The Real Reason Your Employees Click on Phishing Emails (and How to Stop It)
Picture this: Your most trusted employee, Sarah from accounting, just clicked on what looked like an urgent email from the CEO. Within minutes, your company’s financial data is compromised, and you’re staring at a potential $4.45 million loss, the average cost of a data breach in 2024.
If you think this scenario is far-fetched, think again. 95% of successful cyberattacks start with a phishing email, and it’s not just happening to “other companies.” It’s happening to businesses just like yours, every single day.
But here’s what might surprise you: The real reason your employees click on phishing emails has nothing to do with stupidity or carelessness. It’s rooted in basic human psychology, workplace pressure, and gaps in your cybersecurity training that you probably don’t even know exist.
The Uncomfortable Truth About Phishing Success Rates
Let me share something that might make you uncomfortable: Your smartest employees are often the most likely targets.
I recently worked with a tech startup where their head of IT, someone who literally taught cybersecurity courses, fell for a sophisticated phishing attack. The email appeared to come from their cloud service provider, warning about an imminent account suspension. Under pressure to keep systems running, he clicked the link and entered his credentials on what looked like a legitimate login page.
This wasn’t a case of ignorance. This was a case of perfectly crafted psychological manipulation meeting human vulnerability at exactly the right moment.
The Numbers Don’t Lie
According to recent cybersecurity research:
– 1 in 4 employees will click on a phishing link during simulated tests
– Spear phishing attacks have a 70% open rate compared to 3% for legitimate marketing emails
– 91% of cyberattacks begin with a phishing email
– Business email compromise (BEC) attacks cost organizations over $2.9 billion annually
But here’s the kicker: these statistics represent smart, well-intentioned people who simply encountered the right psychological trigger at the wrong time.
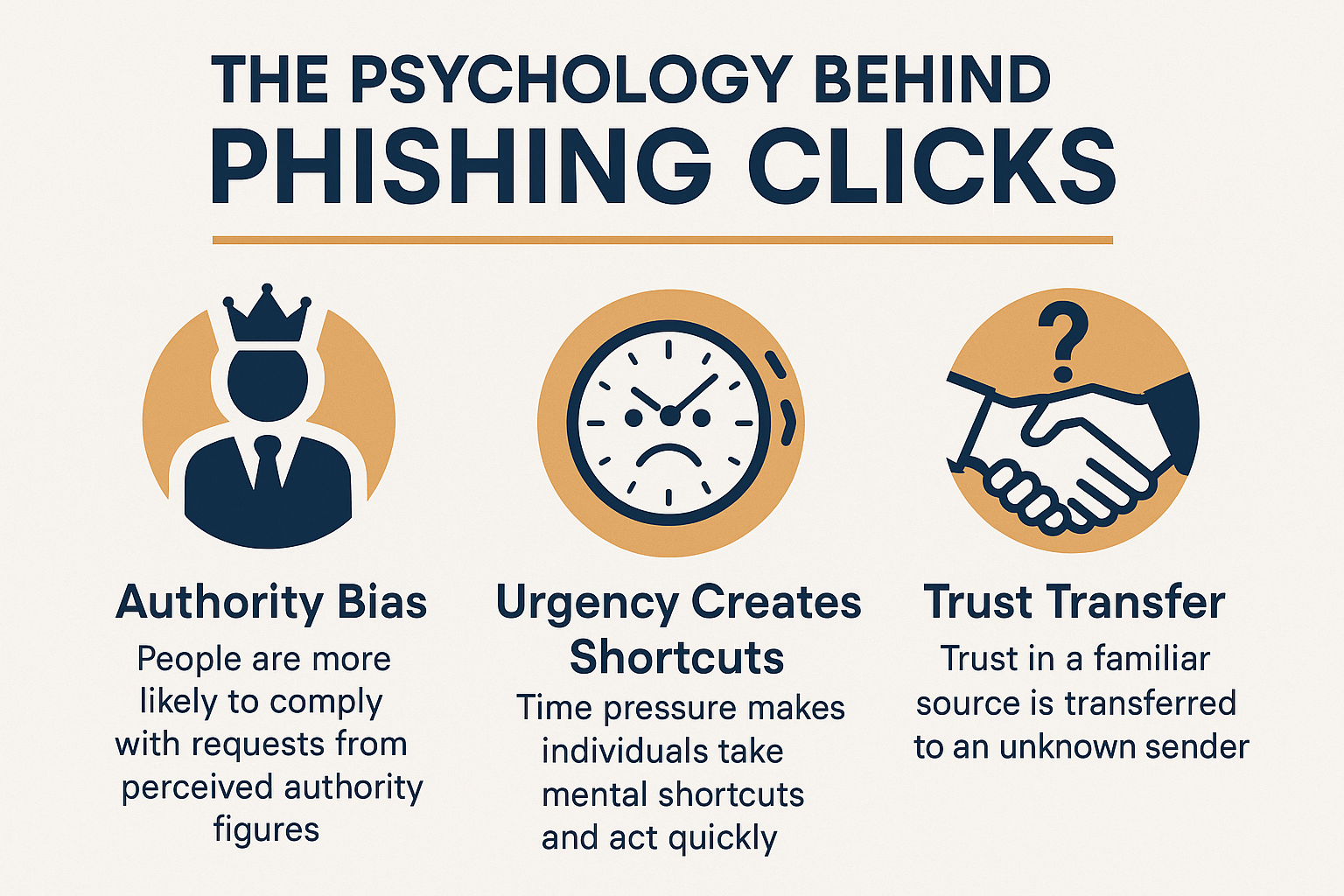
The Real Psychology Behind Phishing Clicks
1. The Authority Bias Trap
Why it works: Humans are hardwired to respond to authority figures without question. When an email appears to come from your CEO, IT department, or a trusted vendor, your brain’s natural response is compliance, not skepticism.
Real-world example: I’ve seen attackers impersonate executives requesting urgent wire transfers, and employees comply because questioning authority feels uncomfortable, even dangerous to their job security.
The psychological trigger: Fear of disappointing authority figures overrides security protocols.
2. Urgency Creates Cognitive Shortcuts
Why it works: When we’re under time pressure, our brains switch to “fast thinking” mode, bypassing careful analysis. Phishing emails exploit this by creating artificial urgency.
Common urgency tactics:
– “Your account will be suspended in 24 hours.”
– “Immediate action required”
– “Time-sensitive security alert”
– “Respond by the end of business today.”
The psychological trigger: Stress hormones impair our ability to think critically and spot inconsistencies.
3. The Trust Transfer Phenomenon
Why it works: Attackers don’t just impersonate random people; they carefully research your organization to identify trusted relationships and exploit them.
I once investigated an attack where cybercriminals spent three weeks studying a company’s social media, website, and public communications to craft the perfect impersonation of their largest client requesting a “confidential” invoice payment to a new account.
The psychological trigger: Existing trust relationships create mental shortcuts that bypass normal verification processes.
Why Traditional Security Training Fails
Let’s be honest: Your current cybersecurity training probably isn’t working.
Here’s why:
The “Awareness Theater” Problem
Most organizations check the cybersecurity training box with annual presentations that cover:
– Technical explanations of phishing
– Generic examples that don’t reflect real threats
– Scare tactics that create anxiety without actionable solutions
– One-size-fits-all approaches that ignore role-specific risks
The result? Employees sit through the training, pass the quiz, and promptly forget everything because it doesn’t connect to their daily reality.
The Context Gap
Traditional training happens in a sterile environment, a conference room, or an online module completely divorced from the high-pressure, multitasking reality of modern work.
But phishing attacks happen when employees are:
– Rushing to meet deadlines
– Juggling multiple urgent requests
– Working outside normal hours
– Dealing with technical problems
– Feeling overwhelmed or distracted
This context gap is why someone can “know” about phishing intellectually but still fall victim when caught in the wrong moment.
The Shame Spiral Effect
Here’s something most security experts won’t tell you: Fear-based training often makes the problem worse.
When employees are taught that clicking phishing links is a serious mistake that could cost the company millions, they become paralyzed by fear. Instead of reporting suspicious emails or admitting mistakes, they:
– Delete questionable emails without reporting them
– Hide security incidents to avoid blame
– Become so anxious about email that productivity suffers
– Stop asking IT questions for fear of appearing incompetent
This creates a culture of secrecy that makes your organization more vulnerable, not less.
The Five Hidden Vulnerabilities in Your Organization
1. The “Trusted Sender” Blind Spot
The problem: Employees receive hundreds of emails from familiar senders, vendors, clients, and internal teams. When attackers compromise these accounts or create convincing spoofs, the emails sail right through mental security filters.
Real example: A law firm lost $1.2 million when attackers compromised their client’s email account and sent wire transfer instructions that looked completely legitimate.
The fix: Implement verification protocols for any financial or sensitive requests, regardless of the sender.
2. Mobile Email Vulnerability
The problem: Mobile devices make it harder to spot phishing indicators. Small screens hide email headers, URLs are truncated, and hovering to preview links isn’t possible.
The statistics: 70% of employees check email on mobile devices, but most phishing training focuses on desktop indicators.
The fix: Mobile-specific training and enhanced email filtering for mobile access.
3. The “Good Employee” Paradox
The problem: Your most helpful, responsive employees, the ones who always reply quickly and go above and beyond, are often the most vulnerable to social engineering.
Why it happens: Attackers specifically target people who are likely to respond positively to requests for help or urgent demands.
The fix: Create “permission to pause” policies that encourage verification without penalizing helpfulness.
4. Third-Party Integration Confusion
The problem: Modern businesses use dozens of cloud services, creating legitimate reasons for employees to receive authentication requests, password resets, and access notifications.
The confusion: It becomes nearly impossible to distinguish legitimate service emails from sophisticated phishing attempts.
The fix: Centralized identity management and clear protocols for handling third-party communications.
5. The Remote Work Security Gap
The problem: Remote employees often work in isolation, without the natural verification that comes from turning to a colleague and asking, “Did you get this weird email too?”
Additional challenges:
– Home network security varies widely
– Personal and business email mixing
– Reduced IT support accessibility
– Increased reliance on digital communication
The fix: Enhanced remote-specific security protocols and virtual verification systems.
The Psychology-Based Defense Strategy
Now that we understand why phishing works, let’s talk about solutions that address human psychology rather than fighting against it.
1. Implement “Cognitive Speed Bumps”
Instead of expecting employees to spot sophisticated phishing attempts, create systematic pauses that interrupt the rush to respond.
Practical implementation:
– The 60-second rule: Any urgent financial or access request requires a 60-second pause before action
– Verification prompts: Email systems that automatically flag external emails with verification reminders
– Two-person protocols: Require verbal confirmation for sensitive requests above certain thresholds
2. Make Reporting Rewarding, Not Risky
Transform your culture from “don’t click bad emails” to “help us identify threats.”
Culture shift strategies:
– Positive reinforcement: Reward employees who report suspicious emails, even false alarms
– No-blame policies: Explicitly state that reporting potential phishing attempts will never result in negative consequences
– Transparency: Share (anonymized) examples of reported threats and how they helped protect the organization
– Gamification: Create friendly competition around security awareness and threat identification
3. Context-Specific Training
Replace generic training with role-based scenarios that reflect actual work situations.
For accounting teams:
– Invoice fraud scenarios using your actual vendor names
– Fake urgent payment requests from “executives”
– Compromised client email simulations
For HR departments:
– Fake job applications with malicious attachments
– Phishing emails requesting employee information
– Social engineering attempts targeting personnel data
For executives:
– CEO fraud targeting other executives
– Sophisticated business email compromise scenarios
– Social media intelligence gathering examples
4. Real-Time Learning Systems
Instead of annual training events, implement continuous micro-learning that happens in the moment.
Effective approaches:
– Just-in-time tips: Brief security reminders triggered by specific email patterns
– Immediate feedback: When employees report suspicious emails, provide instant confirmation and explanation
– Contextual warnings: Smart email systems that highlight potential risk indicators without blocking legitimate communication
– Peer learning: Encourage teams to discuss and share suspicious emails they’ve encountered
Building Your Multi-Layered Defense System
The most effective approach combines technology, psychology, and clear processes. Here’s how to build a system that works:
Layer 1: Technical Controls
Email filtering and authentication:
– SPF, DKIM, and DMARC implementation
– Advanced threat protection with sandboxing
– URL rewriting and safe link services
– Attachment scanning and quarantine
User interface improvements:
– External email banners that identify outside senders
– Link preview tools that show actual destinations
– Mobile-friendly security indicators
– One-click reporting buttons
Layer 2: Human-Centered Policies
Clear escalation procedures:
– Specific contact methods for verifying suspicious requests
– Decision trees for common scenarios
– Alternative communication channels for urgent situations
– Regular updates to reflect new threat patterns
Psychological safety measures:
– Written policies protecting employees who report threats
– Regular communication about the value of security vigilance
– Leadership modeling of security-conscious behavior
– Recognition programs for security contributions
Layer 3: Continuous Improvement
Regular assessment:
– Monthly simulated phishing campaigns with immediate feedback
– Quarterly security culture surveys
– Annual third-party security assessments
– Ongoing threat landscape monitoring
Adaptive training:
– Training content that evolves with current threat patterns
– Personalized learning paths based on individual risk factors
– Cross-departmental security discussions
– Integration with new employee onboarding
Implementing Simulated Phishing That Works
Traditional “gotcha” phishing simulations often backfire by creating fear and resentment. Here’s how to do it right:
The Educational Approach
Before the simulation:
– Announce that simulations will be conducted (but not when)
– Explain the educational purpose and positive intent
– Provide resources for learning and improvement
– Establish clear policies about consequences (spoiler: there shouldn’t be punitive ones)
During the simulation:
– Use realistic but not traumatizing scenarios
– Vary difficulty levels to match different roles and experience levels
– Include both obvious and sophisticated attempts
– Track metrics that matter: reporting rates, not just click rates
After the simulation:
– Provide immediate, constructive feedback
– Offer additional training for those who need it
– Share aggregate results with the entire organization
– Use results to improve policies and training, not to punish individuals
Measuring What Matters
Traditional metrics (less useful):
– Click rates on simulated phishing emails
– Training completion percentages
– Quiz scores
Better metrics:
– Reporting rates: How many suspicious emails do employees forward to IT?
– Response time: How quickly are potential threats identified and escalated?
– Cultural indicators: Do employees feel comfortable asking security questions?
– Behavioral change: Are security practices improving over time?
Creating a Security-Conscious Culture
The goal isn’t to create a workplace where employees are afraid of email; it’s to build a culture where security awareness is a natural part of how work gets done.
Leadership’s Role
Model the behavior you want to see:
– Executives should visibly follow security protocols
– Leaders should ask clarifying questions about suspicious communications
– Management should celebrate and reward security-conscious behavior
– Decision-makers should invest in security tools that make compliance easier, not harder
Communication Strategies
Make security relevant and personal:
– Share stories about how security protects the company’s mission
– Connect cybersecurity to job security and company stability
– Highlight how security practices protect customer trust
– Demonstrate the personal benefits of security awareness
Regular, varied communication:
– Monthly security newsletters with real-world examples
– Quarterly all-hands presentations on current threats
– Annual security appreciation events
– Ongoing informal discussions about security topics
The ROI of Getting This Right
Investing in psychology-based phishing defense isn’t just about avoiding losses; it’s about enabling business success.
Cost Avoidance
Direct savings:
– Average data breach cost: $4.45 million
– Business email compromise average loss: $120,000 per incident
– Ransomware recovery costs: $1.85 million average
– Regulatory fines and legal costs: Variable but substantial
Indirect benefits:
– Preserved customer trust and reputation
– Maintained business continuity
– Protected intellectual property
– Avoided regulatory scrutiny
Business Enablement
Competitive advantages:
– Customer confidence: Clients trust organizations that take security seriously
– Partner relationships: Vendors prefer working with security-conscious companies
– Talent attraction: Security-minded professionals want to work for responsible employers
– Innovation capacity: Secure organizations can adopt new technologies faster
Productivity Gains
Reduced friction:
– Employees spend less time worrying about email security
– Clear protocols reduce decision paralysis
– Automated security tools handle routine threats
– Fewer security incidents mean fewer business disruptions
Common Implementation Mistakes to Avoid
Mistake 1: The “One and Done” Approach
The problem: Treating cybersecurity awareness as a checkbox item rather than an ongoing process.
The solution: Build security awareness into regular business operations, not just annual training events.
Mistake 2: Technology-Only Solutions
The problem: Believing that better email filters and security software alone will solve the phishing problem.
The solution: Combine technical controls with human-centered policies and ongoing education.
Mistake 3: Fear-Based Messaging
The problem: Using scare tactics that create anxiety and paralysis rather than confident, security-conscious behavior.
The solution: Focus on empowerment, education, and positive reinforcement rather than punishment and blame.
Mistake 4: Ignoring Mobile Security
The problem: Designing security policies and training around desktop email while employees increasingly work on mobile devices.
The solution: Ensure all security measures and training account for mobile usage patterns and limitations.
Mistake 5: Underestimating Social Engineering
The problem: Focusing only on technical phishing indicators while ignoring the psychological manipulation tactics that make phishing effective.
The solution: Train employees to recognize and respond to social engineering techniques, not just suspicious links and attachments.
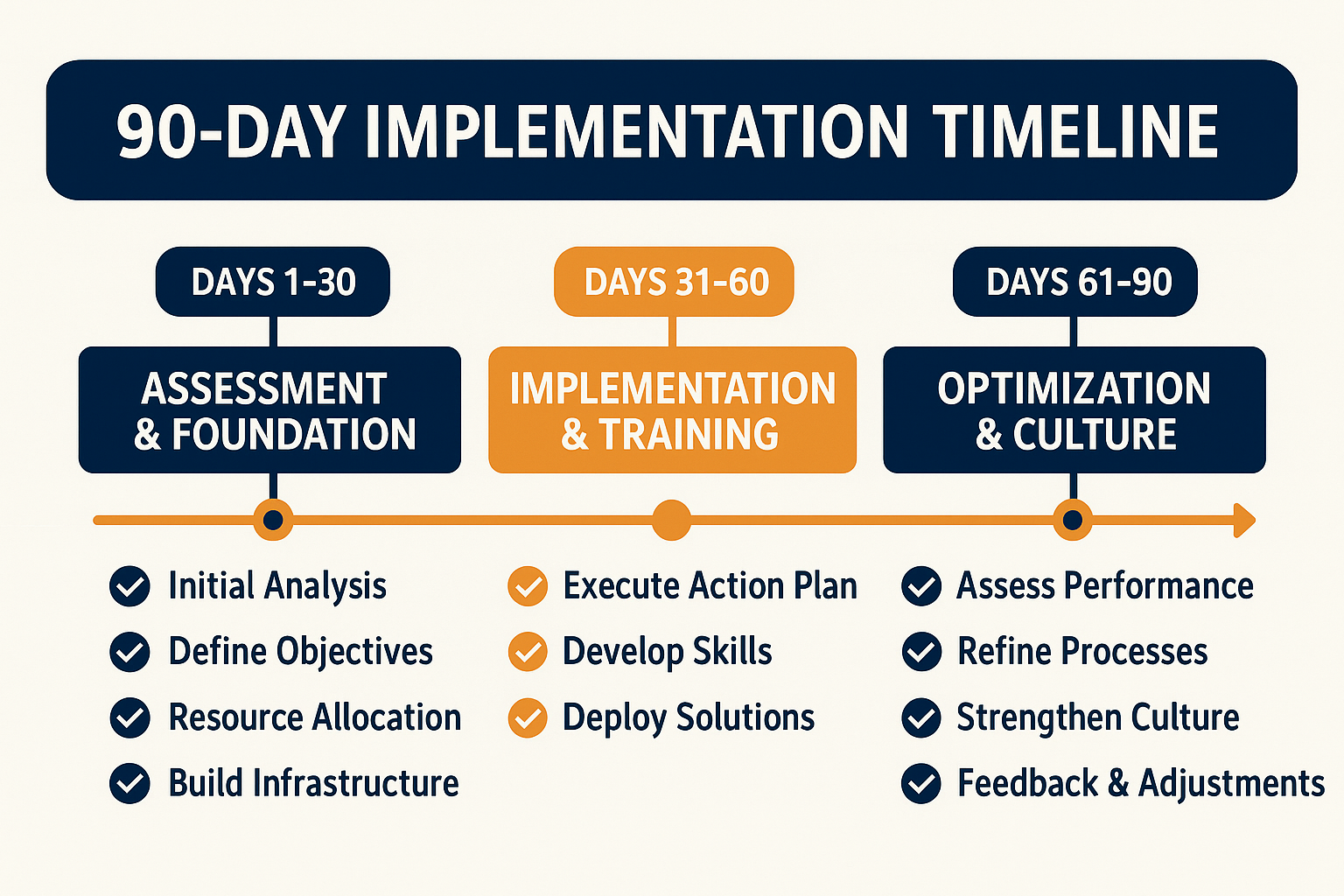
Your 90-Day Implementation Plan
Days 1-30: Assessment and Foundation
Week 1-2: Current state analysis
– Audit existing security training and policies
– Survey employees about current security practices and concerns
– Review recent security incidents and near-misses
– Assess technical security controls and gaps
Week 3-4: Policy development
– Draft new verification protocols for sensitive requests
– Create clear escalation procedures for suspicious communications
– Develop no-blame reporting policies
– Establish metrics for measuring security culture improvement
Days 31-60: Implementation and Training
Week 5-6: Technical improvements
– Implement or upgrade email filtering and authentication
– Deploy user-friendly security tools (reporting buttons, link scanners)
– Create mobile-specific security measures
– Set up monitoring and alerting systems
Week 7-8: Initial training rollout
– Launch role-specific security awareness training
– Begin regular communication about security topics
– Start positive reinforcement programs for security-conscious behavior
– Conduct first round of educational phishing simulations
Days 61-90: Optimization and Culture Building
Week 9-10: Feedback and adjustment
– Gather employee feedback on new policies and training
– Analyze initial simulation and reporting results
– Adjust procedures based on real-world usage
– Refine training content based on observed needs
Week 11-12: Culture reinforcement
– Celebrate early wins and positive security behaviors
– Share success stories and lessons learned
– Begin planning for ongoing security awareness activities
– Establish regular review and improvement cycles
Advanced Strategies for Sophisticated Threats
As your basic security posture improves, you’ll need to address more sophisticated attacks that target specific individuals or exploit detailed knowledge of your organization.
Defending Against Spear Phishing
The challenge: Highly targeted attacks that use specific information about your company, employees, and business relationships.
Advanced defenses:
– Information minimization: Limit publicly available information about your organization and employees
– Social media awareness: Train employees about how their online presence can be used against them
– Vendor communication protocols: Establish secure channels for sensitive business communications
– Executive protection: Implement enhanced security measures for high-value targets
Combating Business Email Compromise (BEC)
The challenge: Sophisticated attacks that impersonate executives or trusted business partners to authorize fraudulent transactions.
Specialized protections:
– Multi-channel verification: Require voice or in-person confirmation for financial requests above certain thresholds
– Time delays: Implement waiting periods for unusual or large transactions
– Behavioral analysis: Use technology that can identify unusual communication patterns
– Financial controls: Separate authorization and execution of sensitive financial operations
Measuring Long-Term Success
Quantitative Metrics
Security incident tracking:
– Number of reported phishing attempts (higher is often better)
– Time to detection and response for security incidents
– Percentage of employees who complete ongoing security training
– Reduction in successful phishing attacks over time
Business impact measures:
– Decreased security-related downtime
– Reduced security incident response costs
– Improved customer and partner confidence scores
– Enhanced regulatory compliance ratings
Qualitative Indicators
Cultural assessment:
– Employee comfort level with asking security questions
– Management support for security initiatives
– Integration of security considerations into business planning
– Proactive security behavior rather than reactive compliance
Behavioral observations:
– Employees naturally verify suspicious requests
– Spontaneous sharing of security concerns and threats
– Security-conscious decision-making in daily operations
– Peer-to-peer security education and support
🎯 Phishing Risk Assessment Tool
Evaluate your organization’s vulnerability to phishing attacks
Recommended Actions:
Key Takeaways
Human psychology, not lack of intelligence, drives most phishing clicks through urgency, authority, and trust manipulation
Traditional security training fails because it focuses on technical details rather than real-world scenarios and emotional triggers
Context switching and workplace stress make even cybersecurity-aware employees vulnerable to sophisticated attacks
Multi-layered defense strategies combining technology, psychology-based training, and clear protocols are most effective
Regular simulated phishing exercises with immediate feedback create lasting behavioral changes better than annual training sessions
Conclusion
The real reason your employees click on phishing emails isn’t stupidity it’s human nature. Attackers have become sophisticated at exploiting basic psychological principles like authority bias, urgency, and trust. Traditional security training fails because it fights against these natural tendencies instead of working with them.
The solution isn’t to expect your employees to become cybersecurity experts. Instead, you need to:
-
Create systems that account for human psychology rather than expecting people to overcome it
-
Build a culture where security awareness is rewarded, not where mistakes are punished
-
Implement verification protocols that make it easy to pause and verify suspicious requests
-
Provide context-specific training that reflects real-world scenarios your employees face
-
Use technology as a safety net, not as a replacement for human judgment
Remember, your employees want to protect the organization; they just need the right tools, training, and culture to do it effectively. When you stop treating phishing clicks as personal failures and start addressing them as systematic challenges, you’ll build defenses that work.
The cost of getting this wrong continues to climb, but the benefits of getting it right extend far beyond avoided losses. Organizations with strong security cultures attract better talent, earn customer trust, and can innovate faster because they’re not constantly dealing with security incidents.
Your next step? Start with an honest assessment of your current security culture. Are your employees comfortable reporting suspicious emails? Do they have clear protocols for verifying unusual requests? Are they afraid of making security mistakes, or empowered to help identify threats?
The answers to these questions will tell you everything you need to know about whether you’re truly protected or just going through the motions of security theater.
Call us today or book a time with our team to assess your security posture and implement the psychology-based strategies outlined in this article, the same ones that have helped hundreds of businesses reduce phishing vulnerability while building stronger, more security-conscious cultures. The question isn’t whether you can afford to implement these changes; it’s whether you can afford not to.
Also, check out our latest article: [5 Reasons to Outsource IT Support Beyond Cost Savings] for more insights on how the right IT strategy can strengthen your business from every angle.

Dmitriy Teplinskiy
I have worked in the IT industry for 15+ years. During this time I have consulted clients in accounting and finance, manufacturing, automotive and boating, retail and everything in between. My background is in Networking and Cybersecurity



