Picture this: Sarah, your most trusted accountant, arrives at the office Monday morning with her usual coffee and determination to tackle the week ahead. She’s been with your Atlanta-based company for eight years, never missed a deadline, and has a spotless record. At 9:47 AM, she receives what appears to be an urgent email from “IT Support” requesting that she verify her login credentials due to a security update. Without hesitation, she clicks the link and enters her information. Within minutes, your entire network is compromised.
Sound familiar? You’re not alone. Despite investing thousands in cybersecurity training, 83% of organizations experienced successful phishing attacks in 2025. The question isn’t whether your employees are smart enough; it’s understanding why even the brightest minds fall for digital deception.
Key Takeaways

Ready to Take IT Off Your Plate?
Stop worrying about downtime, security risks, or endless IT frustrations. AlphaCIS is the trusted IT partner for small and mid-sized businesses in Metro Atlanta, keeping systems secure, connected, and running the way they should every day.
Whether it’s preventing costly outages, protecting your data, or giving your team unlimited support, we make sure technology helps your business grow instead of holding it back.
📅 Book Your Free Consultation- Human psychology, not lack of intelligence, drives employees to click on malicious links through cognitive biases and emotional triggers
- Traditional cybersecurity training fails because it doesn’t address the psychological factors that influence decision-making under pressure
- Effective training programs combine behavioral psychology with practical simulations to create lasting behavioral change
- Building a cyber-aware culture requires ongoing reinforcement rather than one-time training sessions
- Atlanta businesses can significantly reduce breach risk by implementing psychology-based training approaches that work with human nature, not against it
The Human Element: Why Smart People Make Risky Clicks
The Perfect Storm of Psychology and Technology
When I first started working with Atlanta businesses on cybersecurity, I was puzzled. How could seasoned executives, detail-oriented accountants, and tech-savvy employees consistently fall for what seemed like obvious scams? The answer lies in understanding that cybercriminals aren’t just exploiting technology, they’re exploiting human psychology.
Modern phishing attacks succeed because they trigger our most basic psychological responses:
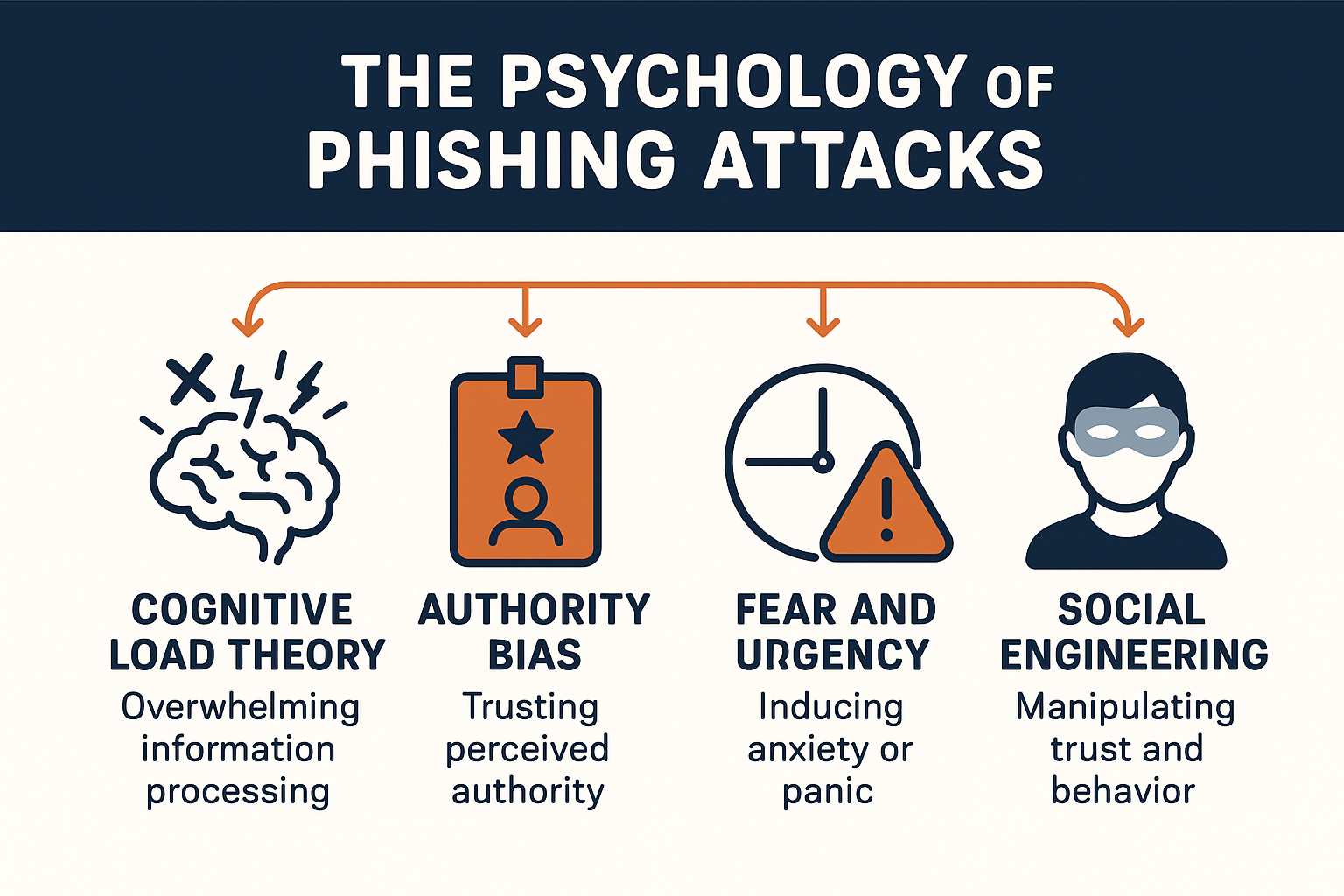
Cognitive Load Theory
When employees are overwhelmed with daily tasks, their mental capacity for careful decision-making decreases. A busy Monday morning or end-of-quarter crunch creates the perfect environment for hasty clicks.
Authority Bias
We’re hardwired to respond quickly to authority figures. Emails appearing to come from “IT,” “HR,” or “The CEO” bypass our normal skepticism.
Fear and Urgency
Messages threatening account suspension, security breaches, or missed deadlines trigger our fight-or-flight response, shutting down critical thinking.
Social Engineering Precision
Today’s attackers research their targets extensively, crafting messages that feel personally relevant and timely.
The Atlanta Business Landscape: Unique Vulnerabilities
Working with Metro Atlanta companies, I’ve noticed specific patterns that make local businesses particularly vulnerable:
– Rapid growth environments where new employees haven’t fully absorbed the security culture
– Mixed remote and in-office work creates communication confusion
– Industry diversity means one-size-fits-all training doesn’t work
– Relationship-based business culture that values quick responses and helpfulness
Why Traditional Cybersecurity Training Falls Short
The Lecture Hall Problem
Most cybersecurity training follows an outdated educational model: present information, test knowledge, assume behavior change. This approach ignores decades of behavioral psychology research showing that knowledge alone doesn’t drive action.
Here’s what typically happens:
- Employees attend a training session
- They learn about phishing techniques
- They pass a quiz
- They return to work and… click the next convincing link
The Disconnect Between Knowledge and Action
I recently worked with a manufacturing company in Marietta where 95% of employees passed their cybersecurity quiz, yet 40% failed a simulated phishing test the following week. The issue wasn’t a lack of knowledge; it was the gap between knowing what to do and actually doing it under pressure.
Traditional training fails because it doesn’t account for:
The Knowing-Doing Gap
Understanding risks intellectually doesn’t translate to split-second decision-making in real scenarios.
Context Switching
Training scenarios rarely match the actual conditions where employees encounter threats.
Timing Issues
Annual or quarterly training creates knowledge decay, as employees forget crucial details when they need them most.
Lack of Reinforcement
One-time sessions don’t create lasting behavioral change.
The Psychology Behind Why Good Employees Click Bad Links
Cognitive Biases That Work Against Us
Understanding specific psychological biases helps explain why even security-conscious employees make risky decisions:
1. Availability Heuristic
Employees judge risk based on how easily they can recall similar incidents. If they haven’t experienced a breach recently, they underestimate the threat.
2. Optimism Bias
“It won’t happen to me” thinking leads to overconfidence in personal ability to spot threats.
3. Confirmation Bias
When an email aligns with expectations (like an expected delivery notification), employees look for reasons to trust it rather than question it.
4. Automation Bias
Heavy reliance on spam filters and security software creates false confidence that “the system will catch real threats.”
Emotional Triggers That Override Logic
Cybercriminals deliberately exploit emotional states that impair judgment:
Fear-Based Attacks
“Your account will be suspended in 24 hours” messages trigger panic responses that bypass careful analysis.
Excitement and Greed
“You’ve won!” or “Exclusive offer” emails tap into positive emotions that reduce skepticism.
Helpfulness and Compliance
Requests for assistance or compliance with company policies exploit employees’ desire to be helpful and follow rules.
Time Pressure
“Urgent action required” creates artificial deadlines that prevent thorough evaluation.
The Social Engineering Evolution
Modern attacks have evolved far beyond obvious “Nigerian prince” scams. Today’s cybercriminals use sophisticated social engineering techniques:
Open Source Intelligence (OSINT)
Attackers research targets using LinkedIn, company websites, and social media to craft highly personalized messages.
Business Email Compromise (BEC)
Impersonating executives or vendors in ongoing email conversations makes detection extremely difficult.
Multi-Channel Attacks
Combining emails, texts, and phone calls creates believable scenarios that feel legitimate.
Building Effective Psychology-Based Cybersecurity Training
The Science of Behavioral Change
Effective cybersecurity training must be grounded in behavioral psychology principles that actually drive lasting change:
Targeted Behavior Modification
Instead of generic awareness, focus on specific behaviors you want to see: pausing before clicking, verifying sender identity, and reporting suspicious messages.
Spaced Repetition
Psychological research shows that information learned through spaced repetition (reviewing material at increasing intervals) creates stronger, longer-lasting memories.
Experiential Learning
Hands-on experience through simulations creates emotional memories that are easier to recall under pressure.
Positive Reinforcement
Rewarding good security behaviors is more effective than punishing mistakes.
Creating Realistic Training Scenarios
The most effective training mirrors real-world conditions as closely as possible:
Simulated Phishing Campaigns
Regular, realistic phishing simulations help employees practice recognition skills in actual work contexts.
Role-Playing Exercises
Having employees practice handling suspicious calls or requests builds confidence and muscle memory.
Multi-Device Training
Training on phones, tablets, and computers reflects how employees actually encounter threats.
Time-Pressure Scenarios
Practicing decision-making under artificial time pressure prepares employees for real urgent situations.
Personalization and Relevance
Generic training fails because it doesn’t connect with individual employee experiences:
Industry-Specific Scenarios
Healthcare, finance, and manufacturing face different threat types requiring tailored training.
Role-Based Training
Executives, IT staff, and general employees need different skills and awareness levels.
Individual Risk Profiles
Some employees are naturally more cautious, while others are quick to trust. Training should account for these differences.
Implementing Psychology-Based Training in Your Organization

Phase 1: Assessment and Baseline
Before implementing new training, understand your current security culture:
Vulnerability Assessment
Conduct baseline phishing simulations to identify high-risk employees and departments.
Security Culture Survey
Measure employee attitudes, knowledge gaps, and behavioral patterns around cybersecurity.
Risk Analysis
Identify which departments, roles, or individuals face the highest threat exposure.
Phase 2: Customized Training Design
Develop training programs that address specific psychological and practical needs:
Behavioral Objectives
Define specific, measurable behaviors you want to see rather than vague “awareness” goals.
Cognitive Load Management
Break complex security concepts into digestible chunks that don’t overwhelm employees.
Mental Model Building
Help employees develop accurate mental models of how attacks work and why security measures exist.
Phase 3: Implementation and Reinforcement
Ongoing Simulation Schedule
Implement regular, varied phishing simulations that evolve with threat landscape changes.
Microlearning Modules
Deliver bite-sized security lessons through brief, frequent touchpoints rather than lengthy sessions.
Communication Integration
Weave security messaging into regular business communications to maintain awareness.
Recognition Programs
Celebrate employees who demonstrate good security behaviors to reinforce positive actions.
🔍 Phishing Email Analyzer
Test your ability to spot suspicious emails using real-world examples
⚠️ Security Concerns Detected:
💡 Security Tips:
- Always verify sender identity through a separate communication channel
- Hover over links to preview the actual URL before clicking
- Be suspicious of urgent language and time pressure tactics
- Check for spelling errors and grammatical mistakes
- When in doubt, contact your IT department
Ready to Take IT Off Your Plate?
Stop worrying about downtime, security risks, or endless IT frustrations. AlphaCIS is the trusted IT partner for small and mid-sized businesses in Metro Atlanta, keeping systems secure, connected, and running the way they should every day.
Whether it’s preventing costly outages, protecting your data, or giving your team unlimited support, we make sure technology helps your business grow instead of holding it back.
📅 Book Your Free ConsultationMeasuring Success: Beyond Click Rates
Comprehensive Metrics for Training Effectiveness
Traditional cybersecurity training often measures success solely by phishing simulation click rates. However, effective psychology-based training requires more nuanced measurement:
Behavioral Metrics
– Time taken to report suspicious emails
– Frequency of security-related questions to IT
– Adoption of security tools and features
– Compliance with security policies
Psychological Indicators
– Confidence levels in identifying threats
– Security mindset changes over time
– Stress levels when encountering suspicious content
– Cultural attitudes toward security reporting
Business Impact Measures
– Reduction in successful attacks
– Decreased incident response costs
– Improved regulatory compliance scores
– Enhanced customer trust metrics
Creating a Feedback Loop
Successful training programs continuously evolve based on real-world results:
Regular Assessment Cycles
Quarterly evaluations help identify emerging threats and training gaps.
Trend Analysis
Tracking performance over time reveals whether training effects are sustained or diminishing.
Targeted Interventions
Data-driven approaches allow for personalized training based on individual risk profiles.
Common Mistakes in Cybersecurity Training Implementation
The “One and Done” Approach
Many Atlanta businesses make the mistake of treating cybersecurity training as a compliance checkbox rather than an ongoing cultural initiative. Annual training sessions followed by months of silence create knowledge decay and complacency.
Focusing on Fear Instead of Empowerment
While it’s important to communicate risks, training that relies primarily on fear tactics often backfires:
– Employees become anxious about normal business activities
– Fear of punishment reduces reporting of potential incidents
– Stress impairs decision-making abilities
– Negative associations with security reduce engagement
Ignoring Individual Differences
Cookie-cutter training programs fail because they don’t account for:
Learning Style Variations
Some employees learn better through visual content, others through hands-on practice.
Role-Specific Risks
Executives face different threats than customer service representatives.
Personality Factors
Risk-averse individuals need different training than naturally trusting employees.
Technology Comfort Levels
Digital natives and technology newcomers require different approaches.
Advanced Strategies for Cyber-Aware Culture Building
Psychological Safety in Security Reporting
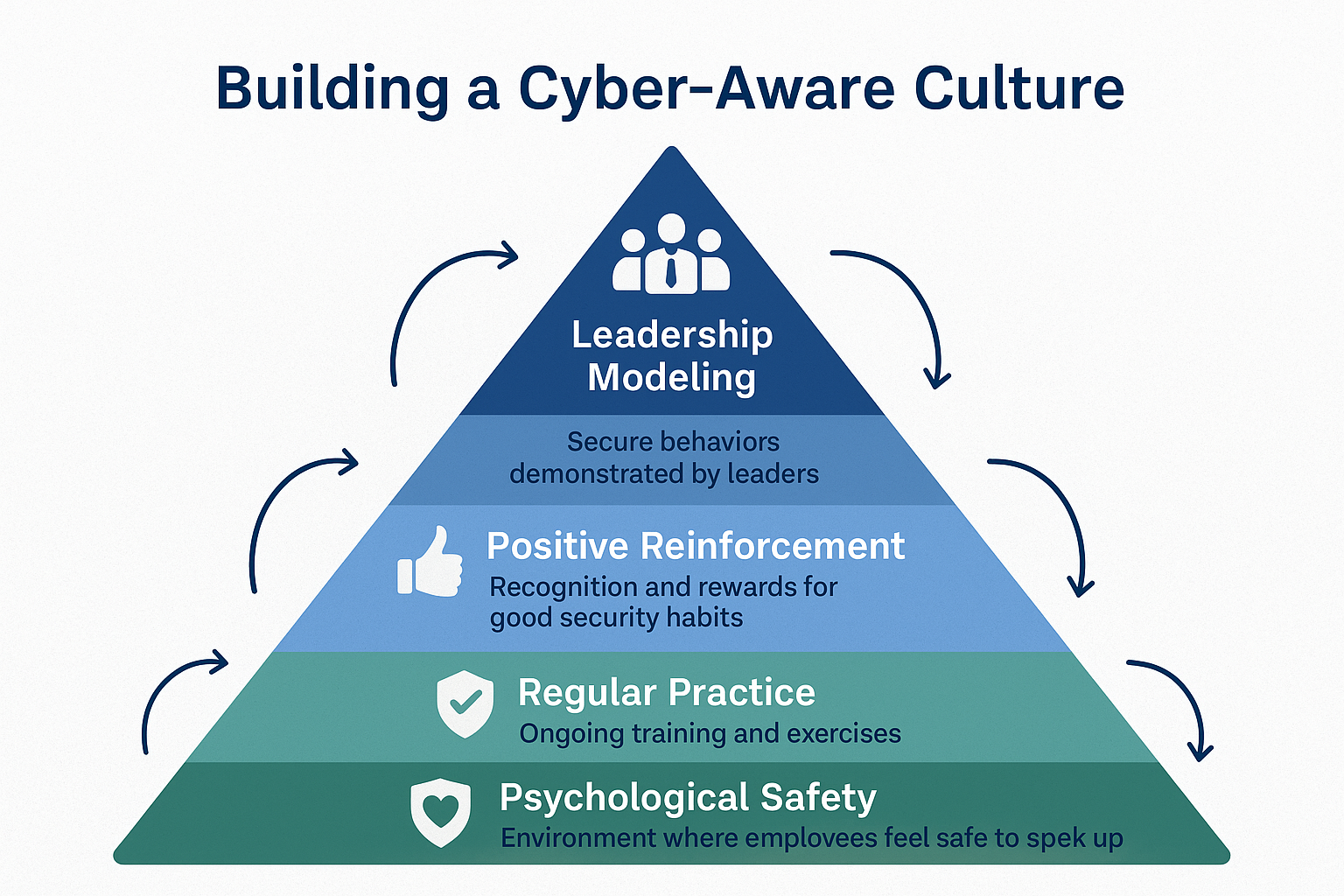
Creating an environment where employees feel safe reporting security concerns is crucial for long-term success:
No-Blame Policies
Employees who fall for phishing attempts should receive additional training, not punishment.
Positive Reinforcement
Celebrate employees who report suspicious activities, even false alarms.
Transparent Communication
Share (anonymized) security incident learnings across the organization.
Leadership Modeling
Executives should openly discuss their own security challenges and learnings.
Gamification and Engagement Strategies
Security Champions Programs
Identify and train security-minded employees to become peer educators and resources.
Recognition Systems
Implement point systems, badges, or other recognition for security-positive behaviors.
Mobile-Friendly Microlearning
Deliver bite-sized security content through apps or messaging platforms.
Scenario-Based Challenges
Create realistic security scenarios that employees can practice in low-stakes environments.
Integration with Business Processes
Security in Onboarding
Make cybersecurity awareness part of new employee orientation from day one.
Regular Touchpoints
Integrate security reminders into existing business communications and meetings.
Performance Integration
Include security awareness as a component of employee performance evaluations.
Department-Specific Training
Tailor security training to specific departmental risks and workflows.
The Future of Psychology-Based Cybersecurity Training
Emerging Technologies and Approaches
AI-Powered Personalization
Machine learning algorithms can tailor training content to individual learning patterns and risk behaviors.
Virtual Reality Training
Immersive VR environments provide realistic training scenarios without the risks of the real world.
Real-Time Decision Support
Mobile apps and browser extensions can provide just-in-time security guidance when employees encounter suspicious content.
Neurofeedback Integration
Advanced biometric monitoring could help identify when employees are in mental states that increase vulnerability to attacks.
Evolving Threat Landscape Considerations
AI-Generated Attacks
As artificial intelligence makes phishing attempts more sophisticated, training must evolve to address deepfake audio, video, and highly personalized content.
Multi-Platform Threats
Training must address security across email, messaging apps, social media, and emerging communication platforms.
Remote Work Challenges
Distributed workforces require training approaches that work across different environments and technology setups.
Implementing Psychology-Based Training: A Step-by-Step Guide for Atlanta Businesses
Month 1: Foundation and Assessment
Week 1-2: Current State Analysis
– Conduct baseline phishing simulations
– Survey employee security attitudes and knowledge
– Analyze existing security policies and procedures
– Identify high-risk departments and roles
Week 3-4: Training Design
– Develop psychology-based training curriculum
– Create role-specific content and scenarios
– Design measurement and feedback systems
– Establish communication plans
Month 2: Pilot Implementation
Week 1-2: Pilot Group Training
– Select diverse pilot group (10-15% of workforce)
– Deliver initial training sessions
– Conduct immediate feedback collection
– Begin regular simulation schedule
Week 3-4: Pilot Evaluation
– Analyze pilot group performance
– Gather detailed feedback from participants
– Refine training content and delivery methods
– Prepare for full rollout
Months 3-6: Full Implementation and Optimization
Month 3: Organization-Wide Rollout
– Deploy training to all employees
– Establish regular communication cadence
– Begin comprehensive simulation program
– Launch security champion network
Month 4-6: Monitoring and Refinement
– Track behavioral and performance metrics
– Adjust training content based on emerging threats
– Provide additional support to high-risk individuals
– Celebrate successes and share learnings
Ongoing: Culture Maintenance
Quarterly Activities:
– Update training content for new threats
– Conduct comprehensive performance reviews
– Refresh simulation scenarios
– Recognize security champions and positive behaviors
Annual Activities:
– Complete program effectiveness assessment
– Update policies and procedures
– Plan next year’s training evolution
– Benchmark against industry standards
Cost-Benefit Analysis: The ROI of Psychology-Based Training

Investment Considerations
Direct Training Costs
– Training platform and content development
– Employee time investment
– Ongoing simulation and assessment tools
– External consulting and expertise
Time Investment
– Initial training sessions (4-8 hours per employee)
– Ongoing microlearning (15-30 minutes monthly)
– Simulation participation (5-10 minutes weekly)
– Security champion activities (2-4 hours monthly)
Return on Investment
Breach Prevention Value
The average cost of a data breach for small to medium businesses ranges from $120,000 to $1.24 million. Effective training that prevents even one breach typically pays for itself many times over.
Productivity Benefits
– Reduced time spent on incident response
– Fewer false positive security alerts
– Improved employee confidence in technology use
– Enhanced customer trust and retention
Compliance Advantages
– Reduced regulatory fines and penalties
– Improved audit results
– Enhanced insurance coverage options
– Stronger legal position in case of incidents
Conclusion
The reality is clear: your employees aren’t clicking bad links because they’re careless or unintelligent; they’re responding to sophisticated psychological manipulation designed to exploit fundamental human nature. Traditional cybersecurity training fails because it treats this as an education problem when it’s actually a behavioral psychology challenge.
For Atlanta businesses in 2025, the solution lies in understanding and working with human psychology rather than against it. Effective cybersecurity training must:
Address cognitive biases and emotional triggers that make employees vulnerable
Provide realistic, hands-on practice in safe environments
Create positive security cultures that encourage reporting and learning
Offer ongoing reinforcement rather than one-time events
Personalize approaches based on individual and role-specific needs
The businesses that thrive in our increasingly digital landscape will be those that recognize cybersecurity as fundamentally a human challenge requiring human-centered solutions. Your employees can become your strongest defense, but only if you train them in ways that align with how the human mind actually works.
The question isn’t whether you can afford to implement psychology-based cybersecurity training. The question is whether you can afford not to. With cyber threats evolving daily and the average cost of breaches continuing to climb, the time for action is now.
Start by assessing your current security culture, understanding your unique vulnerabilities, and designing training that treats your employees as intelligent humans who need the right tools and knowledge to make good decisions under pressure. Your future self and your business will thank you.
Ready to Take IT Off Your Plate?
Stop worrying about downtime, security risks, or endless IT frustrations. AlphaCIS is the trusted IT partner for small and mid-sized businesses in Metro Atlanta, keeping systems secure, connected, and running the way they should every day.
Whether it’s preventing costly outages, protecting your data, or giving your team unlimited support, we make sure technology helps your business grow instead of holding it back.
📅 Book Your Free Consultation
Dmitriy Teplinskiy
I have worked in the IT industry for 15+ years. During this time I have consulted clients in accounting and finance, manufacturing, automotive and boating, retail and everything in between. My background is in Networking and Cybersecurity



