Protocol Analysis: Monitor Modbus, DNP3, EtherNet/IP communications
- Behavioral Analytics: Detect unusual patterns in industrial processes
- Asset Discovery: Maintain a real-time inventory of all OT devices
- Threat Intelligence: Stay updated on manufacturing-specific threats
Key Metrics to Monitor:
- Unauthorized device connections
- Unusual communication patterns
- Failed authentication attempts on industrial systems
- Changes to critical control logic
- Abnormal process parameters
Pillar 3: Human-Centered Security
The Reality: 85% of successful manufacturing cyberattacks start with human error. Your people are both your greatest vulnerability and your strongest defense.
Comprehensive Training Program:
- Role-Specific Training: Different training for office staff vs. plant operators
- Simulated Phishing: Regular testing with immediate feedback
- Incident Response Drills: Practice scenarios specific to manufacturing
- Security Culture: Make cybersecurity part of safety culture
Manufacturing-Specific Scenarios:
- Suspicious USB devices found on the plant floor
- Unusual requests to change production schedules
- Fake vendor communications requesting system access
- Social engineering targeting maintenance staff
Pillar 4: Resilient Recovery and Business Continuity
When (not if) an incident occurs, your response speed determines the total damage.
Recovery Strategy Components:
- Isolated Backups: OT system backups stored offline and tested regularly
- Manual Override Procedures: Documented processes to operate critical systems manually
- Communication Plans: Clear protocols for internal and external communications
- Vendor Coordination: Pre-established relationships with emergency response providers
Advanced Protection Strategies
Industrial Honeypots: Deploy fake industrial devices to detect attackers early in their reconnaissance phase.
AI-Powered Anomaly Detection: Use machine learning to identify subtle changes in industrial processes that might indicate an attack.
Secure Remote Access: Implement jump boxes and privileged access management specifically designed for OT environments.
Supply Chain Security: Vet and monitor all vendors who have access to your industrial networks.
Emergency Response: What to Do When You’re Under Attack
The First 60 Minutes: Critical Actions
When you discover a cyberattack in progress, your actions in the first hour determine whether you’re looking at a minor incident or a catastrophic shutdown. Here’s the emergency playbook I’ve developed:
Minutes 1-5: Immediate Assessment
- Activate your incident response team
- Determine if safety systems are affected
- Document everything: screenshots, timestamps, affected systems
Minutes 5-15: Containment
- Isolate affected systems (but don’t shut down safety systems)
- Preserve evidence for forensic analysis
- Notify key stakeholders (but not via potentially compromised email)
Minutes 15-30: Communication
- Brief executive leadership
- Contact law enforcement (FBI Cyber Division)
- Notify your cyber insurance carrier
- Engage the external incident response team if needed
Minutes 30-60: Stabilization
- Implement manual processes for critical operations
- Assess backup system integrity
- Prepare public communications strategy
Common Mistakes That Make Everything Worse
DON’T Immediately Shut Everything Down: I’ve seen companies cause more damage by panicking and shutting down systems randomly. Safety systems should rarely be turned off during a cyber incident.
DON’T Try to “Fix” Infected Systems: Attempting to clean malware without proper forensics can destroy evidence and spread the infection.
DON’T Negotiate Ransoms Without Expert Help: Paying ransoms doesn’t guarantee recovery and may fund future attacks against you or others.
DON’T Assume Backups Are Clean: Many modern attacks specifically target backup systems. Verify backup integrity before attempting restoration.
The Future of Manufacturing Cybersecurity

Emerging Threats on the Horizon
As we look toward 2026 and beyond, the threat landscape for manufacturing is evolving rapidly. Understanding why manufacturing plants are the new cyber targets: protecting OT and IT systems before it’s too late means staying ahead of these emerging threats:
AI-Powered Attacks: Cybercriminals are beginning to use artificial intelligence to automate the discovery and exploitation of OT vulnerabilities. These attacks can adapt in real-time, making traditional signature-based defenses obsolete.
Supply Chain Infiltration: Attackers are increasingly targeting the software and hardware supply chain, embedding malicious code in industrial control systems before they’re even installed.
Nation-State Targeting: Government-sponsored hackers are viewing critical manufacturing infrastructure as strategic targets, bringing military-grade capabilities to industrial cybercrime.
IoT Device Exploitation: The explosion of connected sensors and devices in smart factories creates millions of new potential entry points.
Building Future-Ready Defenses
Quantum-Resistant Encryption: As quantum computing advances, current encryption methods will become vulnerable. Start planning for post-quantum cryptography now.
AI-Driven Defense: Deploy machine learning systems that can detect and respond to attacks faster than human analysts.
Blockchain for Supply Chain Security: Use distributed ledger technology to verify the integrity of software and hardware components.
Integrated Safety-Security Systems: Develop systems where cybersecurity and functional safety work together seamlessly.
Taking Action: Your Next Steps to Secure Manufacturing Operations
Immediate Actions (This Week)
- Conduct a Quick Risk Assessment: Use the interactive tool above to understand your current risk level
- Inventory Your Connected Systems: Document every connection between IT and OT networks
- Review Access Controls: Audit who has access to critical industrial systems
- Test Your Backups: Verify that you can actually restore from your OT system backups
Short-Term Actions (Next 30 Days)
- Implement Basic Segmentation: At a minimum, put a firewall between IT and OT networks
- Deploy OT Monitoring: Install tools that can see and analyze industrial network traffic
- Train Your Team: Conduct manufacturing-specific cybersecurity training
- Develop Incident Response Procedures: Create playbooks for different attack scenarios
Long-Term Strategy (Next 90 Days)
- Comprehensive Security Assessment: Engage experts to evaluate your entire IT-OT ecosystem
- Implement Zero Trust Architecture: Design and deploy a comprehensive zero trust framework
- Establish Security Operations: Create or outsource 24/7 monitoring capabilities
- Regular Testing and Improvement: Schedule quarterly security assessments and annual penetration testing
Conclusion: The Time to Act is Now
The question isn’t whether your manufacturing facility will be targeted, it’s when. As I’ve shown throughout this article, understanding why manufacturing plants are the new cyber targets: protecting OT and IT systems before it’s too late isn’t just about implementing technology solutions. It’s about recognizing that the convergence of IT and OT has fundamentally changed the risk landscape for industrial operations.
The statistics are sobering: 75% of manufacturing companies experienced cyber incidents in 2024, with attacks increasing 300% year-over-year. The average cost of a successful attack now exceeds $50 million when you factor in downtime, recovery, regulatory fines, and lost business. But here’s what gives me hope: every company I’ve worked with that took proactive steps to secure their IT-OT convergence has successfully defended against attacks that devastated their unprepared competitors.
The convergence of IT and OT systems has created unprecedented opportunities for cybercriminals, but it has also created opportunities for manufacturing companies to build more resilient, more secure operations than ever before. The key is acting now, before you become the next cautionary tale.
Your production lines, your workers’ safety, and your company’s future depend on the cybersecurity decisions you make today. Don’t wait for an attack to expose your vulnerabilities; start building your defenses now.
Remember: In manufacturing cybersecurity, there are two types of companies: those that have been attacked and know it, and those that have been attacked and don’t know it yet. Which one will you be?
Ready to Take IT Off Your Plate?
Stop worrying about downtime, security risks, or endless IT frustrations. AlphaCIS is the trusted IT partner for small and mid-sized businesses in Metro Atlanta, keeping systems secure, connected, and running the way they should every day.
Whether it’s preventing costly outages, protecting your data, or giving your team unlimited support, we make sure technology helps your business grow instead of holding it back.
📅 Book Your Free Consultation
Dmitriy Teplinskiy
I have worked in the IT industry for 15+ years. During this time I have consulted clients in accounting and finance, manufacturing, automotive and boating, retail and everything in between. My background is in Networking and Cybersecurity



