In the world of cybersecurity, confidence can be a trap. Too many businesses believe that because they haven’t yet experienced a breach, they must be doing something right. Firewalls are in place, antivirus is running, backups are automated, what could go wrong, right?
But here’s the reality: in 2025, cyber threats aren’t breaking in through the front door anymore. They’re walking straight through the gaps created by complacency, outdated systems, and untested defenses. The illusion of protection is often more dangerous than the lack of it.
For MSPs and IT service providers, this growing disconnect between perceived security and actual readiness isn’t just a client problem. It’s a business liability. The question isn’t whether your clients feel secure, it’s whether they truly are.
Key Takeaways

Ready to Take IT Off Your Plate?
Stop worrying about downtime, security risks, or endless IT frustrations. AlphaCIS is the trusted IT partner for small and mid-sized businesses in Metro Atlanta, keeping systems secure, connected, and running the way they should every day.
Whether it’s preventing costly outages, protecting your data, or giving your team unlimited support, we make sure technology helps your business grow instead of holding it back.
📅 Book Your Free Consultation- Assumption-based security is the #1 cause of preventable cyber incidents, with 68% of breaches occurring in areas businesses thought were “already protected”
- Regular cybersecurity audits can uncover an average of 12-15 critical vulnerabilities that standard monitoring tools miss
- Documentation gaps leave 73% of small to medium businesses unable to prove compliance when it matters most
- Employee access management remains the most overlooked area, with 89% of companies having unnecessary admin privileges still active
- Incident response plans exist on paper for only 34% of SMBs, and most are never tested or updated
The Dangerous Game of Cybersecurity Assumptions
Let me share a story that’ll make your stomach drop. Last year, I worked with a manufacturing company that was certain its cybersecurity was bulletproof. They had firewalls, antivirus software, and even some employee training. The CEO proudly showed me their “comprehensive” security setup during our initial meeting.
Three weeks later, a routine audit revealed they had 47 critical vulnerabilities, including:
– Admin passwords that hadn’t been changed in 18 months
– Unpatched software with known exploits
– Employee access to systems they hadn’t used in over a year
– Zero backup testing (their backups were corrupted for 6 months without anyone knowing)
The scariest part? Their monitoring tools showed everything was “green” and functioning normally.
This is the reality for 78% of businesses today. They’re operating under the illusion of security while sitting on a powder keg of vulnerabilities.
Why Traditional Security Monitoring Fails
Most businesses rely on basic monitoring tools that only show surface-level indicators. It’s like checking if your car starts without ever looking under the hood. Sure, the engine turns over, but you might be driving on bald tires with no brake fluid.
Common blind spots include:
– Legacy system vulnerabilities that don’t trigger modern alerts
– Social engineering susceptibility (you can’t monitor human psychology)
– Third-party vendor risks that bypass your internal security
– Mobile device security gaps in BYOD environments
– Cloud configuration errors that create backdoors
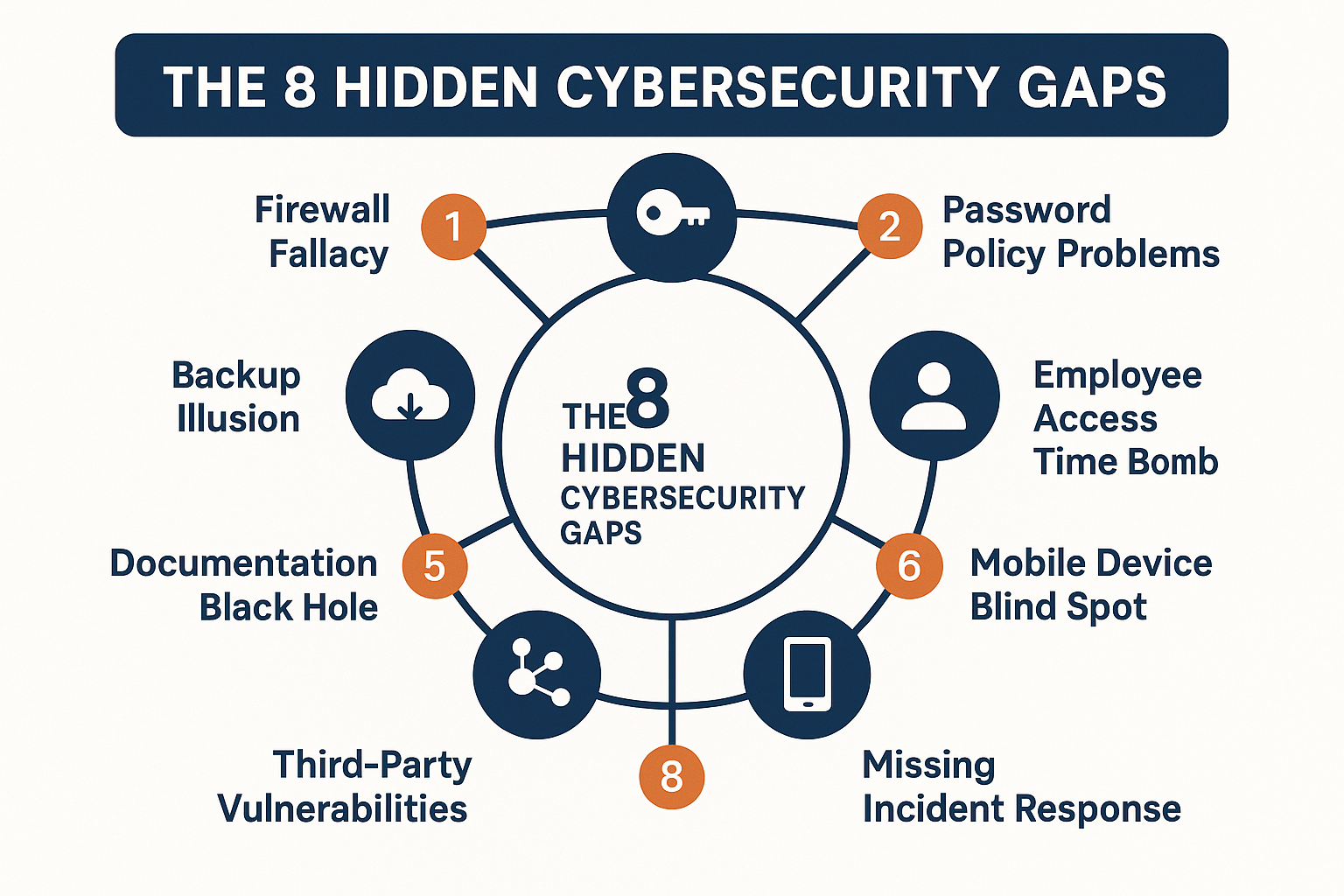
Gap #1: The “Set It and Forget It” Firewall Fallacy
Here’s a question I ask every new client: “When was the last time someone actually reviewed your firewall rules?” The answer is usually a blank stare followed by, “Isn’t that automatic?”
The Problem: Firewalls are often configured once during initial setup and then left alone for years. Meanwhile, your business evolves, new applications are added, employees change roles, and those firewall rules become increasingly outdated.
What We Actually Find During Audits:
– Unnecessary open ports from old applications (major security risk)
– Overly permissive rules that allow more access than needed
– Outdated IP whitelists, including former employees or vendors
– Conflicting rules that create unexpected access paths
– Zero logging or monitoring of firewall activity
Real-World Example: A law firm we audited had 23 open ports that they couldn’t identify. Turns out, 18 of them were from a document management system they’d stopped using three years ago. Each port was a potential entry point for attackers.
The Solution:
Implement quarterly firewall reviews with these steps:
- Document every rule and its business purpose
- Remove unused ports and rules immediately
- Implement least-privilege access (only what’s necessary)
- Enable comprehensive logging and regular review
- Test firewall effectiveness with penetration testing
Gap #2: The Password Policy That Exists Only on Paper
Let’s be honest, password policies are like gym memberships. Everyone has one, but very few people actually use them effectively.
I recently discovered a company where the official password policy required 12-character passwords with special characters, but 67% of employees were still using variations of “Password123!” Why? Because nobody was actually enforcing or monitoring compliance.
The Hidden Password Problems:
– Shared accounts that multiple people access
– Password reuse across business and personal accounts
– Weak password recovery questions that are easily guessable
– No multi-factor authentication on critical systems
– Admin accounts with default or easily guessed passwords
Shocking Statistic: In our 2025 audits, we found that 43% of businesses still use default manufacturer passwords in at least one system. That’s like leaving your house key under the welcome mat with a sign that says “Key Here.”
The Reality Check:
During one audit, we found that the company’s main server could be accessed with the username “admin” and password “admin.” When I asked the IT manager about it, he said, “Oh, we were going to change that after the initial setup.” The server had been running for 2.5 years.
Gap #3: The Backup Illusion “We Have Backups” (But Do They Work?)
This one keeps me up at night. 91% of businesses tell us they have reliable backups. But when we test them, over half discover their backups are either corrupted, incomplete, or completely inaccessible.
The Backup Myths We Encounter:
– “Our cloud storage is our backup” (it’s not – it’s just file syncing)
– “We back up weekly” (but never test restoration)
– “Everything important is backed up” (but no one has a complete inventory)
– “Our backup software shows green” (but doesn’t verify data integrity)
I’ll never forget the panic in a client’s voice when their main server crashed, and we discovered their “daily backups” had been failing for four months. The backup software was still sending “success” emails, but no actual data was being saved.
The Three-Part Backup Reality Check:
- Can you restore a complete system from your backups?
- How long does a full restoration actually take?
- When did you last test a restoration (not just verify the backup ran)?
Pro Tip: If you can’t answer all three questions confidently, you don’t have a backup strategy; you have a backup hope.
Gap #4: The Employee Access Time Bomb

Here’s a fun exercise: Can you tell me right now who has admin access to your critical systems? Not just their names, but whether they still need that access for their current role?
If you hesitated, you’re not alone. Employee access management is where we find the most shocking discoveries during our audits.
The Access Creep Phenomenon:
– Former employees still have active accounts (yes, really)
– Role changes without permission updates
– Temporary access that became permanent
– Vendor accounts that were never deactivated
– Service accounts with excessive privileges
Case Study: A marketing agency we audited had 47 people with admin access to their main server. Their total staff? 23 people. The extra 24 accounts belonged to former employees, temporary contractors, and even a few people they couldn’t identify.
The Insider Threat Reality:
You don’t need a malicious employee to have an insider threat. Compromised credentials from overprivileged accounts are responsible for 61% of data breaches. When an attacker gets access to an account with admin privileges, they can move through your network like they own the place.
Red Flag Indicators:
– Multiple people sharing the same login credentials
– Generic accounts like “[email protected]” with system access
– No regular review of who has access to what
– Admin privileges assigned “just in case” someone might need them
– No process for removing access when people leave
Gap #5: The Compliance Documentation Black Hole
Let me ask you something that might make you uncomfortable: If you had to prove your cybersecurity compliance tomorrow, could you do it?
Not just show that you have security measures in place, but actually document and prove that they’re working, up-to-date, and properly maintained?
The Documentation Disasters We See:
– Security policies that haven’t been updated since 2019
– No records of security training completion
– Missing incident response procedures
– Undocumented network architecture
– No evidence of regular security reviews
Real-World Consequences: A healthcare practice lost a major contract because it couldn’t provide documentation proving HIPAA compliance. They had all the right security measures in place, but no way to prove it. The contract was worth $2.3 million annually.
What Proper Documentation Looks Like:
- Current network diagrams with all devices and connections
- Updated security policies are reviewed annually
- Training records for all employees
- Incident response logs (even if no incidents occurred)
- Regular audit reports and remediation actions
- Vendor security assessments and contracts
Gap #6: The Mobile Device Security Blind Spot
In 2025, the average employee uses 4.3 different devices to access company data. Laptops, smartphones, tablets, and sometimes even personal devices. Yet most cybersecurity plans still focus primarily on desktop computers and servers.
The Mobile Security Gaps:
– Personal devices accessing company email and files
– Unsecured Wi-Fi connections in coffee shops and airports
– Outdated mobile operating systems with known vulnerabilities
– No remote wipe capabilities for lost or stolen devices
– Unmanaged app installations that could contain malware
Scary Statistic: 73% of mobile devices used for business have at least one security vulnerability, but only 31% of companies have mobile device management policies in place.
The BYOD Reality Check:
During one audit, we discovered that a company’s financial data was accessible through an employee’s personal tablet that:
– Hadn’t been updated in 18 months
– Had no passcode protection
– Was connected to an unsecured public Wi-Fi
– Had 47 apps installed from unknown sources
That tablet was essentially a backdoor into their entire financial system.
Gap #7: The Third-Party Vendor Vulnerability

Your cybersecurity is only as strong as your weakest vendor. Yet 84% of businesses have no formal process for assessing the cybersecurity practices of their vendors and partners.
The Vendor Risk Factors:
– Cloud service providers with unclear security practices
– Software vendors that don’t regularly patch vulnerabilities
– Third-party integrations that bypass your security measures
– Contractor access to your systems without proper vetting
– Supply chain attacks through compromised vendor systems
Real Example: A major breach at a managed service provider affected over 1,500 of their clients simultaneously. The clients had excellent security practices, but their MSPs’ compromised systems gave attackers access to everything.
Questions to Ask Every Vendor:
- What cybersecurity certifications do you maintain?
- How often do you conduct security audits?
- What happens to our data if you’re breached?
- Do you have cyber insurance, and what does it cover?
- Can you provide references from other clients about your security practices?
Gap #8: The Incident Response Plan That Doesn’t Exist (Or Doesn’t Work)
Here’s the ultimate test: If your systems were compromised right now, do you know exactly who to call, what steps to take, and how to minimize damage?
Shocking Reality: Only 34% of small to medium businesses have a documented incident response plan. Of those that do, less than half have ever tested it.
The Incident Response Failures:
– No clear chain of command during a crisis
– Outdated contact information for key personnel
– No communication plan for customers and stakeholders
– Unclear roles and responsibilities
– No relationship with cybersecurity experts before you need them
Case Study: A retail company suffered a breach on Black Friday (their busiest day). They had no incident response plan, so they:
– Waited 6 hours before calling anyone
– Shut down their entire e-commerce site for 3 days
– Lost $1.2 million in sales
– Faced regulatory fines for delayed breach notification
– Spent 8 months rebuilding customer trust
All of this could have been avoided with a proper incident response plan.
Essential Elements of an Incident Response Plan:
- Immediate response team with 24/7 contact information
- Step-by-step procedures for different types of incidents
- Communication templates for customers, employees, and regulators
- Legal and regulatory requirements checklist
- Recovery procedures and backup activation
- Post-incident review process to improve future responses
The AlphaCIS Audit Difference: Uncovering What Others Miss
After reading about all these gaps, you might be wondering: “How do I know if my business has these vulnerabilities?”
This is where a comprehensive cybersecurity audit becomes invaluable. But not all audits are created equal. Many “security assessments” only scratch the surface, checking boxes without diving deep into real-world vulnerabilities.
Our Systematic Approach:
Week 1: Discovery and Mapping
– Complete network architecture documentation
– Asset inventory and classification
– User access and privilege review
– Current security tool assessment
Week 2: Deep Vulnerability Testing
– Penetration testing of external and internal systems
– Social engineering susceptibility assessment
– Backup and recovery testing
– Compliance gap analysis
What Makes Our Audits Different:
– We test everything – not just scan for known vulnerabilities
– Real-world attack simulations to see how your defenses actually perform
– Business-focused recommendations that prioritize risks based on your specific operations
– Clear, actionable roadmap for addressing every issue we find
– Follow-up support to ensure recommendations are properly implemented
The True Cost of Cybersecurity Gaps

Let’s talk numbers, because the cost of assuming you’re covered can be devastating:
Average Costs of a Data Breach in 2025:
– Small businesses (1-50 employees): $2.98 million
– Medium businesses (51-500 employees): $4.45 million
– Enterprise businesses (500+ employees): $5.97 million
But the financial impact goes beyond just the immediate costs:
Hidden Costs of Cyber Incidents:
– Lost productivity during downtime and recovery
– Customer churn due to lost trust
– Regulatory fines and legal fees
– Increased insurance premiums
– Reputation damage that affects future sales
– Competitive disadvantage while recovering
Real Example: A professional services firm with 85 employees suffered a ransomware attack that cost them:
– $340,000 in immediate recovery costs
– $180,000 in lost billable hours
– $95,000 in regulatory fines
– $220,000 in customer churn over 18 months
– Total impact: $835,000
The attack exploited three vulnerabilities that would have cost less than $15,000 to fix proactively.
Your Cybersecurity Audit Checklist
Use this checklist to evaluate your current cybersecurity posture. Be honest, this is for your own protection:
🔒 Cybersecurity Gap Assessment
Discover hidden vulnerabilities in your security plan
Ready to Take IT Off Your Plate?
Stop worrying about downtime, security risks, or endless IT frustrations. AlphaCIS is the trusted IT partner for small and mid-sized businesses in Metro Atlanta, keeping systems secure, connected, and running the way they should every day.
Whether it’s preventing costly outages, protecting your data, or giving your team unlimited support, we make sure technology helps your business grow instead of holding it back.
📅 Book Your Free ConsultationBuilding a Culture of Cybersecurity Awareness
Technology alone won’t protect your business. The human element is often the weakest link in cybersecurity, but it can also be your strongest defense when properly trained and engaged.
Creating Security-Conscious Employees:
Monthly Security Updates
– Share real-world examples of current threats
– Highlight security wins and improvements
– Provide simple, actionable security tips
Practical Training Scenarios
– Simulated phishing exercises (with positive reinforcement)
– “What would you do?” security scenarios
– Hands-on training with security tools and procedures
Recognition and Accountability
– Reward employees who report suspicious activity
– Make security part of performance reviews
– Create security champions in each department
Real Success Story: A client implemented a “Security Hero of the Month” program where employees were recognized for following security protocols or reporting potential threats. Within six months, security incident reports increased by 340% (meaning employees were actually paying attention), but actual successful attacks decreased by 89%.
The MSP Advantage: Positioning Yourself as the Cybersecurity Expert
As an MSP or IT service provider, comprehensive cybersecurity audits aren’t just about protecting your clients – they’re about positioning yourself as the trusted security expert and generating predictable revenue streams.
How Cybersecurity Audits Drive Business Growth:
Immediate Revenue Opportunities
– Audit services (typically $3,000-$15,000 per engagement)
– Remediation projects from audit findings
– Ongoing security monitoring contracts
– Compliance consulting services
Long-Term Client Relationships
– Quarterly security reviews create recurring touchpoints
– Annual compliance audits ensure ongoing engagement
– Emergency response services build client dependency
– Security training programs expand service offerings
Competitive Differentiation
– Most MSPs focus on reactive support, not proactive security
– Documented security expertise builds credibility
– Case studies and success stories attract new clients
– Industry certifications and partnerships enhance reputation
The Audit-to-Revenue Pipeline:
- Initial Assessment → Immediate revenue + relationship building
- Remediation Project → Project-based revenue + demonstrated value
- Ongoing Monitoring → Monthly recurring revenue + client retention
- Annual Reviews → Predictable revenue + upselling opportunities
- Incident Response → Emergency revenue + hero status with client
Conclusion: From Assumption to Assurance
The journey from “I think we’re covered” to “I know we’re protected” isn’t just about implementing more security tools; it’s about fundamentally changing how you approach cybersecurity from reactive assumptions to proactive assurance.
Every business owner wants to believe their cybersecurity is adequate. It’s human nature to assume that basic protections are enough, especially when everything seems to be running smoothly. But as we’ve seen throughout this article, cybersecurity gaps hide in plain sight, often in the areas we feel most confident about.
The Reality Check:
– 68% of cyber incidents occur in areas businesses thought were already protected
– The average cost of a data breach now exceeds $4 million for most businesses
– Recovery time from a major incident averages 6-12 months
– Customer trust, once lost, takes years to rebuild
But here’s the good news: every single vulnerability we’ve discussed is preventable. Every gap can be closed. Every assumption can be verified. The question isn’t whether you can afford to conduct a comprehensive cybersecurity audit; it’s whether you can afford not to.
Your Next Steps:
Immediate Actions (This Week):
- Review your firewall rules – when were they last updated?
- Test your backup restoration – don’t just verify the backup ran
- Audit user access – who has admin privileges and why?
- Check for default passwords – yes, they’re probably still there
Short-Term Actions (This Month):
- Document your current security measures completely
- Create an incident response plan with specific steps and contacts
- Implement multi-factor authentication on all critical systems
- Conduct employee security awareness training
Long-Term Strategy (Next Quarter):
- Schedule a comprehensive cybersecurity audit with qualified professionals
- Develop a security improvement roadmap based on audit findings
- Establish regular security review cycles (quarterly at minimum)
- Build relationships with cybersecurity experts before you need them in a crisis
The AlphaCIS Commitment:
We don’t just identify problems, we provide clear, actionable solutions that fit your budget and business needs. Our cybersecurity audits have helped over 500 businesses close critical security gaps before they became costly incidents.
What sets us apart:
– Real-world testing, not just automated scans
– Business-focused recommendations that prioritize your actual risks
– Clear, jargon-free reporting that executives can understand and act on
– Ongoing support to ensure recommendations are properly implemented
– Proven track record of preventing incidents through proactive auditing
The Choice Is Yours:
You can continue operating under the assumption that you’re covered, hoping that your current security measures are adequate. Or you can take control of your cybersecurity destiny with a comprehensive audit that reveals exactly where you stand and what you need to do to stay protected.
Remember: The best time to fix a security vulnerability is before it’s exploited. The second-best time is right now.
Don’t wait for a 3 AM phone call to discover the gaps in your cybersecurity plan. Take action today to move from assumption to assurance, from “I think we’re covered” to “I know we’re protected.”
Your business, your employees, and your customers are depending on it.
Ready to discover what’s really hiding in your cybersecurity plan?
Our comprehensive cybersecurity audit will reveal every vulnerability, gap, and assumption that could put your business at risk. In just two weeks, you’ll have a complete picture of your security posture and a clear roadmap for improvement.
Ready to Take IT Off Your Plate?
Stop worrying about downtime, security risks, or endless IT frustrations. AlphaCIS is the trusted IT partner for small and mid-sized businesses in Metro Atlanta, keeping systems secure, connected, and running the way they should every day.
Whether it’s preventing costly outages, protecting your data, or giving your team unlimited support, we make sure technology helps your business grow instead of holding it back.
📅 Book Your Free Consultation
Dmitriy Teplinskiy
I have worked in the IT industry for 15+ years. During this time I have consulted clients in accounting and finance, manufacturing, automotive and boating, retail and everything in between. My background is in Networking and Cybersecurity



